Day 1 of PHDays: How to create a botnet, hack Telegram, and survive ransomware
5/24/2017
The Joy of Tech webcomic about the Internet of Ransomware Things—with dishwashers mining bitcoins and coffee machines threatening to brew only decaf unless paid—is both funny and a sign of the times. Considering the Internet's increasing reach into our offices and homes, the theme of the Positive Hack Days forum this year is "The Standoff: Enemy Inside." The seventh annual PHDays international digital security forum opened today, drawing over 4,000 participants from all over the world, who contributed and took part in talks, hands-on labs, roundtables, and hacking contests. Experts showed the finer points of ransomware infection, created an experimental router botnet, demonstrated the process of hacking electrical infrastructure and WhatsApp accounts, and looked at techniques for intercepting phone calls and text messages.

Mass infections of Russian government organizations in May 2016 provided fodder for discussion of corporate infrastructure and its security. According to Positive Technologies research, a hacker with minimal knowledge could penetrate the network perimeter in 55 percent of cases, and on 76 percent of corporate systems an attacker could obtain full control of one or more critical resources. Equally frightening is the fact that the average age of the oldest uninstalled system updates is over six years—something needs to be done. Key factors for ensuring security at companies and organizations of all stripes were the centerpiece of the PHDays plenary session "Information security today: the splendor and misery of corporate security." Discussion was led by Boris Simis, Deputy CEO for Business Development at Positive Technologies.
Sergey Lebed (Director of the Information Security Service of Sberbank) related an anecdote from April 14, when the hacker group Shadow Brokers made public the modules used to create such malware as WannaCry. Sergey was speaking at a conference. "I asked my colleagues how their weekend had been, because we had been working around the clock to understand these modules and prepare recommendations for our team. But many of the security experts there hadn't even heard the news! Sometimes security specialists live completely cut off from the practical side of security."
Timur Yunusov, Head of the Banking Systems Security Unit at Positive Technologies, shared his own experience. "The recent story of hackers intercepting one-time bank passwords sent via SS7 should not come as a surprise. We have spent two years showing telecom companies that this could happen, but complacency ruled the day."
Sergey Gordeychuk (Kaspersky Lab) said that "knowing one's perimeter is basically impossible." The larger a company is, the harder it is for defenders to cover everything. But it is not fair to leave all responsibility to the users. "Everyone has to realize that citizens are not able to ensure their own security, whether in the physical world or the digital one. Card fraud has to be the responsibility of banks, and protecting an e-government and its users must be the duty of that government."
Avoiding tears with WannaCry
Andrey Dugin, Head of Information Security at MTS, spoke on "SOC in a large corporate network: challenge accepted." He laid out the mobile provider's stages of building a security operations center, which has existed since 2005 but became much larger and more active in the 2010–2015 period. Forum visitors learned about the technologies used, staff, and workflows. MTS has been refining its technologies and processes for the last two years, while security staffing has increased from 8х5 to 24х7. Naturally, the recent news of WannaCry was not left out of the discussion. Andrey shared one example of when the SOC team successfully repelled an attack. MTS has invested heavily in a proactive stance with patch management, backups, user education, and monitoring of security events both at the system log level and in the world at large.
SOC-related discussion was picked up at "SOC Evolution 2017," where Oleg Bakshinsky (IBM), Alexander Lesnikov (Sberbank), Alexey Novikov (Positive Technologies), Arkady Prokudin and Alexey Shabanov (SAP), Elman Beybutov (IBM), Alexander Bondarenko (R-Vision), Vladimir Dryukov (Solar Security), Dmitry Pudov (ANGARA), Vladimir Shadrin (Rostelecom), and Sergey Soldatov (Kaspersky Lab) shared their experience building operating centers for monitoring and reacting to cybersecurity incidents.
Botnet growth medium
It's important to realize that the Internet of Things doesn't only mean using your smartphone to brew a cup of coffee in the morning. The IoT is already important in healthcare, for example. Even pacemakers are potentially vulnerable to hackers. The dark side of the IoT and the importance of security in this area were emphasized by Positive Technologies experts during a press briefing, where they demonstrated attacks against various devices. Statistics from Positive Technologies show that there are over 3.5 million vulnerable cameras worldwide. Accessing the video from a camera of an individual user requires just 60 seconds, two search requests on Shodan, and one search request on Google. What's more, over 90 percent of all surveillance cameras used in corporate environments contain critical vulnerabilities. Home routers are an equally welcoming environment for hackers. Passwords for approximately 15 of 100 such devices have never been changed from the default values. And having just the five most popular user name/password pairs (the top three are admin:admin, support:support, and admin:0000) is enough to gain administrative control over one in ten routers.
IoT security has rocketed to the top of concerns primarily because of the fear of DDoS attacks. Massive armies of infected devices have already been used to strike Spotify, Twitter, Github, and PayPal. By commandeering sufficiently large numbers of "smart" thermostats and video cameras, hackers have knocked Internet giants offline. Artem Gavrichenko, QRator Labs CTO, explained how the DDoS situation changed so drastically in just one year and what new approaches are being invented to cope. Speaking of the necessary safety margin for infrastructure in seismically active areas, he mentioned the instructive example of a Japanese engineer, who worked at a nuclear power plant that was located closer than Fukushima to the epicenter of the infamous tsunami. He personally insisted on building a barrier 14 meters high although according to standards, 12 meters was sufficient. As a result, when the 13-meter tsunami struck his nuclear plant, disaster was averted—unlike at Fukushima.
Discussion about the Internet of Things was continued at "IoT (in)security," which was moderated by security expert Alexey Lukatsky. The topic of attackers' motivations was touched on. According to Pavel Novikov, Director of the Telecommunication Systems Research Group at Positive Technologies, attackers will soon have more than just "laughs and giggles" to inspire their destructive work. "In the early 2000s, worms would destroy hard drives but they did not spread very far since the attackers did not have any strategy for monetization. But recently for example there were problems with the service of a certain mobile operator, which caused many traffic toll barriers to stop working—these days, such devices are often controlled by mobile signal. So what happens if smart city systems really take off and something similar happens with traffic lights? Demanding ransom will be the simple and obvious way for attackers to make money."
Router armies
In order to thwart botnet creators, security experts have to think like the enemy. The enemy has to jump through a number of hoops: finding Internet traffic, preparing the infrastructure for exploits and a dropzone, renting bulletproof hosting, encrypting a malicious binary file to evade antivirus defenses, creating management protocols, and running C2 while constantly hiding behind a web of VPNs, SSH encryption, and proxies. Some botnet creators have found clever ways to expedite this process, as scrutinized by Maxim Goncharov and Ilya Nesterov in their talk "Live dissection: anatomy of a router-based botnet."
"Botnet creators can't find enough routers that can be easily reprogrammed," the researchers said. "It's hard to write code for most routers—you have to know the versions of Linux and various libraries involved. So in the situation involving 5 million Deutsche Telekom routers, the attackers failed to overwrite the router firmware. This meant that a router could be restored to normal by simply unplugging it and waiting 30 seconds. But on the other hand there are devices such as OpenWRT from Netgear for which writing firmware is a relative breeze."

Battening down the hatches against ransomware
The warning bells about ransomware were sounded a year and a half ago by analysts from Palo Alto Networks, IBM X-Force, Trend Micro, and other companies. Now that WannaCry has infected hundreds of thousands of computers in over 150 countries, Mona Arkhipova's presentation "Ransomware incidents forensics" is especially timely. As the Director for Information Security Monitoring and Architecture at Acronis, she recreated the process of Osiris infection of an endpoint PC step by step, showing in stark relief the weak links in protection. Mona's advice for organizations was to regularly check the state of antivirus, DLP, and other protection; test backups; and keep spare workstations on hand for critical users.
MacBook hacking
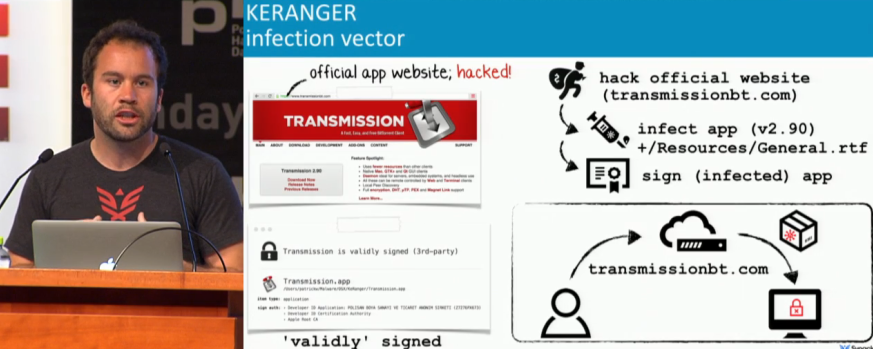
While Windows users regularly lose sleep due to security issues, Apple fans cannot afford to be complacent either. Ex-NSA and NASA employee Patrick Wardle took the stage in Moscow with an overview of new malware targeting macOS. The talk included discussion of properties, infection vectors, and persistence mechanisms for Mac malware. Wardle presented generic detection methods that help to ensure the security of macOS. "You shouldn't fall for Apple's marketing claims that their systems are the best protected," Patrick advised. The first ransomware on macOS, keranger, was analyzed in detail. Hackers used a web vulnerability on the site of Transmission, a popular free torrent client, and added malicious code to the application download. The malicious version was present for several hours late at night on the developer's official site. Users who happened to download Transmission during that time were struck by ransomware, which demanded one bitcoin in return for not blocking all files on the user's hard drive. Patrick also mentioned several cases in which third-party software could be exploited. For example, if an attacker already has a foothold on a system, an old version of Mac firewall Little Snitch could be installed remotely in order to escalate privileges. Little Snitch has the necessary certificate and vulnerability that an attacker could abuse to perform operations at the kernel level.
Hacking WhatsApp and Telegram accounts
Accessing big-time corporate secrets is sometimes just a matter of hacking employee accounts on popular multiplatform instant messenger services, which are increasingly used for corporate chat. Check Point researcher Roman Zaikin detailed an interesting vulnerability in WhatsApp and Telegram. By sending a seemingly harmless file that contains malicious code, an attacker can read all of a user's old chats and view new messages, get the user's contact list, and view all exchanged videos and photos. "The end-to-end encryption used in today's chat platforms looks gorgeous. Only the sender and recipient have keys," he explained. "On the WhatsApp site, the company says that they themselves cannot see your correspondence. But why should an attacker try to break end-to-end encryption if they can instead use it to their advantage? We can fly under the radar. In the list of allowable files (DOC_MIMES) on the WhatsApp web interface at web.whatsapp.com, it's possible to add Text/HTML files. Then any file, including JavaScript, can be sent to the victim. The victim clicks the file, which steals their information and launches WhatsApp in our browser. Then the information received by WhatsApp on the victim's phone is also received by the attacker in the browser. Against potential victims who are security-wise and click-weary, the researchers created an image/HTML file hybrid that can be sent to a group chat.
The Standoff
Positive Hack Days is more than just discussions, talks, and hands-on labs. Adrenaline races at The Standoff, an attackers-versus-defenders battle in near-real-world conditions. The battleground is a virtual city made to resemble a real megapolis rich with offices, telecom operators, banks, power stations, and IoT devices. One of the attacking teams, TSARKA, leapt into first place by the end of the day. The group of hackers from Kazakhstan was able to intercept text messages of the city's mayor. This secret correspondence contained some truly scandalous material, instantly enriching the TSARKA team by 150,000 credits. Their method of attack remains unknown—could the hackers have really smuggled in a fake mobile base station?
The other attacking teams with non-zero results—BIZone, Antichat, Vulners, Rdot.org, and Hack.ERS—for the time being are racking up their scores by digging through the city’s digital infrastructure for email accounts and credit card numbers. But the compensation for these finds is rather less, at 100 to 500 credits each.
Those fancying themselves a modern-day Jessie James competed in $natch, a contest organized with the support of ARinteg and QIWI. Attackers helped themselves to virtual money (convertible to real winnings) from a full-fledged financial infrastructure encompassing banks, ATMs, self-service kiosks, and online stores. And like in the real world, mobile networks are one source of vulnerabilities that can be used to grab cash.
The forum will continue on May 24. Don't forget to follow all the latest from PHDays VII on Twitter and Facebook! Watch the forum live online at www.phdays.com.
See the PHDays VII full schedule on the forum's official website.
Positive Hack Days Business Partner: MONT
Forum Partners: Rostelecom, R-Vision, Kaspersky Lab, IBM, Microsoft, Solar Security, InfoTeCS, and SAP
Forum Sponsors: Axoft, Web Control, ANGARA, Check Point, McAfee, and Symantec
The Standoff Partners: Palo Alto Networks, ICL System Technologies, and Beyond Security
The Standoff Participants: Infosec, Advanced Monitoring, Jet Infosystems, and CROC
Technology Partners: Cisco, CompTek, Acronis, Synack, ARinteg, Qrator Labs, Wallarm, Zecrion, Aktiv, QIWI, PROSOFT, and Advantech
Premier Media Partner: TASS