A city's electricity and oil production are knocked out, and a container falls onto a barge — PHDays 10 has concluded
5/24/2021
The reviews of the jubilee PHDays 10 are in, and attendees are calling it dazzling and invigorating, much like the weather in mid-May. Nothing was out of place on-site: jackets, T-shirts, and even the Russian minister of digital development were spotted. This was much more just than a gathering of over 2,500 information security specialists who had grown tired of being isolated during the pandemic. More than 20,000 people in different countries logged on to watch the forum and the action at The Standoff, the world's largest cyber-range. We talked candidly about important topics, brand-new technologies and approaches, geopolitical issues, business headaches, investor hopes, and troubles encountered by private users. We demonstrated how hackers are able to cripple the modern city, and we presented a methodology to protect against such damage that is nothing short of revolutionary.

Although the defender teams were experienced, the attackers dealt severe blows to all the companies in the city created on The Standoff cyber-range. As a result, on the last day of the exercises, the city residents had no electricity. The attackers disconnected the power lines after hacking into the relay protection and automation devices at a substation owned by Tube. A container fell onto a barge at the Heavy Ship Logistics seaport. It was revealed that hackers from the Invuls team had taken control of the gantry crane and issued deliberately wrong commands. In addition, attackers from Codeby and True0xA3 stopped the automated control system of Nuft, a large regional corporation in the petroleum production and refining business, and tampered with instrument data. Oil production plummeted by 90% in one day.
Ultimately, the attacks affected the gas distribution plant, thermal power plant, oil rigs, wind turbines, electrical substations, railroad facilities, airport, seaport, stores, network of advertising video screens, street lighting system, and offices of 25 Hours, Heavy Ship Logistics, Nuft, and Tube. Business risks were triggered most often at Heavy Ship Logistics and FairMarket: 33 and 26 times respectively.
During the four days when the cyber-range operated, 33 unique business risks were triggered—that was 54% of the total number of risks listed in the competition program. The attacker teams submitted to the jury a total of 84 reports of successful task completion. The red team winners were True0xA3 (35,877 points), Codeby (30,183), and Invuls (17,643).
The defender teams sent 328 reports of detected incidents. Based on the number of reports of attacks, the top three teams were Jet Security Team (Tube), akPots_team (Nuft), and Yourshellnotpass (25 Hours). Over the course of the competition, the defenders investigated 18 triggered business risks, and Jet Security Team and Yourshellnotpass investigated all the risks triggered in their companies. On average, using all the necessary collected information, it took around five hours to investigate the incidents.
After the awards ceremony, Vladimir Zapolyansky, Director for Marketing and Corporate Communications, Positive Technologies, spoke with the defenders from Yourshellnotpass and Jet Security Team. The team members said that unlike last time, this year they were able to pay more attention to defense and investigation. In addition, they used the hacks and tooltips the attackers themselves created. It took Yourshellnotpass 19 hours and Jet Security Team 12 hours to investigate the first incident.
You can read more about the cyber-competition in the special publication dedicated to the initial results of the cyber-range, and we'll tell you about the interesting people who gave talks on the last day of PHDays 10.
The reality of cybersecurity

The modern minister is coffee in a glass, running shoes, and a good sense of humor. A different kind of person probably wouldn't have been able to run the ministry that has helped make Russia a leader in developing digital government services—and it is worth noting that Russia's Government Services regularly win international awards.
The last day of the forum included a plenary session, "The reality of Russian cybersecurity."
The speakers were:
- Maksut Shadaev, Minister of Digital Development of Communications and Mass Media of the Russian Federation
- Vitaly Lyutikov, Deputy Director, FSTEC of Russia
- Alexander Muranov, Deputy Chairman of the Board, Gazprombank
- Aidar Guzairov, CEO of Innostage
- Vladimir Sakovich, Head of Skolkovo Ventures
"I think the environment in which we find ourselves is clear to everyone: the pace of digitalization has increased dramatically, partly owing to the pandemic," said Maksut Shadaev. "Russia is launching a large number of digitalization projects in all sectors, including in healthcare and education. The fastest growing sector is public services. COVID-19 pandemic has shown that all services can be obtained online, so these services are developing very quickly. The rapid penetration of digitalization dramatically exacerbates all the cybersecurity risks. Now there are discussions in the government, in the Administration, and in the Security Council, the main idea of which is that new cybersecurity challenges require new solutions. Our Prime Minister likes to say that we can't expect a new result using the old methods. I think that in the summer, we will develop a set of mobilization and incentive measures in order to be able to respond to new risks."
The main question put to the speakers by the session moderator, Positive Technologies CEO Yury Maksimov, addressed Russia's prospects for becoming a leader on the global information security market. "If you look at the economics of the Russian industry, you'll realize that about 50% of the funds invested in cybersecurity in Russia are spent on Western products, primarily American ones. How can we shift to Russian solutions, or force or persuade people to use them?" Yury Maksimov asked.
Alexander Muranov, Deputy Chairman of the Board of Gazprombank, offered the example of software in the banking industry.
"If you look at retail banking, you will find almost no foreign products there," Alexander Muranov said. "All major banks have their own teams that write code day and night, working remotely or in other formats. In the last two years, retail banking has completely changed in terms of software. The imported systems, Indian and American, have left the banks, and only the Russian ones have remained. Many products are open-source; however, Russia has created its own retail product industry. Infosec is on the verge of making the same decisions." In response to the question about completely replacing foreign information security products with Russian ones, Alexander said that to him, the ideal format is a trusted execution environment with separate "untrusted" products. "You shouldn't see enemies in all companies, but you need to have the option to manage the enemy, understanding what's happening with the "untrusted" solutions. It's worse when the whole environment is untrusted—that's a disaster."

"Until universities start to organize stands, lab sessions, and workshops based on Russian, rather than foreign, solutions, nothing will change. When young specialists graduate from university, they are aware of some foreign vendor, but have no idea about our domestic solutions," said Vitaly Lyutikov, Deputy Director, FSTEC of Russia. "Fortunately, there has been some development in this area. With the support of the Ministry of Digital Development, we are working over the issues of establishing technological training centers on the basis of the Academic Methodological Association, and we hope that this will help a little. Infosec service customers are another issue. They must understand that their task should be to ensure security, not to simply meet the requirements. All the requirements of such regulators as FSTEC and Federal Security Service pursue one goal—genuine security. And quite often, it is customers that create this ill-reputed "security on paper," when they do not care about the method of solving the problem. The only thing they are concerned about is how to make inspection authorities stop bothering them. If the customers do not want to build an information security system to achieve the goal, then we will strain every nerve, but still will not solve this problem, because this creates unfair competition between developers. It is always easier to offer just any solution than a high-quality one. The third problem is the developers themselves. If you analyze the competitions foreign vendors are winning, you see that these vendors take the lead in requirements related not so much to security as to interface ergonomics and user friendliness. This is also important, and Russian vendors need to pay more attention to it."

"Prohibition of foreign solutions must be approached very carefully. If the risks are big, such solutions should be forbidden. Where there is little risk, we need to persuade companies to switch to domestic software, while creating a truly competitive environment," Lyutikov added.
"We always have two extremes, we either allow everything or forbid everything. The government should stimulate the emergence of products to replace imported solutions, using various mechanisms of government support. But this is a long and methodical undertaking," Maksut Shadayev commented on the situation in the information security industry.
Answering Yuri Maksimov's question about why the cybersecurity market in Russia is so narrow and the number of startups small, Vladimir Sakovich, the Head of Skolkovo Ventures, noted that this industry around the world is usually divided between large players who can provide end-to-end coverage and reliability.

"Usually we find out about new startups when they are acquired by major companies such as Cisco," said Vladimir Sakovich. "Last year, large companies from around the world spent about $25 billion on the purchase of startups. In Russia, this figure hovers around zero, and such transactions are often carried out not for money, but, for example, in exchange for market access. When young startups do not see the steps that they should take to increase their value, they lose the motivation to grow. But most importantly, there is no motivation for investors who have to invest money in startups at an early stage in order to sell them later for a large amount. Thus small players find themselves without funding, and they don't have the means to grow until they break even. Even large companies in the information security field have problems with funding. Traditional methods of obtaining funds through borrowing on the stock exchange and large private equity funds are complicated by the negative geopolitics ambiance and the lack of stock exchange instruments."
Shortage of capital and the required investment instruments leads to the following: even if startups in the field of information security appear, they continue being small businesses for years.
"Every year, 10–15 startups come to Skolkovo, but most of them remain at the level of ideas; they fail to interest investors and move further along the investment cycle. To rectify the situation, the state should help stimulate private funds. The second challenge that must be addressed is the makeover of the non-market order distribution system. This will lead to an increase in revenue and somehow whet the investors' interest. And the third challenge is to create an investment infrastructure for the later stages, similar to an IPO, since, unfortunately, entering an IPO in the field of cybersecurity has become more difficult.. I think this is the task for three or five major banks," says Vladimir Sakovich.
Maksut Shadayev agrees that startups should be given the green light and some mechanisms should be streamlined. "Startups should be able to sell their products to government agencies without competitive bidding. If the customer is a business entity, tax benefits should be allowed. Until we lower the market entry barriers for startups, we can shower any developments with money as we please, but without access to the market it is pointless," said Maksut Shadayev.
Vitaly Lyutikov, Deputy Director, FSTEC of Russia, warned against blind faith in startups. He brought up an example of a company with just 6 developers creating an operating system.
"What if these developers scatter after a while and the product is left without support? We must help startups, but the mechanism must be thought out in order to eliminate risks at least in the core industries," said Vitaly Lyutikov.
Aidar Guzairov, CEO of Innostage, believes that if the information security industry in Russia unites and builds a roadmap, then the issue of a complete transition to domestic products will be resolved in under three years. "But the industry is not only about solution manufacturers and customers, it is also about training developers and specialists who work with end solutions and personnel retention in Russia. It should be understood that a developer, even one living in Ulyanovsk, does not need to leave, they can work well for vendors from the United States," said Aidar Guzairov.
Yuri Maksimov raised the issue of unacceptable damage to companies and the need to involve company management in the information security process. "Crime is changing its form: earlier, criminals stole money, and now they are beginning to blackmail, as it is much easier. In order to steal money from a bank, it is necessary not only to hire a hacker, but also to use droppers, carders, who come into close contact with the bank. An extortionist may sit in Bali and bring down an entire company all by himself. There was news that Japan, after the incident with the Colonial Pipeline, announced its desire to switch to local technologies, even in private companies. This is a serious problem for many countries—some states are starting to close their cybersecurity. As for large companies, until the top management gets involved in cybersecurity, it will not be able to give the results that the first persons really need," said Yuri Maksimov.
"Unfortunately, executives often deal with information security only once a year, while negotiating the budgets," said Aidar Guzairov. "Management of this level should ask their CISO regularly, what the company should do so that it is not destroyed by hackers and they can have the peace of mind. But these questions do not get asked."
Maksut Shadayev agrees with him: "In large companies, an information security manager often simply does not have access to the first person. As a result, the IS manager better understands the FSTEC regulations than the specifics of the protected business. Although, when the legislation on critical infrastructure protection was introduced, where criminal responsibility is spelled out, the top officials began paying a little more attention to information security," Maksut Shadayev noted.
At the end of the meeting, answering the question of whether the work is underway in Russia to create a hardware base on which all domestic IT solutions could function, Maksut Shadayev noted that the program for the development of production capacities and demand stimulation is under Prime Minister's personal direct control, and a meeting on this very subject was scheduled for Friday.
Artem Sychev: Russian banks are better protected
On the last day of the forum, much attention was paid to the issues of banking system security. Artem Sychev, First Deputy Director of Information Security Department, Bank of Russia says: "The banking system of the Russian Federation is head and shoulders above the Western ones in terms of information security. Our financial institutions have got a lot more experience in countering attacks and eliminating the consequences."
According to him, an important aspect is the understanding of information security risks at the management level of financial organizations, not just specialized units.
"If the management of a financial institution does not understand information security risks, does not even know what these risks are about, then in this case, not only the management is exposed to risks, but the shareholders and investors as well. It is extremely important for us to understand the extent to which cyberculture is present in the corporate management and whether it can affect the company's financial stability," says Artem Sychev.
"We are often accused of paying too much attention to technical issues in regulatory documents. On the one hand, they want us to say how it should be, and on the other hand, and on the other hand, they want us to give them more freedom," said Artem Sychev. "But ultimately, neither the technical details nor the safety features are the key. The key question for us is whether, should a crisis occur, a financial organization is able to ensure the business continuity and minimize losses."
The problem of crypto exchanges: an employee and the code
The situation is worse in the field of digital currencies. Vaagn Vardanyan, Senior Specialist at Banking Security, Positive Technologies, spoke about logical vulnerabilities that he had found on large cryptocurrency exchanges and that made it possible to manipulate the balance. He conducted the study in 2019–2020. Vaagn identified several reasons why exchanges are hacked: the dishonest insiders and the code vulnerabilities. In his research, Vaagn focused on logical vulnerabilities that are difficult to identify at the coding level.
How to protect older people from scammers

Let's move on from logical vulnerabilities to psychological ones. Vladimir Bengin, Director for Product Development, Positive Technologies, moderated the discussion on social responsibility and fraud prevention that took place at the "Why don't you ask us?" business section.
"We spend much of our resources on awareness," said Dmitry Gadar, Vice President, Director of the Information Security Department, Tinkoff. "For example, many materials about scammers are published in Tinkoff Journal; they are even on our TikTok. In addition, my team gives lectures at universities, and I personally give lectures at schools, about dangers on the Internet. We need to start this from school age and also help adults who are not prepared for the new threats. However, the topic is not that simple. If I worked in a telephone company, the management would hardly let me block the 30% of traffic generated by potential scammers just because we want world peace."
Vladimir Dryukov, Director of Solar JSOC, a center for countering cyberattacks at Rostelecom-Solar, did not believe there were so many colonies and illegal call centers that could generate such a volume of traffic, and noted that it is still important to inform the elderly about threats on popular sites like Sberbank or Gosuslugi.
"This is not a problem unique to us, and it has nothing to do with the Russian mentality," said Vladimir Dryukov. "The area we are lagging behind in is the movement of the state towards awareness. The United States has a separate Department of Homeland Security. They put great effort into making sure that information about new cybercriminals' tricks is publicized."
Social engineering in 2021
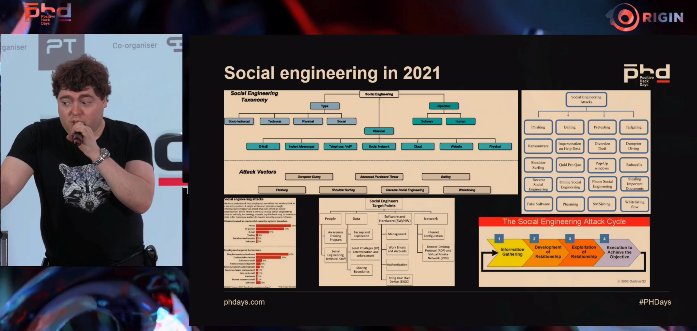
Information security specialist Dmitry Andreev spoke about the principles of social engineering and various application scenarios, illustrating his story with vivid real-life examples, and also sharing his experience in fighting this dangerous technique in companies.
"To protect against social engineering, you need to train employees, but you can't just blindly follow the rules," explained Andreev. "Without understanding how a psychological mastermind works, a person will be very vulnerable. It is necessary to show the attacker's logic by examples."
"Top management should understand why we are developing the company's information security; this should motivate them to learn, first of all, to fight off social engineering attacks. If this is not done, even a very good manager or administrator will become vulnerable," stressed Andreev.
How to avoid the unacceptable
Can a business be confident that it won't collapse from cyberattacks? Roman Chaplygin, Director for Business Consulting, Positive Technologies, addressed this question in his presentation, thereby continuing to show the public the company's next generation of solutions—products on the meta-level that make it possible for a single person to stop a cyberattack and protect the company.
"A business can only collapse when a major unacceptable event takes place. There are always emergencies that make it impossible to achieve operational and strategic goals and lead to a long-term disruption of core business. In particular, we have placed at the forefront of our concept events after which an organization will never return to its former activities and normalcy, and we believe that the security service's activities should be aimed at preventing such unacceptable events from ever materializing," stated Roman Chaplygin.

Discussing the list of unacceptable cyber-events Positive Technologies has compiled, he noted that the theft of money equivalent to 10–15% of net profit would be catastrophic for any company, regardless of the industry it's in.
"Practice has shown that the most effective and simple way to identify events that are unacceptable for a business is the individual training of top management, operational managers, and IT and information security specialists. For this reason we have identified, step-by-step, a list of implementation scenarios and systems that if hacked would result in unacceptable events", stated Roman.
Evgeny Gnedin, Head of Information Security Analytics, Positive Technologies, discussed how to make the unacceptable impossible, as well as the methodology of meta-products and immersion in processes.
"The list of unacceptable events is the first step in our methodology. The effectiveness of further work depends on how detailed and complete this list is. In order to stop an attacker in time, we need to understand how the unacceptable event is superimposed on the entire infrastructure of the company. So, by comparing the attack trajectories of different hackers, we saw on the resulting diagram a number of identical steps and systems involved. Therefore, we concluded that infrastructure has systems that require enhanced protection and monitoring. By learning to identify these systems and then vigorously defending them, we are one step closer to preventing an event that is unacceptable to business. And by providing enhanced monitoring of key systems and keeping them up to date, we will be able to stop intruders during the early stages of an attack," the speaker concluded.
Comprehensive and gentle scanning
The topic of new approaches to information security continued at thrEat reSearch Camp. In particular, Ilya Zuev, CISO, Rambler&Co and Okko, gave presentations. He shared his experience, noting that it is a daunting task to protect more than a hundred projects when the company has different groups of admins and developers. Rambler & Co has developed a comprehensive scanning system for protecting infrastructure and combating ransomware.
"The essence of our system is step-by-step scanning, which includes taking inventory, a quick scan, scanning services and software, DAST, compliance and expiration scanning, as well as scanning CI/CD containers, checking for corporate secrets published on public resources, a general filter of false positives by hash, notifying of detected vulnerabilities and displaying them visually, and, finally, coverage metrics. All scan results are collected in one place for processing, and we are already making decisions based on the results," said the expert.
Ilya also emphasized the importance of checking domain expiration dates, "People love creating websites on Tilda because it's easy and it looks good. However, a subscription to Tilda may expire unnoticed, and cybercriminals will take advantage—they steal such domains and place "bad" sites and unpleasant Javascripts there."

What we are dealing with, or a brief introduction to the information security environment if you have been in a coma for the past 10 years
Independent researcher Vladimir Dashchenko chose the topic of his speech "Retrospective analysis of significant security incidents for the last 10 years" for the PHDays forum, which is celebrating its tenth anniversary this year. He presented a brief exegesis of events that are connected with information security in one way or another, analyzed what impact they had on humanity, technologies, attacks, and protection methods, and answered the key question: has our attitude towards information changed today, when the risk of data leaks has significantly increased?
Vladimir noted that over the past decade there has been a phenomenal number of high-profile hackings, leaks, vulnerabilities, malware attacks, and other incidents.

"Since 2014, the world of the Internet of Things has been winning over more and more hearts: in North America, Google Glass, which previously could only be tested by Google employees, was made available to the general public for the first time. It started right off with the fappening—a massive hacking of celebrities on the iCloud, leaking their photos. From that moment on, the problem of information security began to affect even people who knew nothing about it: celebrities, actors, movie stars, and ordinary folks. At the same time, a huge number of micro-startups specializing in providing cybersecurity to individuals appeared in Western countries. If earlier, people hired bodyguards to provide physical protection, now there are security guards that provide digital protection." said Vladimir.
Ural OS security models

Speakers from the Ural Federal University, based on their experience working with domestic operating systems, talked about formal OS security models, their implementation, and problems of scanning and verification.
"To create a secure operating system, numerous modifications and architecture solutions must be added," says Liliya Galimzyanova, postgraduate student at the Ural Federal University. "We offer to extend a standard access control model. We'll think of files as memory areas loaded to the process space. It will be easier to make a specification for further verification and show the correlation between the model and the code."
The speakers also suggested making the access control model as versatile as possible so that it could be practically processor-independent. "Our main task is to define the conditions for security, whereas the actual realization is of secondary importance. We have to walk a thin line between the reality and mathematics or formal models," added Roman Gilmiyarov, postgraduate student at the Ural Federal University.
The game is never over
Artem Bachevsky, an independent cybersecurity researcher, drew attention to the security issues of video games while developing and automating AppSec processes. From the very beginning, Artem conceded that he is not a gamer, but he is interested in all things hackable. In his speech, Artem spoke about the most vulnerable genres of games (promo games, browser games), common vulnerabilities and attacks (insecure protocols, errors in the code, bots, and cheating) and how to protect against them. One such vulnerability causes a game to never end.
The forum and the cyber-range have come to an end, but news and detailed reports are already being prepared on these events. Follow us on PHDays, on The Standoff, and in social media. Thank you for being with us!
Innostage, the co-organizer of the forum, deployed and maintains infrastructure for The Standoff, and monitors and controls the actions of the teams. Rostelecom-Solar, a national provider of information security services and technologies, has become a business partner of the forum. PHDays technology partners are the Russian private chain of supermarkets Azbuka vkusa, IT-company Osnova, and the developer of remote banking service solutions iSimpleLab. The following companies are presented at PHDays: Axoft, Cross Technologies, ICL, OCS Distribution, R-Vision, Security Vision, and Jet Infosystems. The partner of the competition program is ARinteg.