Digital Substation Takeover: Contest Overview
6/11/2015
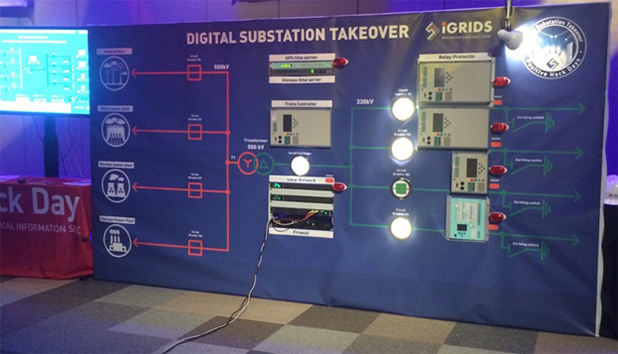
Digital Substation Takeover, presented by iGRIDS, was held at PHDays V. The contest's participants tried themselves in hacking a real electrical substation designed according to IEC 61850. The general task was to perform a successful attack against the electrical equipment control system.
What it's all about
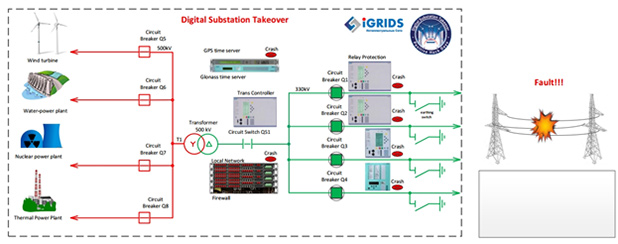
A special high voltage (500 kV) substation model had been developed for the contest. It included switches, time servers, protective relays that are used in modern high voltage electric networks to ensure protection in emergency situations and incidents (in case of a short circuit, faults in a power transmission line etc.).
Several scenarios were offered, each of them corresponding to unauthorized access to switches: circuit breaker opening, earthing switch closing despite operation blocking. The contest's organizers suggested that the most difficult task—that is to cause an emergency on the site—would be followed by fireworks of burning wires of the model overhead power line set nearby.

This year's format combined various competitions with capture the flag contests. CTF teams along with the rest of the forum's participants were able to take part in them (see our article on our blog). About 50 PHDays attendees and several CTF teams took part in Digital Substation Takeover.
Technical details
The model used the following equipment:
- Siemens SICAM PAS v. 7.0,
- common protective relays and switches,
- GPS and GLONASS time servers,
- industrial switches.
The course of the contest
Since the contest was held for the first time at PHDays and due to its specific nature, participants spent the first day studying power-system protection, switches, and operation blocking. They had to analyze large amounts of information found on special forums, vendors' sites etc.

The contest comprised several tasks of different difficulty levels:
- temporal destruction to the substation's information infrastructure (was performed six times);
- time server reprogramming (was performed once);
- unauthorized disconnection of consumers (twice);
- detecting an unknown vulnerability (once).
The most difficult task was to take control over primary devices and issue a command bypassing blocking. No one managed to solve this task (though one team got quite close).
Sergey Sidorov took first place, Alexander Kalinin came second. RDot and ReallyNonamesFor gained some points for hacking the substation.
The winners received tickets for PHDays VI. So get ready for the new version of the contest that will be held in spring 2016!
Not quite at ease
During the contest, representatives of power supply companies, such as the Federal Grid Company of Unified Energy System (FGC UES), were watching the process closely.

"To tell the truth, when I saw those people lounging in beanbags and hacking industrial control and protection systems for some virtual profit, I felt uncomfortable," said Mikhail Seleznev in an interview [ru] with Digital Substation, an online magazine. Mikhail is the head of the ICS and metrology division of the relay protection department at FGC UES. "No one can guarantee that a group of such creative individuals won't gather together and use the knowledge their obtained during this contest to crack real infrastructure—just for the fun of it. Are they aware of the weight of possible consequences of such actions?"
However, Mikhail doubts that it's IEC 61850 that should undergo any changes: "The standard should continue to develop for the benefit of the purposes it was designed for. Information security should be the subject of other standards. There has been much talk about ICS protection recently. In fact, it is important to engage representatives of power supply companies in such discussions—and in putting new methods into practice."
iGRIDS, the organizers of the contest, registered everything that occurred on the stand. By the middle of the contest, it became obvious that the range of threats was broader than they had expected. The developers assure that they will take into account new attack variations when developing subsequent versions of protection systems. And they’ve already got an invitation to take part in PHDays VI!