Day 2 of PHDays 8: Games Over (until next year)
5/21/2018
The eighth annual Positive Hack Days has wrapped up. Over 5,200 participants gathered in Moscow to watch hackers intercept mobile signals, take cash from an ATM, fool smart utility meters (one of the hackers was 12 years old!), and pull off dozens of other technical feats. True drama was in the air during the finale of the attacker-versus-defender showdown at The Standoff.

Cyberbattle royale
After a long 30 hours, The Standoff is over. Looking at the results of the two-day struggle between attackers and defenders, one could say "they gave peace a chance," since attacker teams succeeded primarily in hacking unprotected targets. However, competition between the attacker teams was intense: the scoreboard changed dramatically due to fast-moving developments in the last hour of the game.
The first day was slow going, with only a handful of events. By day's end, one of the attacker teams hacked an unprotected office, as reported by the Rostelecom SOC. City infrastructure was hit as well: attackers found vulnerabilities in cameras and performed denial of service. One attacker managed to tinker with heating systems. Throughout the day, attackers reported bug bounty vulnerabilities and bank card details to the organizers (in return for in-game compensation).
As expected, things really heated up during the night. Jet Antifraud Team, responsible for protecting the bank, recorded a mass attack intended to steal money from the accounts of city residents. During the daytime, there were only five attempts, worth a total of 140 credits. In the evening and nighttime hours, three large-scale attacks involved a total of around 20,000 attempts to fraudulently transfer funds to 19 external accounts.
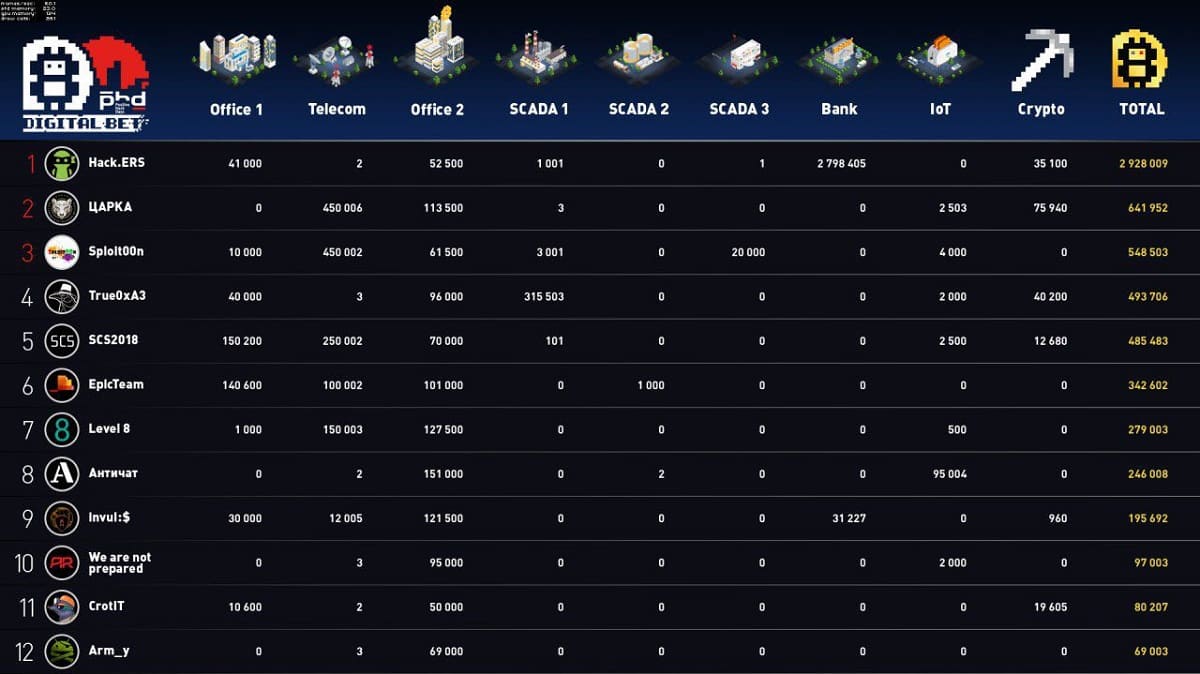
The CAICA and Sploit00n teams succeeded in hacking mobile subscribers: SMS messages were intercepted and then a vehicle was located based on GPS coordinates. The teams took advantage of the fact that the telecom operator's base stations had been specially left unprotected by the organizers. In a separate case, during the afternoon, CAICA was also able to reset the passwords of all users of the telecom operator's portal. CAICA tried to sell the reset accounts on the black market, but the would-be buyer suspected that something was up and the deal fell through. In the meantime, the telecom operator quickly restored accounts from a backup after receiving subscriber complaints and patched the portal flaw that the attackers had taken advantage of. As a last resort, the attackers then tried to make money by turning in the accounts as part of a bug bounty, but the telecom company paid out a pittance. (Note: In all fairness, this sequence of events was not the result of defender negligence. The organizers had required that the defenders temporarily disable WAF protection for the portal in order to install updates and test new functionality. Naturally, attackers leapt at the opportunity.)
Towards day's end, unknown attackers tried to bruteforce SIP accounts online, but due to a timely change by the defenders to the Asterisk configuration, the attack was slowed down before its ultimate failure. It was evident that attackers were in a rush, judging by their botched effort to bruteforce non-existent phone numbers (one digit was missing).
Later on, two teams dug up compromising materials on one of the city's insurance executives. However, one of the teams did not have the information needed to confirm that the stolen correspondence actually belonged to the executive in question. The other team obtained only part of the correspondence. The black-market buyer paid for this information, of course, but not as much as attackers had been hoping. Near the end of the second day, one team succeeding in tracking another car via GSM.
Industrial infrastructure was a much tougher nut for attackers to crack. Although they had hacked an unprotected office on the day prior, attackers were slow to realize that the office was responsible for a process network containing industrial equipment. When numerous attempts to obtain remote ICS access had failed, the attackers switched to trying to connect locally. Attackers and defenders struck an impromptu ceasefire in the early morning hours: both sides tried to get an idea of the workings of the process network, with hackers attempting attacks under the watchful supervision of the defenders.
The attackers hacked another office on the second day. Several services were hacked as well. As announced by the SRV and Advanced Monitoring teams, one Linux machine was subjected to a lengthy bruteforce attack. Eventually, after using an extra-large dictionary, the attackers succeeded in obtaining account credentials. They then attempted to start lateral movement and attack internal services while bypassing the NGFW, but were stopped before they could do so. In just two days, the defenders' WAF repelled around 1,500,000 attacks, which resulted in 30 security incidents.
Late in the day, one team pulled off a DDoS attack on a controller and caused an oil spill. Team True0xA3 even caused a citywide blackout in the closing minutes of the game. Nor was the railroad immune: unknown hackers were able to seize control of a locomotive.
One hour before the end of the cyberbattle, the city decided to try living without its antifraud system. Team Hack.ERS rose to the occasion by cleaning out the bank. Previously hovering around last place, on the strength of this sudden development Hack.ERS rose to kick CAICA (last year's champions) out of first place.
Final results and task analysis TBA.
Digital Bet: the underside of digitalization

Any technology can be turned into a weapon. Several years ago, hackers used contextual advertising to perform targeted attacks against American defense and aerospace companies. Fine-grained control of the intended audience, made possible by advertising networks, allowed the attackers to plant malware on the systems of employees at targeted companies. Which other technologies could be used in surprising ways? The new challenges of the digital age were discussed at "Digital economy: A threat or a chance?" by representatives of Informzashchita, Russian National Coordination Center for Computer Incidents, Rostelecom, Sotsioma, IBM, and Group-IB.
Stanislav Bartashevich, Director of the Information Security Product Office at Rostelecom, commented on the rise in attacks on businesses and governments. Every day, Rostelecom logs approximately 800 DDoS attacks on the company and its clients: "Some of the most interesting recent attacks were linked to the Russian presidential elections, when the sites of the Central Election Commission and others were hit by over 50 powerful attacks, aiming at both DDoS and web application vulnerabilities."
Attack effectiveness, as well as attacker types and motivations, were covered by Dmitry Volkov, co-founder and Head of Threat Intelligence and Investigation at Group-IB: "We have two sources informing us of how successful an attack is: the first is our equipment, which shows that attacks are getting through, and the second is incident response. The client figures out that something has happened and we come in to deal with the consequences. We are performing more and more incident responses every year. This does not necessarily mean that the total number of attacks is rising—rather, attacks are becoming more sophisticated and drawing more attention from executives. It's currently fashionable to say that the number of attacks is increasing. That's true, narrowly speaking, but viewed in terms of their actual effectiveness the number is falling."
Participants shared their views on security in the digital world: the profile of attackers, feasibility of attacks, effectiveness of protection, and regulatory compliance. The human element, in terms of staff capacity and insider threats, was front and center. After all, security ultimately depends on the skill of employees. Nonetheless, the general sentiment was that such challenges do not negate the many opportunities on offer.
A hole in your pocket
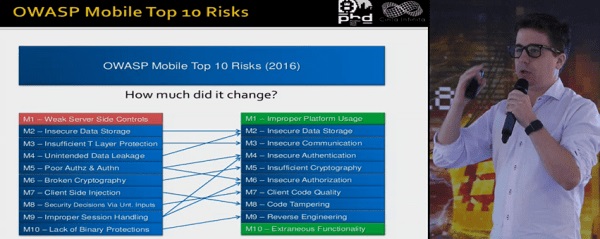
The average person uses 30 mobile apps per month. Security of smartphones and tablets was on the mind of Gustavo Sorondo, CTO at Cinta Infinita, in his talk "Mobile app security fails and how to survive them." Gustavo performed his first testing of a smartphone app eight years ago for an Internet bank, when nearly nobody had done such a thing. Only in 2014 did OWASP release its first top 10 list of mobile app vulnerabilities, before updating it in 2016. Gustavo's first security concern: incorrect platform usage, replacing weak server-level control. For example, if an Internet bank is supposed to use fingerprints for login, but the platform allows bypassing this and the developer goes down this path, this would be classified as incorrect usage of the platform.
His second and more important concern is insecure storage of data, such as in logs and cache files. The third worry: insecure communication, when apps send data in cleartext without encryption or do not warn about fake or expired certificates. In Sorondo's estimation, mobile app security lags behind the web by around 10 years. Popular desktop browsers will prominently warn the user if a site certificate is out of date; by contrast, a mobile browser will often remain silent. In addition, no automated systems for pentesting of mobile apps currently exist. Code analysis systems are available, but tend to generate a high number of false positives, making them suitable only as a starting point for pentesting. Gustavo recommends making development and testing of mobile software compliant with OWASP guidelines, specifically the Mobile Application Security Verification Standard (MASVS) and Mobile Security Testing Guide.
Deep diving
There was plenty of hardcore technical lectures at PHDays as usual. Arseny Reutov dissected issues relevant to smart contracts in his presentation "Predicting random numbers in Ethereum smart contracts." Arseny is the Head of Application Security Development Research at Positive Technologies. Besides being the world's second-most popular cryptocurrency, Ethereum is also behind the majority of smart contracts. Alfa Bank and S7 Airlines made a deal using an Ether-based smart contract last year, for example. The contract's algorithm executed transfer of funds upon receipt of documents indicating completion of work. Smart contracts streamline the paperwork that would normally be required, but they have a big drawback—like any program, they are vulnerable to hackers.
Four-wheel computer
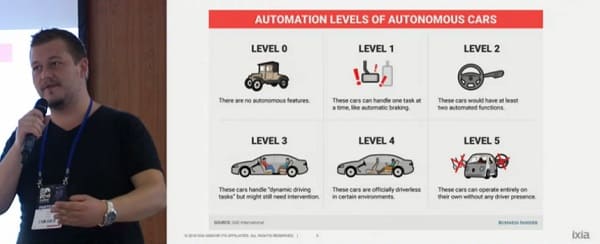
Gartner predicts that over 250 million cars will be connected to the Internet by 2020. These vehicles will exchange data with smart city services to reduce traffic jams, diagnose technical issues, and keep passengers entertained and informed. Convenient, yes—but these abilities will also give hackers huge new opportunities. Stefan Tanase and Gabriel Cirlig from IXIA (Keysight Technologies) investigated a car's onboard computer and discovered a slew of vulnerabilities. Gabriel's own car was used for experimental purposes. According to Stefan, vulnerabilities in a car are much more dangerous than those on ordinary PCs. Human lives are at risk; any glitch or hack of a fast-moving vehicle could be fatal. To find vulnerabilities in the car computer system, the researchers used software such as the open-source Mazda Aio Tweaks. In their talk "Smart car forensics and vehicle weaponization," they showed how a criminal could use GPS data from on-board computers to monitor the location of car owners. One woman even requested that Gabriel help with finding her stolen car by connecting to the entertainment system and obtaining GPS logs.
Banks' fancy toys

The banking industry is a perennial target for attackers. This March marked the arrest of the head of the Cobalt criminal group, which had stolen more than €1 billion from around a hundred financial organizations around the world. Measures to prevent such digital fraud were on the agenda at "Securing the financial sector," which was moderated by Alexey Kachalin, Executive Director of Sberbank Cybersecurity.
Discussion included a provocative question: which will die out first, DLP or endpoint antivirus products? A few of the replies:
Lev Shumsky, independent expert: "The business value of DLP is very hard to get a feel for, while the cost is substantial. Instead of dying off entirely, I think that DLP will be used in special niche cases. It can work well when people work in metal fortresses, locking up their gadgets during the workday behind a walled-off, secured perimeter. But in all other situations, this is an expensive toy that requires inordinate effort from administrators, analysts, and operators. As for antivirus products, they will clearly continue to evolve and adapt."
Dmitry Gadar, Tinkoff.ru: "If you are wondering whether a technology will die out, you have to ask: in what context? Should antivirus protection be on every workstation? Well, the answer to that question says more about your needs than about the merits of the software. The reason for antivirus protection is to deal with consequences. At one bank, I didn't put antivirus programs on our ATMs at all. Instead, I created an isolated software environment. It was so much fun! There was no need to bother with ATM updates because the programs rarely changed. I could just set it once, knowing that no virus would get in. It's the same story with DLP—an expensive tool with marginal payoff. But there are architectural solutions that remove any need for using such clumsy technologies in the first place. The tricky part is to get it sorted out for yourself: which technology are we using and for what, what's the scope, and which technologies fit that scope. Usually we security types are too lazy for that."
How they get your money by a phone call
Alexander Kolchanov, an independent researcher, talked about vulnerabilities in banking-by-phone systems, which offer a way to obtain sensitive information about bank clients and transfer money from their accounts. These banking methods involve either conversing with a call center operator or sending SMS messages. In "Flaws in telephone banking: client data disclosure and money stealing," Alexander demonstrated a number of viable attacks, many of which involved flaws in SMS-based authorization.
As Kolchanov says, a single bank might have several phone banking systems, some of which may be neglected. For example, a few of the phone banking systems could be well protected, but authorization for others might be much simpler. Another problem involves relying only on passport/ID information to verify identity. This information can be used by an attacker to call the bank and perform transactions, or else to learn additional client data for the next stage of an attack.
Problematically, some banks have special systems for premium clients that use weaker authorization procedures. So in the case of a premium client, all an attacker needs to know is information from the target's government ID and account balance. Another dangerous trend is use of personal bankers (with separate phone numbers) for premium clients. At one major Russian bank, ordinary clients are better protected, since they have to give both their ID information and codeword. But their richer counterparts at the same bank do not need to say any codeword. So as soon as an attacker learns the client's phone number, personal banker's phone number, and ID information, it's off to the (fraudulent) races.
Automated SOC

Another late-afternoon session, "How to make your SOC finally work," featured Vladimir Bengin, Head of Sales Support at Positive Technologies. Participants from the Russian State Transport Leasing Company (GTLK), Angara Technologies Group, and Solar Security shared their experience in building security operations centers and how to "train" SOCs to prevent incidents. Sergei Rysin of GTLK emphasized cooperation from IT departments as a cornerstone of SOC operation. The information security department at GTLK consists of a single person, so management (with the support of a private-sector SOC) was happy to allow Sergei to automate things as much as possible. For instance, an unauthorized connection to the Wi-Fi network automatically blocks the network segment. If sensitive data is copied to a USB drive, employees are alerted by text message. IT and security staff receive notifications of important events. Alexander Sukhomlin of Solar Security said that some clients believe that merely contracting with an MSSP provider will result in an SOC. However, building up reaction processes on the client side is an irreplaceable element of creating a mature SOC.
Dmitry Zabelin, Head of Risk Management at Angara Technologies Group, noted: "With an SOC, you're not monitoring people, programs, servers, or some other particular 'thing.' You're keeping an eye on what brings the company money. And what brings a company money? Its business processes. When you're outlining the budget for your SOC, management won't understand a thing if you start describing server cost in the abstract. What does get their attention is the fact that a cyberattack could disable your hydroelectric plant and unleash 240 meters of water on an entire region."
Two days without rest
The forum hosted hack duels, online competitions, various contests on hacking smart grids and smart contacts and getting through a smart-home labyrinth. The cultural program included a comics contest, reading cyberpunk stories, the Positive Hard Days rock festival. Be patient, we will tell everything about these activities soon.
For now, first comments about the forum:
Alexander Bondarenko, CEO, R-Vision:
"I couldn't get enough of PHDays—it just flew by. There were so many interesting talks, meetings, case studies, practical discussions, and new ideas. We were able to present our latest accomplishments, get useful feedback from the community, and be a part of the conversation on the most important topics in security.
PHDays continues to set the bar for events in the security industry. The combination of applied security and thought-inspiring talks would be very difficult to find anywhere else."
Grigory Galkin, Development Director at MONT:
"Joining Positive Hack Days means joining the battle for digital world security. Every year, the most current and fundamental issues are raised at the forum. This time we talked about digital economy, which became a starting point of global changes. Be believe that together with industry experts we can protect our digital future."
Recordings of these and other talks at PHDays 8 are available online at https://www.phdays.com/en/broadcast/