HackBattle 2.0: school canteen ICO under attack
6/6/2018

In May 2017, Positive Hack Days VII presented a brand new contest named HackBattle, which attracted audience attention. Almost 100 security specialists took part in that contest. The audience was so eager to see the final that the area was packed (more details in the last year's review). Inspired by professionals' interest, we decided to hold HackBattle 2.0 at PHDays 8. Learn how the contest passed this year, and check if you can solve the tasks.
Participation rules
The contest was held on both days of PHDays. During the first day, there was a qualifying stage: we selected two strongest and bravest participants who solved most tasks within the minimum period. The final of the contest was on the second day. Two hackers were to attack one aim, and the first to get through and escalate privileges on the target system was the winner. The progress was commented by security experts, and highlights could be followed on a large screen.
Qualification
As in the previous year, the participants were to solve CTF-format tasks against the clock. Each participant had 35 minutes to solve 10 tasks and earn a certain amount of points, depending on the task complexity. Each participant could take part in qualification only once.
This time we took into account the requests of participants of the first HackBattle and allowed using not only our workstations but also participants' laptops.

Laptop owners at their own table with blackjack and patchcords

Qualification participants
It was hard to define two best participants who would be able to solve the final task under pressure of audience attention. The fight was very tough and it was unclear until the very end who was going to play the final round. Scoreboard displayed a small gap between the leaders—just 50 to 100 points—and when the scores were equal, the time difference was mere seconds! Only at 6 p.m., after the qualification was finished, we managed to define the shortlist: Vladislav W3bPwn3r Lazarev and Artur inviz@penis Khashayev.
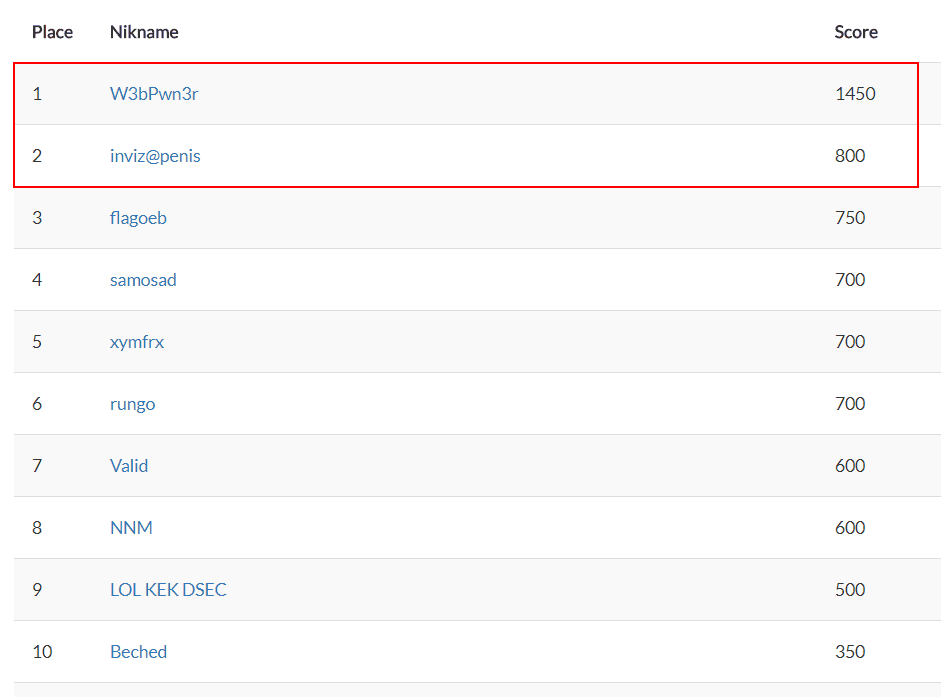
Leaderboard
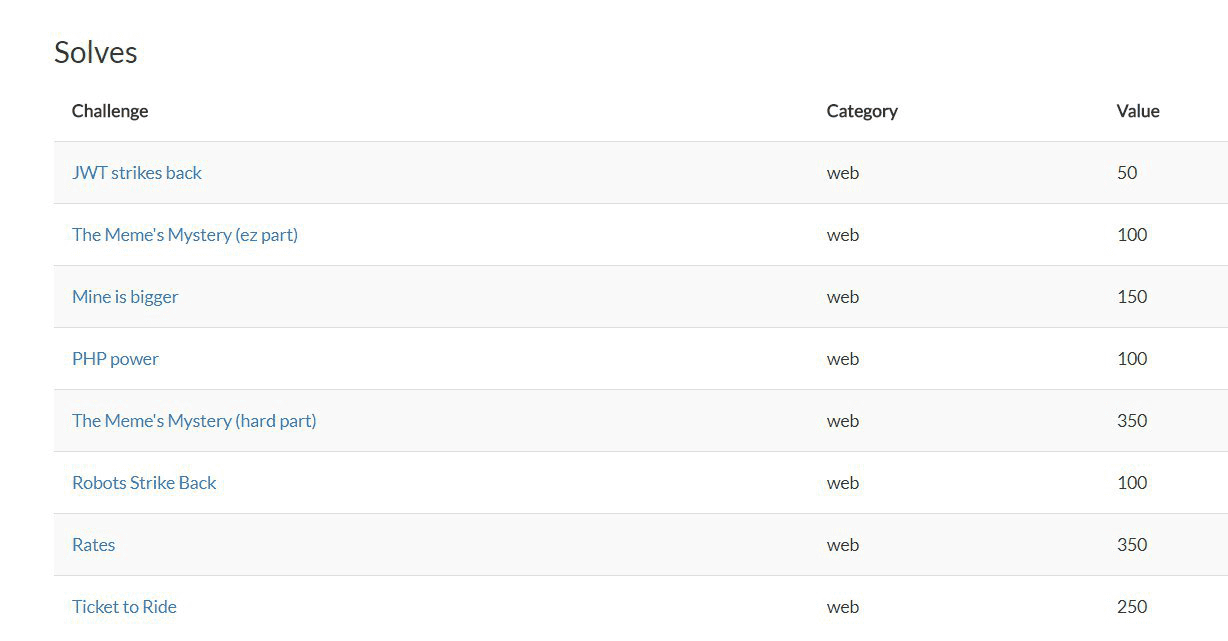
Tasks solved by W3bPwn3r

Tasks solved by inviz@penis
Final
On May 16 at 2:00 p.m., the final of HackBattle 2.0 was held on the main stage of the Congress Hall. As a year ago, the hackers' actions were streamed to the big screen and commented by experts from Positive Technologies. For convenience of the audience, most of which came to support the finalists, each of the hackers' monitors was separately shown on screens on both sides of the main stage.

Battle of the strongest
The final task was to attack the same aim: this year the hackers' victim was a server that hosted an ICO for a school canteen.
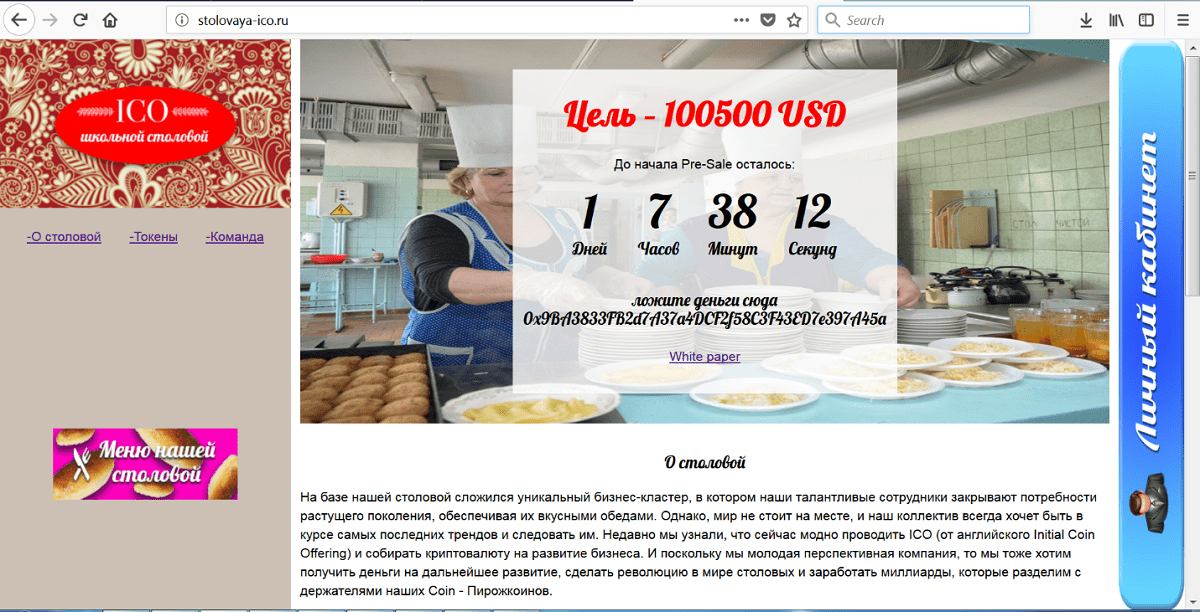
The school canteen ICO website
The task was to replace the wallet ID displayed on the website to any other wallet ID before the ICO presale would start (use the link at the end of the article to download this task). This was a multistage task that could be solved in a number of ways.
During the last six months, Positive Technologies performed numerous ICO pentests, and each tested project contained vulnerabilities of various severity levels. Nowadays, media publish more and more information about compromised ICOs. Obviously, information security in this sphere is not a priority. Therefore, we decided to draw attention to the security of cryptocurrency services and make this issue a topic of the final battle.
The duel took 20 minutes (full-length version of the final, as well as other conference videos are available at phdays.com/ru/broadcast/). This tense battle ended with a victory of Vladislav W3bPwn3r Lazarev who was the first to accomplish the task.

Vladislav Lazarev, the winner
We interviewed the finalists after the battle and learned what their impressions were.
"First of all, I'd like to give credit to the high level of infrastructure and quality of the tasks. It was a nice surprise to be in the spotlight, though doing even customary actions turned out to be more difficult when a lot of people are looking at your screen. Probably, it would be more fun to have the qualification in the same format as the final," said Vladislav Lazarev.
Artur Khashayev shared his impressions: "HackBattle is certainly the event that cheered everyone up during the conference. One of unexpected things was that it took a while to have the Internet working, so I spent some time importing a proxy certificate. But the canteen ICO website was well-crafted. And I would like to highlight the performance of speakers who commented the battle: they did a great job adding vitality and keeping a large audience excited."
Technical details about organizing the stream, performance of the scoreboard and its synchronization with the workstations provided by the organizers are available in Anatoly Ivanov's blog.
Contest tasks
All tasks, except task 10, are OVA virtual machines. Task 10 is a binary file for *nix. All virtual machines have static IP addresses from the subnet 172.30.0.0/24, gateway 172.30.0.1, DNS 8.8.8.8. Access to virtual machines is provided for reconfiguring.
1. WhiteHub (150)
NotSoEvil corp has developed a clone application with blackjack and Brian Crépes. Can you find the sensitive information there?
https://static.ptsecurity.com/phdays/2018/hackbattle/1.ova
phd:ckjyktnbnyfpfgfl
http://172.30.0.15/
2. Rates (350)
Our rate changer is rocket science, can you make it through to the secret info?
https://static.ptsecurity.com/phdays/2018/hackbattle/2.ova
phd:cfvsqkexibqgfhfljrc
http://172.30.0.16/
3. Mine is bigger (150)
Bet you can't beat me! Prove different.
Unix user would know what is going on here:
https://static.ptsecurity.com/phdays/2018/hackbattle/3.ova
phd:vjzgeirfnsxtndpfgfl
http://172.30.0.17
4. PHP Power (100)
Are you good enough at source code analysis?
https://static.ptsecurity.com/phdays/2018/hackbattle/4.ova
phd:zboegjlheuelheue
http://172.30.0.18/
5. Too Smart (450)
This NES games search engine seems to have some vulnerabilities. Unfortunately they claim to have bought a new age firewall, can you make it through and get the private game.
https://static.ptsecurity.com/phdays/2018/hackbattle/5.ova
ssh: task:13372018
http://172.30.0.13/
6. The Meme's Mystery - ez part (100)
Find out what this meme is hiding.
Note that this tasks has two flags. Send the second flag to The Meme's Mystery (hard part)
The Meme's Mystery - ez part (350)
The meme's intelligence has increased, but the flag still seems to be reachable
Note that this is the second flag of the task
https://static.ptsecurity.com/phdays/2018/hackbattle/6.ova
ssh: task:13372018
http://172.30.0.12/
7. JWT strikes back (50)
In memorial of old JWT bugs, the task we solve...
https://static.ptsecurity.com/phdays/2018/hackbattle/7.ova
ssh: task:13372018
http://172.30.0.11:5000/
8. Robots Strike Back (100)
Robots are back, defeat them again and save the princess, mighty warrior!
https://static.ptsecurity.com/phdays/2018/hackbattle/8.ova
dev;V3ryHardP@ssw0rd12345
http://172.30.0.20
9. Ticket to ride (250)
We have developed a nice website to get you some comfortable tickets, is it secure enough?
https://static.ptsecurity.com/phdays/2018/hackbattle/9.ova
dev;V3ryHardP@ssw0rd12345
http://172.30.0.19/
10. Trace Me (50)
This program prints flag, go get it. Oops, nearly forgot to say that it is ouputed to stdout. Hope you are still able to get it
https://static.ptsecurity.com/phdays/2018/hackbattle/10
Final
https://static.ptsecurity.com/phdays/2018/hackbattle/Final.ova
dev;V3ryHardP@ssw0rd12345
IP-address 172.30.0.21
In hosts file add strings:
172.30.0.21 stolovaya-ico.ru
172.30.0.21 www.stolovaya-ico.ru
172.30.0.21 blog.stolovaya-ico.ru
172.30.0.21 www.blog.stolovaya-ico.ru
Entry point: stolovaya-ico.ru
By: Dmitry Galecha, Anatoly Ivanov, and Alexander Morozov, Positive Technologies.