Cyberbattle at PHDays, or How to hack city infrastructure in 30 hours
7/25/2018

For the third year running, the highlight of the hacking contests at Positive Hack Days is The Standoff, in which teams of attackers, defenders, and security operations centers (SOCs) do battle in a virtual city. Experience in 2016 and 2017 showed the appeal of this ultrarealistic format for both participants and visitors at PHDays. So there was no doubt among the organizers that The Standoff deserved to return this year. In 2018, a total of 19 teams took part in The Standoff, and for nearly 30 hours, these teams fought for control of the city.
The defenders stood fast, but the attackers still managed to pull off some hacks: according to the rules, some targets were deliberately left unprotected. Meanwhile, the battle among the attacker teams for first place was rather hot indeed—the scoreboard was turned nearly upside down just half an hour before the end of play. Read on for a blow-by-blow account of what happened during these two exciting days.
Day 1: Getting the lay of the digital land
Events were slow in coming on the first day. Attackers took their time reconnoitering and learning about the targets. As announced previously, the city's economy was based on digital technologies. City infrastructure included an electrical plant and substation, railroad, office buildings, energy-efficient smart homes, banks with ATMs and self-service kiosks, mobile communications, the Internet, and online services.

Physical mockup of the virtual city
Attackers could refer to an internal portal, which contained general information about city infrastructure and a list of high-level objectives. By completing tasks, the teams earned varying amounts of credits. Whichever team had the most credits at the end of the game, won.
The first attacks struck a bit before lunchtime, affecting city infrastructure including systems for controlling cameras, stoplights, and ventilation systems.
The Antichat team discovered vulnerabilities in cameras and performed a denial of service attack. At 11:20 a.m., the team obtained access to video surveillance systems and tried for two hours to knock them offline. Like in real life, some of the cameras had easy-to-guess passwords. The attackers were ultimately able to simply turn off some of the cameras and disable others by using publicly available exploits.
Then Antichat set its sights on heating systems. The team obtained access to the controller responsible for heating and ventilation, at which point they started turning the heat on and off again. The organizers awarded only partial bug bounty credit for this, since the task specified that the team needed to disable the ventilation and stoplight systems as well.
At noon, CAICA discovered vulnerabilities in ICS software but failed to seize this chance in time to penetrate target infrastructure.
At about the same time, a brief presentation was given on the main stage by the Rostelecom SOC, which had been monitoring an unprotected office (belonging to a fictional engineering company named Sputnik). The team stated that attackers had successfully used brute force and exploited vulnerabilities to hack the office network and obtain domain administrator privileges.
Around midday, CAICA reset the passwords of all subscribers of the telecom operator's portal. The team then tried to sell the reset accounts to a black-market buyer, who backed out after having doubts about whether the accounts were real. As soon as subscribers started complaining, the telecom operator restored accounts from a backup and closed the portal security hole. Then the attacker team tried to cash in the accounts for bug bounty credits, winning only a pittance for their efforts. This incident was not the result of defender negligence: the organizers had asked the defenders to temporarily disable the WAF for the portal in order to install updates and test new functionality. Naturally, attackers jumped at the opportunity.
The team of telecom defenders—You shall not pass—noted that hackers focused on the portal and web interfaces. Most of the telecom company's resources were under the watchful eyes of defenders, but some were left unprotected on purpose, as stipulated by the organizers. For example, the defenders were unable to defend against theft of accounts, password resets, and interception of text messages. Meanwhile, the ANGARA SOC team could only record these incidents, which worked to attackers' advantage. You shall not pass also told us of social engineering attempts: some attackers, presumably inspired by CAICA's successful gambit last year, posed as journalists to obtain data from the defenders. But the defenders did not take the bait.
Closer to evening, the attackers learned that the city had its own cryptocurrency. Attackers could earn extra credits by performing DDoS attacks involving the blockchain. CAICA was the first team to dip its toes in the cryptocurrency waters: around 6 p.m., they hacked a machine in order to mine with it.
At 9 p.m. it became known that CAICA had discovered a car based on its GPS coordinates. A bit later, CAICA and Sploit00n hacked telecom subscribers nearly simultaneously, as they intercepted text messages with compromising information about a top insurance executive. (As noted already, securing subscriber data was outside the remit of defender teams.) For this successfully completed task, the attackers received 250,000 credits each.
Towards day's end, unknown attackers tried to bruteforce SIP accounts online, but due to a timely change by the defenders to the Asterisk configuration, the attack was slowed down before its ultimate failure. It was evident that attackers were in a rush, judging by their botched effort to bruteforce non-existent phone numbers: one digit was missing, so instead of trying valid 10-digit numbers without country or city codes, they repeatedly entered 9-digit ones.
Jet Antifraud Team, responsible for protecting the bank, reported shortly thereafter that they had blocked five fraud attempts so far that day, worth a total of 140 credits. This was only a small preview of what was to come during the night.
After watching over events on the first day, the organizers remarked that the attackers seemed rather cautious and reluctant to even attempt any large-scale hacks. And when attackers did act, they did so in obvious and unsubtle ways. Many attacks were still stuck at an early stage by day's end, since the attackers did not know how to continue developing them. For example, after hacking the unprotected office of Sputnik, an engineering company, the attackers were slow to find its relationship to the industrial process segment. Nor did teams put hacked systems to use for mining cryptocurrency.
All the same, the first day saw around 100 bug bounty vulnerability reports, as well as numerous thefts of accounts and credit card information. These attacks were worth only a few credits each, but some of the teams were able to make up for this in volume (to the tune of 100,000 to 200,000 credits).
Based on experience in past years, defenders steeled themselves for attacks as night drew closer.
The night is dark and full of terrors

The Standoff in full swing
And sure enough, the excitement came at night. The sun set, hackers started to perk up, and vulnerabilities discovered earlier in the day now began to be put to use. Digital unrest struck several parts of the city right away.
Jet Antifraud Team detected mass attempts to steal money from residents' bank accounts. A total of 500 accounts were open at the bank, worth a total of 3 million credits. The attackers tried to cash out, or at least cycle the money between accounts and get a feel for the bank's anti-fraud systems. Three major attacks were recorded between 10 p.m. and 2 a.m., involving a total of around 20,000 attempted fraudulent transactions and 19 fraud-linked accounts. Although 100 legitimate accounts were compromised, the bank did not lose a single credit.
After midnight, True0xA3 decided to give CAICA some competition by hacking a computer to mine cryptocurrency. Each of the two teams assembled a small botnet for mining during the night.
Surprisingly, a ceasefire developed in the early morning hours. Defenders and attackers put aside their differences to jointly study the infrastructure of the industrial process segment. Industrial systems had changed substantially compared to the prior year's competition, and included a long list of equipment: hydroelectric plant, electric plant, substations, oil refinery, petroleum transport and storage facilities, railroad and automated warehouses, tanker loading facilities, building management systems (BMS), life support and video surveillance systems, and smart homes. Real software and hardware came from diverse vendors: ABB, Advantech, Belden, GE, ICONICS, ICP DAS, Kepware, Loxone, Matrikon, Moxa, Phoenix Contact, Prosoft, Rockwell, Schneider Electric, and Siemens. Software and firmware versions were specially chosen by the organizers to be representative of the vulnerabilities and configuration errors typically encountered in the wild.
When attempts to get remote access to ICS equipment failed, the attackers started to connect locally and—with defenders looking over their shoulder—scanned the network to learn its topology and exploited known vulnerabilities, while refraining from any full-fledged attacks.
Day 2: Expect the unexpected

Early on the second day, attackers conquered yet another office, this time belonging to the city's insurance company. Around 9:30 a.m., SCS obtained personal information of the insurer's clients. Team SRV (defenders) and Advanced Monitoring (SOC) reported that several services had been hacked. One Linux machine was subjected to a lengthy brute-force attack; with the help of an extra-large dictionary, SCS was finally able to crack the accounts. Then the attackers created a foothold on the system and, until they were stopped, tried to attack internal services while bypassing the NGFW. Around this time, SCS snapped up a mining computer that had been seized by CAICA, but the defenders quickly caught this and put a stop to mining. In just 24 hours, the WAF of the SRV defender team repulsed around 1,500,000 attacks. The Advanced Monitoring team logged 30 security incidents.
After lunch, SCS, EpicTeam, and Level 8 tried to earn 250,000 credits on the black market by selling compromising material from text messages regarding a top insurance executive, as two of the other teams had done on the previous day. But one of the teams could not provide proof that the correspondence in question in fact belonged to the executive (such information was not present in the stolen data), and therefore received only 100,000 credits. Another team obtained only part of the correspondence. The black-market buyer still paid for this information, but rather less than the team might have preferred—only 150,000 credits.
In the meantime, True0xA3 began making inroads in the energy sector and sending bug bounty reports of vulnerabilities. One exploit helped them in their attack, at 3:19 p.m., on an electrical substation: the team disabled a protection terminal, disrupting normal operations as a result.
The Jet Security Team defenders team and RT SOC informed in the afternoon that attackers had taken full control of the unprotected Sputnik office, and from there, found ways to access oil-related ICS systems. Attackers had tried and failed many times during the night to punch through, but now they had finally found a way to proceed. Sputnik had not secured its Wi-Fi network, which enabled attackers to obtain access. In addition, credentials for remote access via TeamViewer to the workstation of an ICS engineer were discovered. The attackers made use of this to seize control of the session. No serious attacks had yet been detected, but Jet Security Team and the RT SOC predicted bumpy times for the city's oil sector.
Events were not long in waiting. By the end of the day, an unknown team performed a local attack on tanker unloading systems: attackers walked up to the equipment and created (possibly by accident) a loop on the local network, which cut out communication with the PLC and SCADA simultaneously. This caused an oil spill on the tanker, but without serious consequences. Such attentive expert ICS protection (from total monitoring to reconfiguration of industrial network equipment) as shown by Jet Security Team is very rarely found in real life.
But the most interesting event came just an hour before the end of play. The city's anti-fraud system was disabled. Hack.ERS and invul:$ quickly moved to take advantage. But Hack.ERS was the first team to automate transactions, cleaning out the bank all by itself in just 20 minutes—making off with around 2.7 million credits. As a result, the team rocketed from tenth place to first place, pushing last year's winner CAICA off the top perch. In just 30 hours, Jet Antifraud Team defended the city bank by blocking 22,500 attempted fraudulent transactions worth 97,000 credits.
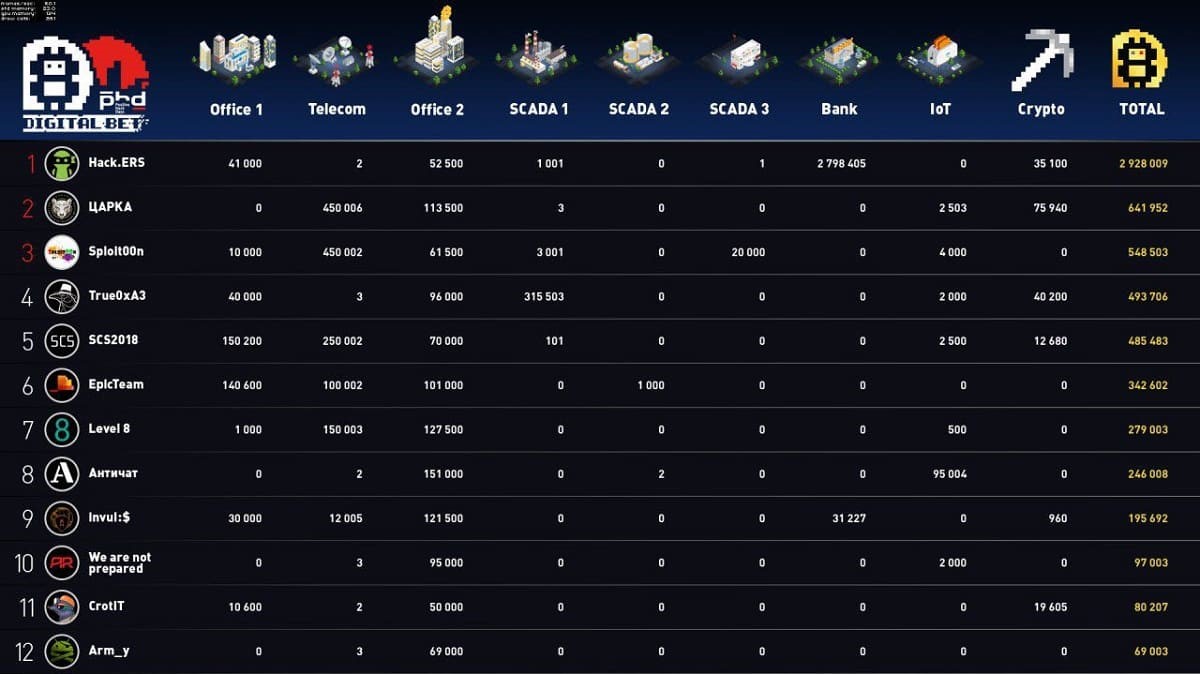
Final scoreboard
Action heated up on the cryptocurrency exchange as well. Out of 12 teams, 6 got busy mining: CAICA, True0xA3, Hack.ERS, SCS, CrotIT, and invul:$. As in real life, the value of the currency varied wildly from a low of 5 credits per block to as high as 200. The numbers changed dramatically during the last hour. A total of 1,776 blocks were mined: CAICA – 620, True0xA3 – 515, Hack.ERS – 355, SCS – 133, CrotIT – 104, and invul:$ – 48. Over the two days, the teams earned: CAICA – 75,940 credits, True0xA3 – 40,200 credits, Hack.ERS – 35,100 credits, SCS – 12,680 credits, CrotIT – 19,605 credits, and invul:$ – 960 credits.
In the closing minutes of the contest, True0xA3 caused a citywide blackout. This was the logical continuation of the team's actions leading up to this point: studying the stand, reading ICS security research, and finding the necessary utilities. Thanks to a vulnerability in the MMS protocol, they were able to cause a short circuit. (The same attack was also performed two years ago at PHDays VI.) The protection system should have been able to block this attempt, but True0xA3 had disabled it on the previous day. The railroad was not spared either: True0xA3 took control of the locomotive but did not have time to do anything with this. Sploit00n found several vulnerabilities in an automated railroad warehouse enabling changes to PLC logic, but the team ran out of time before attempting any modifications.

Model railroad
Positive Technologies products also monitored goings-on during the two days of action: MaxPatrol SIEM, PT Network Attack Discovery, and PT MultiScanner. PT Network Attack Discovery, for example, recorded 11,769,526 attacks. For more on the attacks and technical details of what was recorded by Positive Technologies solutions, stay tuned for our next article.
Everybody won: final thoughts
One could say that everyone was a winner this year. The 30 hours of cyberbattle at The Standoff once again proved that security professionals can provide excellent protection without impinging on business logic or industrial processes. Attackers were unable to hack protected targets, but they did demonstrate the consequences of neglecting security. Some targets and infrastructure were left totally undefended, as sometimes happens in real life, in order to make the competition more realistic and exciting. And to make sure that defenders did not abuse their position and unfairly tilt conditions in their favor (such as by turning off services to improve security), the organizers ran special programs to make sure that everything was online and accessible.
The first three places went to Hack.ERS, CAICA, and Sploit00n. For full results see the final scoreboard.

The Standoff champions: the Hack.ERS team
Ilya Karpov, ICS security expert and an organizer of the ICS stand, believes that the defenders won even though attackers made trouble at a substation. "Although the oil sector in The Standoff was plagued with deliberately planted vulnerabilities, configuration errors, access points, and even physical access, outstanding protection was provided by Jet Security Team. We did not see any sophisticated attack vectors involving logic changes this year: nobody made it as far as the controllers, since the defenders had things 100 percent under control. Still, True0xA3 among the attacker teams succeeded in figuring out how the substation works—their attack was the most sophisticated one we saw during the contest. For the second year now, we were expecting to see attacks on network equipment, since this is what gets targeted in real life, but attackers have been neglecting such techniques so far."
Mikhail Pomzov, member of the PHDays organizing committee, says that the attackers could have accomplished more: "All hacker tasks this year were based on logic. There were hidden objectives that were unlocked by certain actions or events. For instance, getting access to an account on one portal could enable sneaking onto other network segments. But attackers used very straightforward approaches and did not go the extra mile. They simply completed tasks and got their credits. Maybe they just did not have enough time."
Mikhail Levin, member of the PHDays organizing committee, weighed in as well: "Every year, the purpose in our holding the event is to focus attention on information security and demonstrate the attack scenarios that exist, as well as ways of counteracting them. I think that we succeeded this year. How can we not recall that critical point in the game when attackers and defenders came together to better understand the industrial process segment of our digital city and how industrial systems work in general. After all, the participants are security pros in real life, who build protection systems, resist attacks, and investigate incidents on a daily basis. And to better protect industrial systems in practice, they have to figure out how these systems function. Here at The Standoff, they had the opportunity to exchange experience and master the latest techniques and penetration testing tools in conditions that mimic real ones as closely as possible."

Defender teams