Forgot Your Password? Hash Hacking at PHDays 2012
7/10/2012

An unknown password is “made” according to the following recipe: extract minced information (hash) from cookies, database dump or another resource and process it with various tools until you get the combination of symbols you need. For the cracking time not to exceed the age of our Galaxy, you should consider numerous peculiarities. The success depends on the hacker’s experience, encoding algorithm, salt (if presented), the utilities and hardware used (nowadays programs require powerful graphics cards to decode hashes). To find out how the task is tackled by best hackers, read the article covering the Hash Runner competition held as a part of PHDays 2012.
All competitions of this type are characterized with hegemony of a number of teams: hashcat, Inside Pro, john-users, which is not surprising because these are communities of developers, testers and common users formed around most popular hash hacking tools. And their success is rooted not only in years of experience, good training and unity of teams, and accessibility of formidable computer powers, but in the ability to modify the tools in the real time mode in response to ever changing circumstances.
All the above-mentioned teams took most active part in Hash Runner at PHDays 2012. For two days the contestants fought for a useful prize - an AMD Radeon HD 7970 graphics cards.
And here are the results.
Rules
The competition was open for any Internet user. All in all, there were 19 participants from various countries participating.
The competitors are given a list of hash functions generated according to various algorithms (MD5, SHA-1, BlowFish, GOST3411, etc.). Points for each hacked hash were scored depending on the complexity of algorithms, generation rules and dictionaries used. To win the competition, a participant was to score as many points as possible during a limited period of time, leaving the competitors behind.
It's all simple: you have a number of hashes of various types and two forum days (the competition started at 10:00 a.m. on May 30 and ended at 6 a.m. on May 31) to crack as many as possible.
Participants
The participants of the competition were from different countries. The main rivals were InsidePro Team 2012, teardrop and Xanadrel.
Strategies
To win the competition, the participants were to figure out password generation rules. The generation used dictionaries in different languages, as well as name dictionaries. The first rule guessed by the participants was a dictionary word repetition, for example:
fayettefayette
jeweljewel
hamlethamlet
Each hash types contained a certain number of passwords generated according to the same rules. Thus, by guessing a password to a hash encrypted with a simple algorithm and figuring out its generation algorithm, one could apply the knowledge to the rest positions in the list and guess passwords to more complicated hashes.
It was good thinking, and not good guessing, that gave the push to the three leaders.
Each team used its own tactics: one tried to brute force the passwords to the most complicated hashes, thus scoring more points, another, on the contrary, tried to outrun their rivals in the number of successfully hacked hashes, focusing on plains.
The leaders gave dust to their competitiors.
Xanadrel (France), who used to paly for Hashcat, decided to play a one-man game this time and fought on its own.
Hardware he used for the competition included PC (i7 950, 1x 5770 and 1x 7970) and i5 2300k core for 4 LM hashes.
Software tools:
· Hashcat
· oclHashcat-plus
· ophcrack
· rcracki_mt
· passwordspro
· maskprocessor
The passwords were cracked by wordlist attacks and generation of basic/common rules in hashcat and passwordspro for the GOST hashes. During the entire competition, the contestant wasn’t able to hack not a single DES, neither phpbb3, ssha, or wordpress hash (they were unusually long and hashcat failed to crack them).
It was not until the end of the competition when Xanadrel thought of bruteforce attacks and managed to get a couple of passwords like 6{x#_a or 9Mv)0. Besides, there were passwords of the ddyyy type (for example, 08march1924). For this cases, the contestant had to create rules for appending/prepending the year/day and a wordlist with months only.
Оригинал райтапа Xanadrel [eng]
Unlike Xanadrel, who chose to fight on his own, the guys from Insidepro teamed up. Their strategy was simple: try attacking any algorithm wherever possible using whatever technique was handy (a bruteforce attack, dictionaries).
The list of hardware and software tools used by the team:
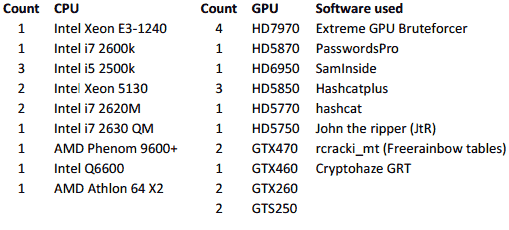
Note: Since most of the team members could contribute only when they had time to it, the listed tools were not used continuously during the competition days. Only a part of the hardware/software was used at once.
Most of the times, the participants relied on tools they developed themselves, such as nsidePro’s Extreme GPU Bruteforcer, PasswordsPro and others because they support the saltless Wordpress and phpBB out of the box. However, right in the middle of the contest, one of the team members managed to patch JtR to support these saltless hashes, thus enabling more successful attacks.
For the details, see the details in the Insideproteam's write-up (ENG).
Another leader of the competition was Teardrop, formed specially for the competition by those Hashcat, who were not able to take part in it. The team used the following software:
· Hashcat
· oclHashcat-plus
· oclHashcat-plus custom build to crack saltless PHPass and DCC2
· Hashcat-utils and Maskprocessor
· John the Ripper
· rcracki_mt for LM
· PasswordsPro for GOST
In the run of the challenge, the team members had to make some modifications to oclHashcat-plus and John the Ripper to load the PHPass and BFcypt hashes. The full story you will find on the Hashcat forum.
Statistics
Some fancy graphs.
The first one depicts participants' progress in time:
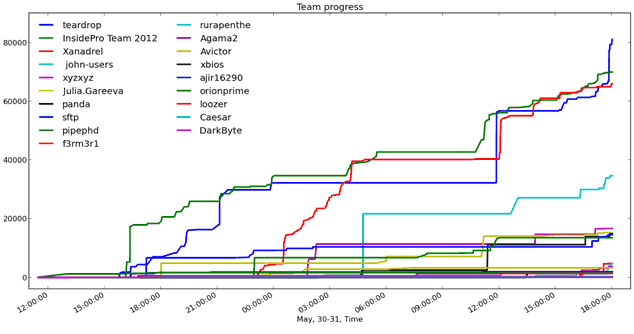
It should be mentioned that in such competitions participants usually try to send their answers as late as possible to confuse the rivals.
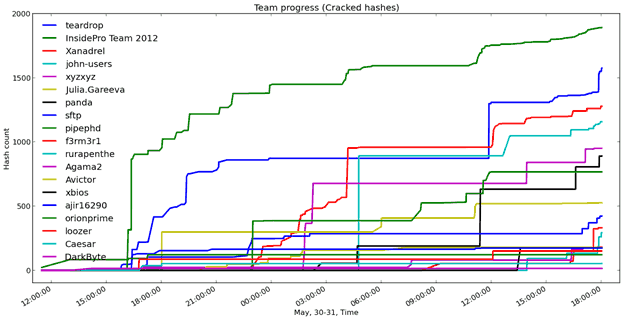
Teams progress in hash hacking:
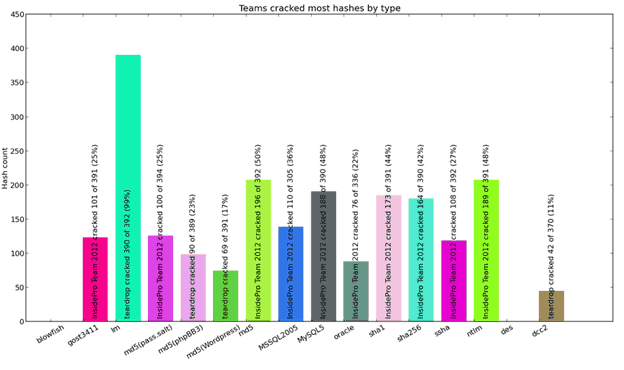
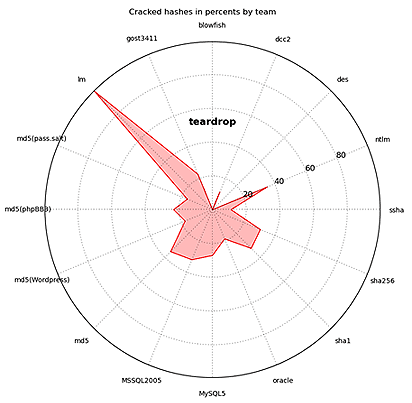
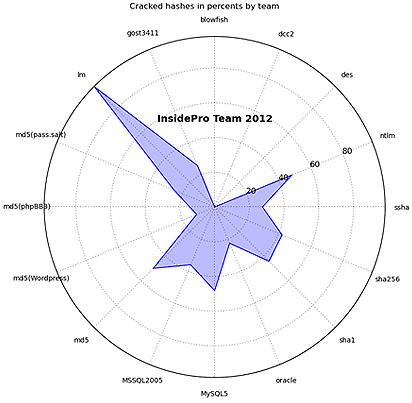
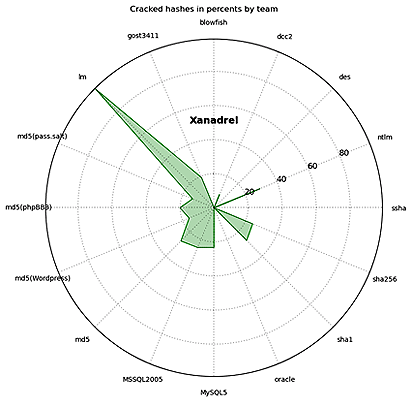
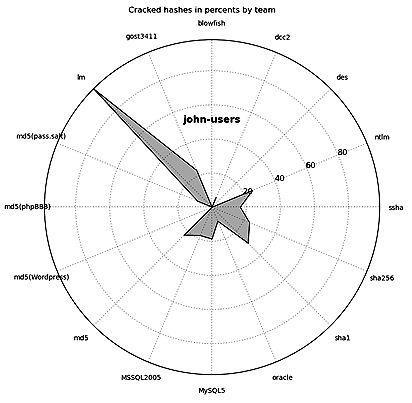
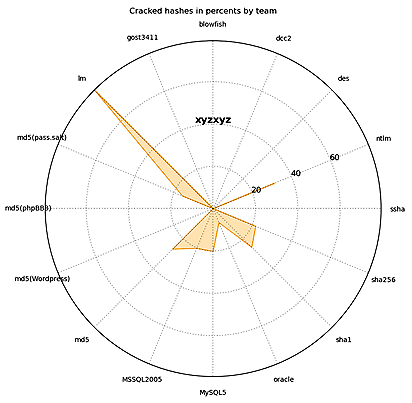
The following types of hashes were the easiest for the teams to crack:
Top-5 Teams
Teardrop
InsidePro Team 2012
Xanadrel
John-users
Xyzxyz
Winners
The final part of the competition proved to be the most tensed; the winner was decided within the latest minutes. The participants stopped their programs in a few minutes before the end to send all the passwords they had managed to brute force.
InsidePro Team 2012 held the leading position for a long time, but Teardrop were able to make a final push and leave them 11,000 points behind. Here is the winner's stand:
3. Xanadrel
Note that the winners managed to bruteforce passwords only to 11% of the hashes.
All the participants were awarded by the organizators and sponsors of the event. The special prize, an AMD Radeon 7970 graphics card, was presented to Teardrop (Hashcat). Our congratulations to the teams!
P.S. Visit the official site of the PHDays forum to find the links to video of the presentations.