Food stores and air ticket systems raided by hackers in Moscow—The Standoff cyber-range is in full steam
5/20/2021
The contentions at The Standoff cyber-range are at their equator now, after two days out of four. Digital twins of real retail stores, airport, railway, seaport, traffic light system, power plant, chemical plant, and oil terminal are continually attacked by competing teams. In parallel, lectures are presented by our guests, some of whom contribute to defending the city model. The international forum Positive Hack Days begins on May 20 to end on Friday, together with The Standoff.
By Wednesday evening, the attackers gained access to a point-of-sale terminal of the cyber-range’s retail network and "purchased" 68,950 rubles worth of alcohol at 100% discount against a real till slip. They hit the store’s ERP system and managed to remove the special excisable product mark from the hard liquor items, which resulted in withdrawal of the selling license for the products. The hackers also accessed personal data of the outlet’s staff and clients and stole some strategic documents.
The transportation industry facilities were truly bombarded by hackers. Several teams were able to defraud the ticket selling system of the transportation company Heavy Ship Logistics, which serves the airport, railway, and seaport. One team gained access to the operations data.
So far other facilities prove more robust. The petroleum production and refining corporation Nuft had its "Loss of massive contract due to bid theft" risk triggered by the team True0xA3. The same team has sent the Tube company’s plans to take over the advertising market down the drain: they hacked into the Tube CEO’s computer, stole information about the forthcoming deal, and sold it to rivals. Tube shares fell to a record low. 25 Hours, a commercial real estate complex and amusement park management company, and the city’s energy operator Big Bro Group are still going strong, but the situation can change any minute.
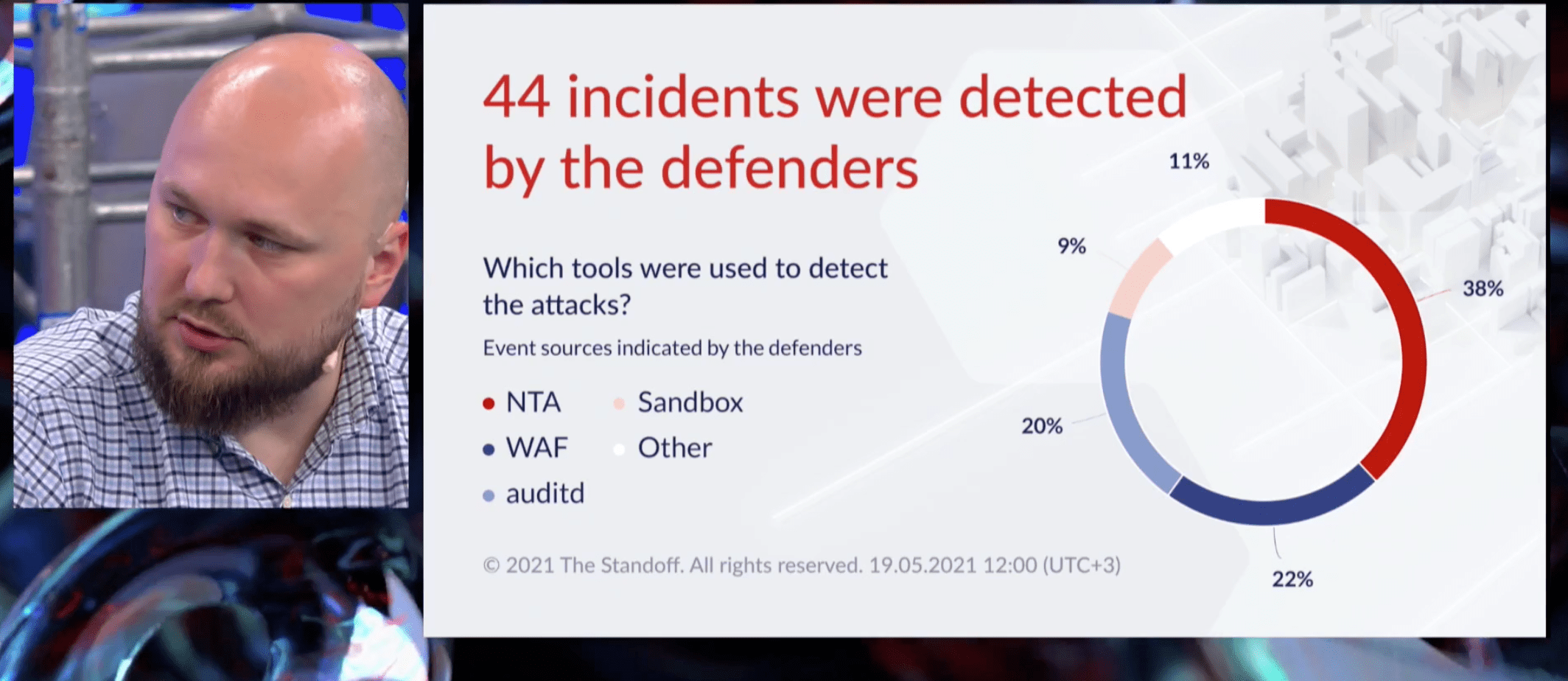
Detailed statistics are already available for day one. The attacking teams have detected 133 vulnerabilities, the defending ones have reported 44 incidents.
"During day one at The Standoff , most of the incidents were recorded using the NTA class solutions (38%)—one way or another, all attacks are visible in traffic," said Alexey Novikov, PT Expert Security Center director. "One can use tunneling or other methods of concealing their actions, but the traffic will always contain the traces. There are many web apps on the perimeter, but there are even more targets inside the network, which is why WAF systems have registered 22% of incidents—second place among all the solutions. Same as in real life, as soon as you place a service on the perimeter, within 30 minutes you see hackers trying to exploit its vulnerabilities. Every fifth incident was detected with the help of auditd. The solution monitors user activities at the host machines: when hackers first penetrate them, conduct reconnaissance, and upload software. And almost every tenth incident (9%) was detected with the help of a sandbox—those were social attacks with malware mail. Some defenders even try opening them."
Cybersecurity reality. Figures and facts
At the same time—almost continually—the cyber-range presents lectures by prominent information security experts.
Dmitry Sklyarov, head of apps analysis at Positive Technologies, discussed the origin of the word "hacker", originally denoting a person studying complex systems without looking for personal gain, and why it had come to be mixed up with "cracker"—one seeking unauthorized access to private information in order to manipulate the data.
During the talk, Dmitry covered some of the subtleties of his work at Positive Technologies underscoring the difference between the "black" hackers and the "white" ones—the security researchers.

"The main difference between the "good" guys and the "bad" guys is their motivation. When finding weak spots in a system, I highlight them instead of exploiting them to make money or steal from the users. I seek to make the world a better place," said Dmitry Sklyarov. He also pointed out that it is impossible for a hacker to cross from the dark side to the light one because of the leverage their accomplices have over them and the unconcealable traces of former hacking activities. According to Dmitry, having once opted for the dark side, the person sticks to it all their life. The expert also touched on the misleading sense of impunity when committing cybercrimes implying criminal liability.
Average ransom—one million dollars
Evgeny Gnedin spoke about the results of the most interesting studies completed by Positive Technologies over the past couple of years and featured in the yearly Positive Research magazine, the new issue of which is released, as the tradition goes, during the PHDays. The head of analytics at Positive Technologies has covered in detail the main 2020 trend—ransomware attacks, as well as the advent of such term as "ransomware partner program". "The ransomware business tends to become distributed between specialized groups, each addressing a subject of its own: some of them write code and create files (but don’t hack companies), others pack the files, thus creating a chain. Every contributor ultimately gets its share of the ransom collected by the ransomware operator—the global average for attacks of this kind is around USD 1 million of ransom," said the expert.
Evgeny also highlighted one more trend dictated by ransomware operators—selling of accesses (accounts, installed tunnels, and web shells) by underskilled attackers as part of the partner program. Underskilled hackers don’t know how to use access once it is established: how to develop the attack inside the penetrated infrastructure or sneak around the defenses without being noticed. What they do know is that this information is in high demand.
"Since 2020, the offer of accesses for sale has grown tenfold, the price per access sometimes ranging from ten thousand dollars to several hundred thousand dollars. The share of "cheap" accesses is growing: early last year low-cost accesses accounted for 15% of the total; by now the figure has reached 60%", said Evgeny. According to him, the APT groups able to upgrade privileges in a given infrastructure can buy any type of access and have it monetized.
All members of the defending team need a set of skills of their own

Teams from large, prominent companies, such as RBK.money, Azbuka Vkusa, and others are scheduled to protect the virtual city on the cyber-range. Dmitry Ushakov, technical manager of the sales department at Positive Technologies, offered recommendations to the blue teams that are scheduled to help defend the city.
"The ideal number of competitors is between six and eight," Dmitry said. "The participants’ different skills are important. Someone needs to specialize in forensics and someone in defense, while other participants should have skills in monitoring, and so on. Some of the companies have come here because they want their vulnerabilities to be found. Some companies are participating to get training under stressful conditions and to get a feel for where each person’s strengths lie."
According to Dmitry Ushakov, nowadays the priority of cyber-ranges and digital twins is evolving very quickly. Even in Russia there are several such platforms, including the state-owned national cyber-range.
Food for vulnerabilities
Azbuka Vkusa brought along an actual cash register like the one used in its supermarkets. Participants in The Standoff are also looking for vulnerabilities in this cash register. Dmitry Kuzevanov, head of the information security department at Azbuka Vkusa, said that his company was the first food retailer to launch the bug bounty program, and that participants had the opportunity to choose a monetary reward or food items of a higher total value. Over the course of the program, more than 100 vulnerabilities were detected, with around 10% of them being classified as critical.
"For a long time, retail on the whole bought solutions from integrators and didn’t have their own development, while many employees weren’t very familiar with computers. As a result, the information security situation was worse than in IT companies, for instance," Dmitry said. "Now, all retailers have their own development, mobile app, and rewards program. If you look at a cash register, it’s a full-fledged computer with wireless communication. Employees circulate around the premises with data-collection devices that have access to prices, payments, and the reward program database. All of this needs to be protected. But at the moment, our main security issue has to do with the human factor. If an employee opens a phishing message, enters valid login credentials, and malicious parties penetrate the network through that access, no security system will help. So it’s crucial to train all retail workers. The second key aspect is the use of secure development methods when creating software. At Azbuka Vkusa, this approach is used at every stage of the product’s lifecycle, from conception to rollout."
How secure is the travel industry? Pentest results

Igor Lukic, CEO at Enigmasec, shared his thoughts on the security of the travel industry. He cited incidents where hackers broke into hotels and demanded ransom from the management so their guests could enter or exit their rooms. Lukic also said that most tourists placing online orders and using different services with their personal accounts do not scrub their login or credit card information from smart TVs or other smart devices when they leave the hotel.
"The main vulnerability in hotels is the level of service—for example, if a guest asks to print a boarding pass or plug in a USB drive, the staff will never refuse because they’re trying to make every guest feel special. They’ll just plug the guest’s USB drive into the main computer at reception, and once the attacker gains access to it, they can easily post vulnerable code or PowerShell into the hotel’s shared network," Igor said, discussing the results of the pentests done on tourism companies.
He concluded that the travel industry needs to invest in informing customers about cybersecurity rules so that they do not, for example, fall victim to phishing attempts when they connect to fake Wi-Fi networks in airport waiting areas.
How to report vulnerabilities
Let’s imagine that one day you discover a vulnerability. What to do about it? Maxim Goryachy, an independent researcher known for identifying security flaws in Intel processors and chipsets, said that once a vulnerability has been detected, the researcher has three legal options. "First, do nothing. Second, get in touch with the vendor and try to convey the need to eliminate the vulnerability. Sometimes it’s necessary to double-check whether the manufacturer of the vulnerable component has fixed the bug. Third, try to sell the vulnerability to a third-party organization, such as ZDI, which can encapsulate it. What they do with it remains at their own discretion, for which reason I do not recommend this course of action," noted Maxim.
In hardware systems, it is not always easy to figure out which vendor is responsible for a detected vulnerability. A major operator can sell a 4G modem bearing the logo of a Chinese reseller, while the real manufacturer is some third company. Publicity helps in such cases—for example, researchers at MITRE can request CVE identifiers. If the CVE record is found, MITER, like an arbiter, confirms the existence of the vulnerability. In this case, the researcher does not even need to disclose the details of the vulnerability (lest they be exploited by cybercriminals). Going forward, the vendor itself often reaches out.
According to Maxim, vulnerability elimination can give vendors an edge over the competition (a major smartphone maker’s ads already highlight user data privacy).
Active participation in bug bounty programs is incompatible with working for a large company, says Maxim. If you work for an Amazon-type organization and find vulnerabilities, say, in an Intel processor, the two companies’ cooperation agreements, including an NDA, could cause problems. It is automatically assumed that this cooperation grants access to materials related to vulnerability detection. Another reason is that bug bounty programs don’t pay as well.
"In 2020, Facebook paid all researchers around USD 2 million, and Intel, since 2017, approximately USD 2.5 million, if HackerOne statistics are anything to go by," said Maxim. Therefore, professional bug bountying, especially in the area of hardware vulnerabilities where various equipment is required, may not be all that rewarding.
Of open source and fears
According to Anton Kuranda, CTO at Rbk.Money and Osnova IT-company, developers should not be afraid of opening their code. He gave an example of Google which bought Android, Inc. but left the code open. "This might have been one of the reasons why this OS is so popular. Thanks to the open source code, even sanctioned Huawei is still able to sell Android smartphones (though still experiencing some problems with it). Another example is the server market: 95% of all servers use various Linux distributions. As a result, even the giant Microsoft corporation, which traditionally has been working with proprietary code, is greatly interested in exploring the open source opportunities," Anton added.
When speaking about the open source code safety, Anton gave an example of the Linux Foundation Technical Advisory Board that banned the commits of the University of Minnesota for their experiments with the attempts to insert deliberately buggy patches that contained errors and latent vulnerabilities.
"Producing code that you are ready to present to the community poses additional requirements to the documentation and code style. When writing closed source code, you can ask your coworker for advice, but when you open your code to the world, you must describe how it works and draw up building instructions. The very idea that the code may one day become public is a great source of mobilization and motivation for people. If you develop a closed solution, you can pile up some spaghetti code, compile it somehow, and no one will ever see it. Open source code is a completely different story: it can hurt the developer’s reputation. This can be a strong motivation for people to write clean, beautiful and safe code," Anton Kuranda said.
The Standoff, the world’s largest open cyberbattle, will be held on May 18–21 this year. You can keep up with the battle here: standoff365.com
