Hot Cyberwar. Hackers and Missile Launchers
7/10/2015

The most spectacular contest during PHDays V was the one organized by Advantech. The contest's participants must gain control over an industrial system that controlled a missile launcher and to hit a certain secret object.
General
A missile launcher on a turret rotating about two axes, and a target were presented on a stand. The contest's participants must gain control over the industrial system, turn the missile to the target and hit it (breaking down the equipment wouldn't count).
According to the contest's scenario, a hacker bypassed the external perimeter and had access to the office's network segment. Those who connected to the network received the operator's login and password and could watch the system in operation. IP addresses of all the set devices were listed in a table on the stand.
This year's format combined various competitions and capture the flag contests (for more information see our blog). About 40 PHDays attendees and several CTF teams took part in the contest.
Technical details
The SCADA system was deployed on the panel PC Advantech TPC-1840WP and was running on Windows 7 Ultimate without any additional protection systems. The operating system's updates were installed, Windows firewall was up. The SCADA system was implemented on Advantech WebAccess 8.0.
Since the software could contain unpatched vulnerabilities, the operator's access was limited to visualization of the processes that go on in the controller. The controller's tags were read-only, and rewriting them didn't affect the equipment's operation. With administrator privileges, the attacker could access the page containing description of the system's structure and intrinsic addressing.

Interconnection between the SCADA system and the PLC was maintained via Modbus TCP with the use of pseudoregisters (reading not from I/O modules, but from the controller's program memory).
In standard mode, client and administrator web access to the SCADA system is available via Internet Explorer through HTML4 using IIS, which is part of a standard Windows distribution kit. By default, authentication is performed by the SCADA system itself.
The physical connection between the SCADA system and the PLC was provided by the L2 managed switch Advantech EKI-7659C with the use of common Fast Ethernet. The connection for contestants was performed through the same switch, via the wire through EKI-4654R or via Wi-Fi through EKI-6351. The switch was not used for VLAN or as a filter for MAC addresses, though it could be used in that way. In addition, the laptop used for managing the stand was connected to the subnetwork.

PLC functions were implemented via the PAC controller Advantech APAX-5620KW, a device based on an ARM processor under WinCE 5. The controller turned the missile launcher due to the timer (for our purpose: it controlled the technological program of the process). For this purpose, the softlogic kernel ProConOs (written by KW Software) was used as a task at the kernel level. The movement program was implemented by the developer in ladder logic by using KW Multiprog. The cycle was 50 msec.
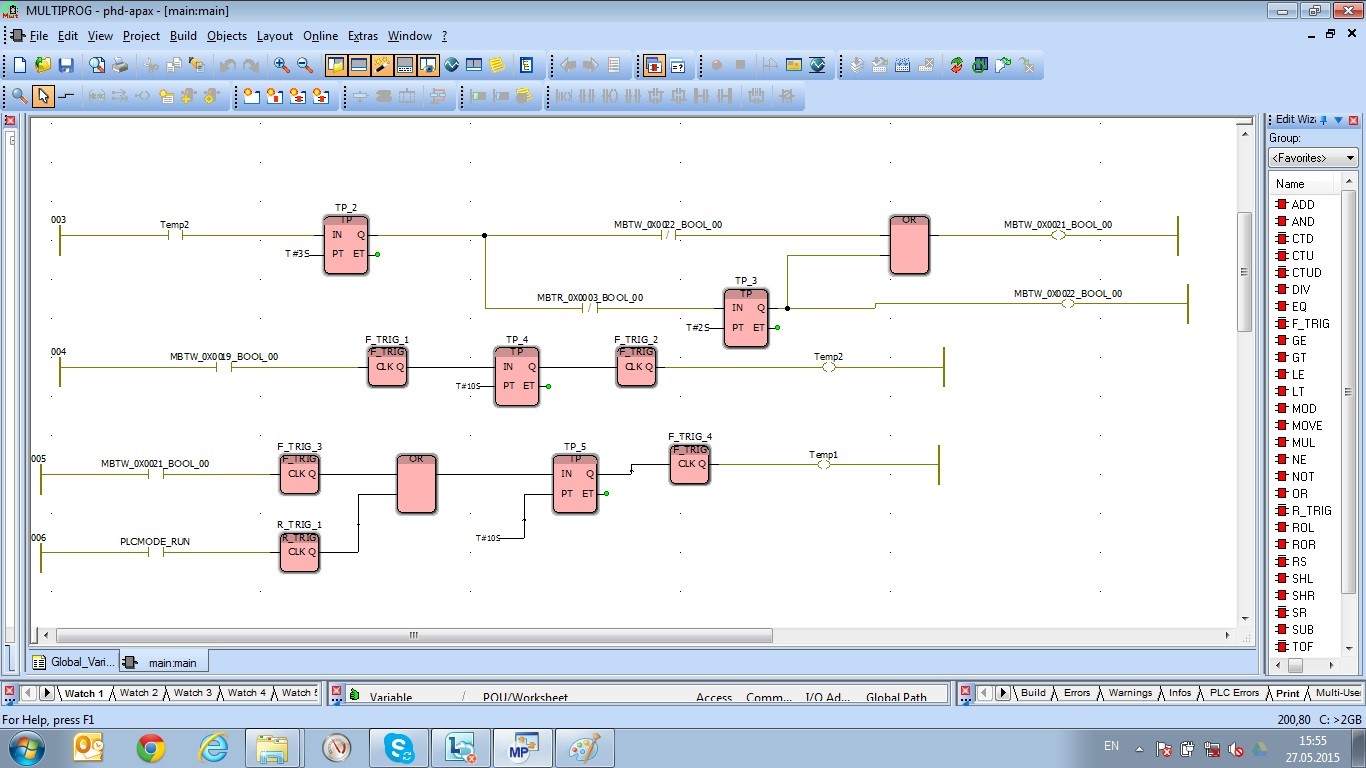
The controller had three standard connection methods: via VGA and USB (unavailable for contestants); via remote desktop (password-protected); via a development system in IEC 61131: it allowed controlling the softlogic subsystem and debug it.
The controller supported two LAN ports, one of which was connected to the SCADA system (the office subnetwork); and the other one, to the input/output modules (the field subnetwork). Network ports had addresses in different subnetworks. This solved the problem of load balancing and separation of access.
For input/output, ADAM-6050 modules (for discrete input from the axes final position sensor) and ADAM-6260 modules were used (for relay control). These modules have the ability of distributed programming in GCL, due to which emergency protection was provided. In particular, when riding into a fin, the DI module reports it to the DO module, and the DO module reversed the appropriate motor for 3 sec. Watchdog that disabled all outputs was installed, in case of communication interruption. The missile actuator control unit's block could be bypassed by recording a logical 1 in a separate internal variable (for which it was necessary to perform a recording function in the Modbus register within the internal subnet).
The physical connection between the modules was performed without the use of an external switch, by using the daisy chain technology in ADAM-6260. The launcher's turret was supplied by a separate 5 VDC unit and was equipped with three motors (rotation around the vertical and horizontal axis and rocket launch). A relay circuit was used to reverse rotary engines and as zero-level protection against short-circuit in the power unit. In addition, the rocket launcher was equipped with five ground-pressure final position sensors (left, right, up, down, volley performed).
Almost all the components of the system contained non-dictionary (generated) passwords of 8—10 characters that included Latin uppercase and lowercase letters, numbers, punctuation marks.
The battle
The contest lasted for two days during Positive Hack Days.
Day 1
During the first day, contestants mostly examined the external subnet's structure and tried to attack the system via SCADA. The hackers disabled operating system services, including the firewall, managed to foist a new user (without administrator privileges though), restarted the PC twice.

Several participants managed to obtain administrator access to WebAccess by using Windows and SCADA exploits, looked through tag descriptions and had the opportunity to stop the system's kernel. However, the system didn't react to the efforts of rewriting tags; the kernel started automatically via Windows Scheduler. At the end of the day the hackers, exhausted, left an autograph on a page of the system and postponed further efforts till the next morning
Day 2
During the first half of the second day, the contest's participants searched for the source of control signals. One of the participants detected an exploit in WinCE 5, but wasn't able to use it.
At 2 p.m. a hint was given: the controller's external segment is read-only and you could try to "pass" the controller.
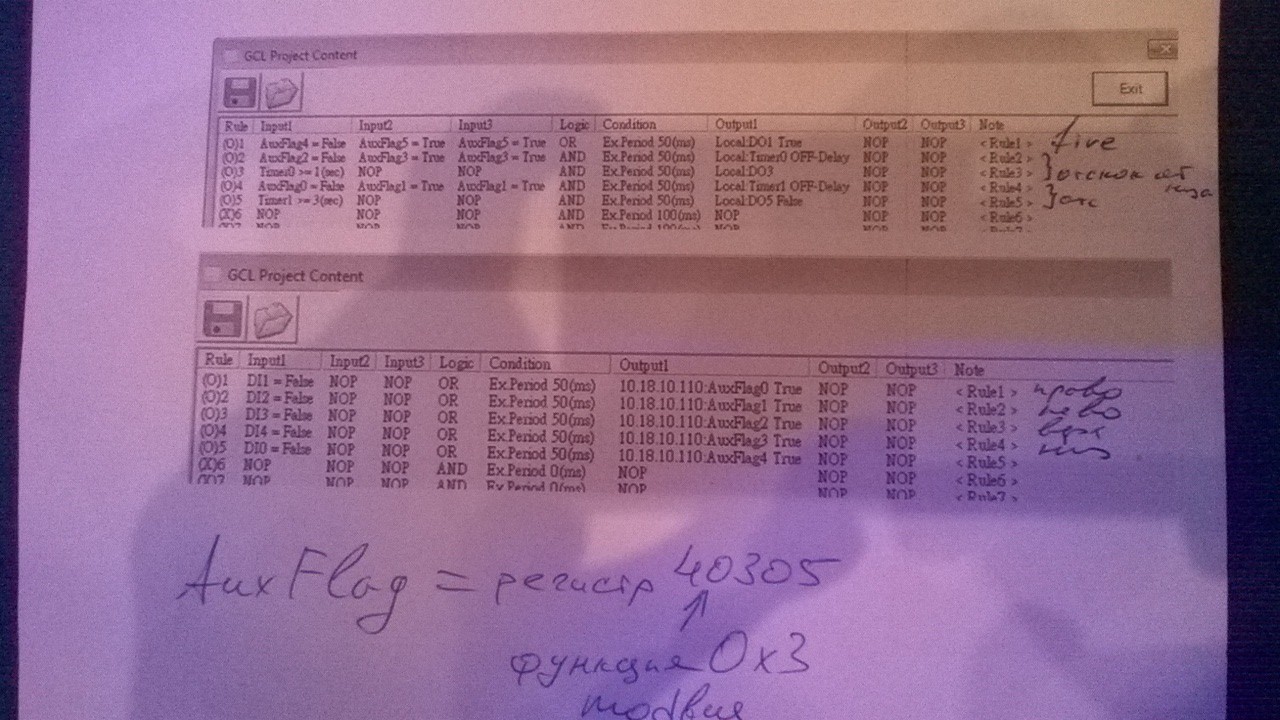
At this point RDot (a CTF team) joined. In an hour and a half the team managed to access the remote desktop APAX-5620, gained the opportunity to "kill" and launch the softlogic task and manipulate network adapters.
One of the contestants claimed to have received the opportunity to unidirectional forwarding from LAN1 to LAN2 without receiving return packages. However, Modbus did not allowed using this opportunity for destructive purposes.
At 3 p.m. some mechanical problems occurred on the stand. The contestants gained the opportunity to intercept packages between KW Multiprog and the controller (stop and restart of the controller, enabling the debug mode, the use of the force function with respect to controller memory cells). However, the contestants didn't use this information.
At 4 p.m. participants were provided with program source codes of the APAX and ADAM modules, which could contribute to discovering ways of exploiting regular programs. RDot was noted for the successful attempt of backward reading the program from the controller (this function in KW Software was not password-protected), turning on the debug mode, and monitoring the controller's registers.
At 5 p.m. users were admitted to the internal network; they launched a DDoS attack against the emergency protection system and tried to disable it.

The contest ended at 6 p.m. No one managed to stop the GCL program or to gain control over the outputs, although there were signs of impact on the modules' firmware.
Prize-winning participants were determined due to the points they gained:
• 1st place: Artur G. from the team Rdot (for hacking the APAX remote desktop, successful work with the source code in IEC61131),
• 2nd place: Pavel I. (the first one to gain administrator access to the SCADA system's interface),
• 3rd place: Alexander Y. (for sending packages between the APAX controller's ports and for applied efforts).
Consolation prize: Alexey P. (for using social engineering methods: detecting SCADA project backup from the administrator's laptop and obtaining the administrator password).
The contest's organizers concluded that:
• Most intruders do not know much about ICS specifics. Participants mainly performed attacks (against ports) or used methods that did not comply with the system's features (monitoring Modbus traffic via Wireshark). However, it is possible to study the system's structure and its standard operation.
• The most vulnerable are those components that are the closest to the operator interface: SCADA client input, remote desktops. For systems based on Windows, additional software is required to protect both computers (firewalls) and communication channels (encryption).
• An enterprise bus and fieldbus must be physically isolated from each other at least by a device with two network cards. Using VLAN is not always effective because of vulnerabilities in web interfaces pf switches.