MeterH3cker contest writeup: hacking smart meters at PHDays 8
6/19/2018
The contests at this year's Positive Hack Days included MeterH3cker, an all-new competition for hacking the smart grid. Participants had the run of two mock buildings powered by solar panels; excess power was sold back to the grid at a special rate. The job of the participants was to interfere with metering by any means necessary in order to improve their account balance.
Stand

The MeterH3cker stand
Today's buildings with solar panels can both consume energy from the grid and sell it back. This idea was at the heart of our MeterH3cker setup.
The stand consisted of two (mock) modern residential buildings with (real) smart grid devices and technologies. Each building contained solar charge controllers, smart meters, and power-hungry devices. Both buildings were connected to a mock electrical substation, where an aggregator polled the building meters, as well as the substation's own meter, to provide the information used for billing.
On the stand's network was a single controller responsible for the heating, ventilation and air conditioning (HVAC) system of each building. In addition, next to the smart homes there was a (genuine) charging station for electric cars; of course, the charging station informed the billing aggregator of how much energy had been used to charge vehicles.
Conditions switched between "Day" and "Night." During the daytime, the solar panels generated electricity and the building meters ran backwards, based on the amount of power consumed vs. sold to the grid. Each building had its own account: as power was generated, the balance of the relevant building increased, and as power was consumed, the balance decreased. The balances were also affected by the rates set on the meters.
Thus the main goal of the competitors was to hack for maximum profit: increase the account balance of the buildings by attacking the installed equipment.
To visualize the results, we created our own billing server, which collected data from the aggregator. The aggregator, in turn, polled the meters in several ways:
- Building #1 meter: via an unencrypted Modbus-like vendor protocol
- Building #2 meter: polled by a VR-007.3 device via an unencrypted Modbus-like vendor protocol, after which the aggregator obtained data from the VR-007.3 web server via HTTP
- Substation meter: via the Modbus TCP protocol
For the sake of comparison, we also set up reference meters, which were not accessible to the attackers. Connected to the same electrical circuits, these meters provided readings to the billing server directly over an RS-485 interface.
For easy viewing of all goings-on, next to the stand we put up a big screen with real-time display. The blue graph illustrated the readings from the aggregator. These readings changed based on the attackers' actions. The green graph reflected the actual (unaltered) amounts of power generated and consumed, based on the data from the reference meters.
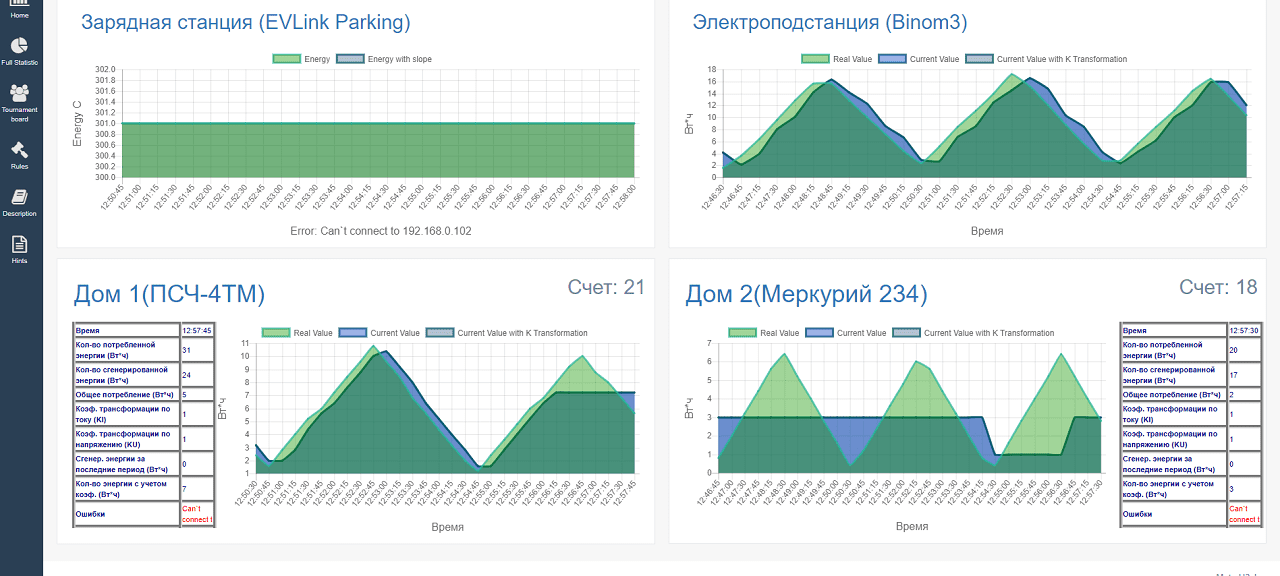
View of values for each building: account balance, power consumed, power sold to the grid, and rate
The stand network had an internal portal for contest participants. This page displayed the most up-to-date graphs, descriptions of each part of the stand, contest rules, and even occasional hints.
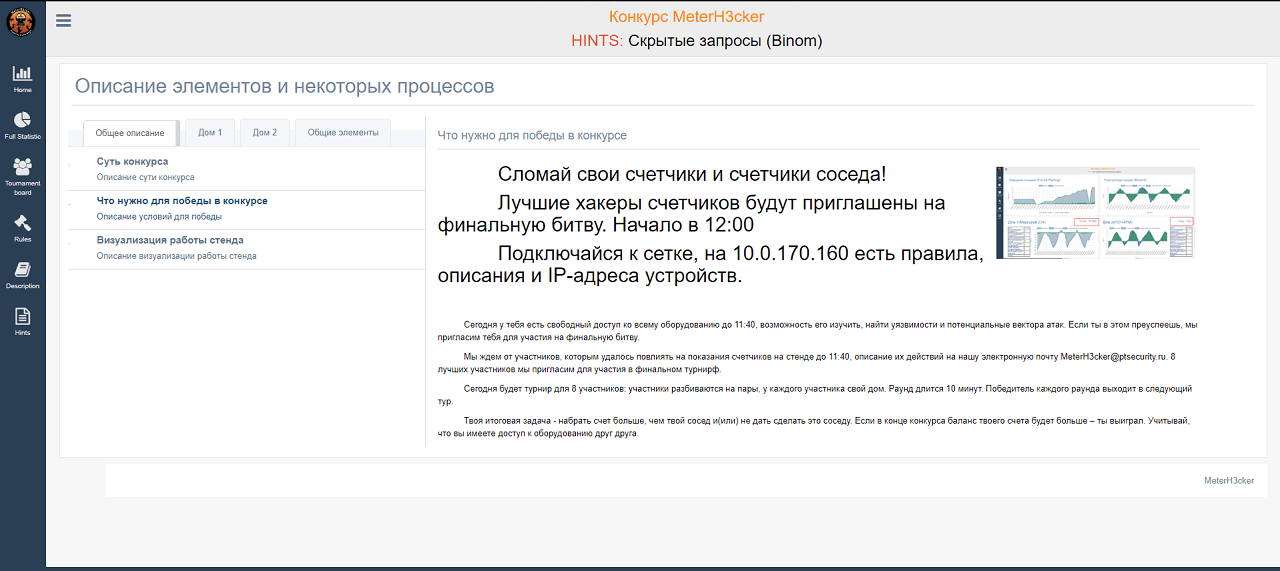
Internal MeterH3cker portal
Format and rules
The contest took place over two days. Preliminary rounds were held on the first day. By connecting to the stand network, each participant obtained access to all equipment in both buildings, the substation, and charger station. The participants had the opportunity to closely study the equipment, find vulnerabilities, and design potential attack vectors. Throughout the day, occasional hints on the contest portal pointed to weak spots in the equipment. The most successful competitors from the first day were invited to return for the finale on the second day.
The finale was a sort of duel: two participants were invited up at a time, each being responsible for one building. Their objective was, in the space of 10 minutes, to use all possible methods to fool the meters and generate more energy than their "neighbor." The winner was the participant with the higher account balance at the end of the 10 minutes. Spicing things up was the fact that participants had access to their opponent's equipment. As a result, improving one's own score, as well as sabotaging the score of the other participant, were both viable strategies.
Day 1: preliminaries
There were plenty of eager participants, some of whom had seriously prepared for the contest and obtained all the necessary software in advance. A contingent from Japan carefully studied the stand from the opening hours of the contest, which helped them to obtain impressive results on the second day.
A big surprise came in the form of a 12-year-old hacker, who, in spite of his age, got the hang of the equipment and demonstrated several attacks.

Happy hackers
.
The first results were in by midday. The Japanese participants combined forces and sent commands via a web interface, with which they took control of the charger station and stopped cars from receiving power. Soon after they succeeded in bruteforcing the administrator password for the solar charge controller and thereby disabled generation of power.
The previously mentioned young hacker forced the aggregator to constantly reboot, effectively causing denial of service and interfering with meter polling.
Closer to the end of the day, the participants from Japan succeeded in causing a large difference in values between the reference meters and the hackable meters. As a result, the building balance changed dramatically. They also discovered a vulnerability in the web interface for the substation meter, which allowed reading the contents of the files on the device's flash card; one of the files contained the hash of the administrator's password. Successfully bruteforcing the password enabled obtaining access to the meter configuration.
In the closing hour, one hardy soul by the name of Oleg came up and, despite the limited time remaining, pulled off an attack that landed him a spot in the finals on the next day.
By the end of the first day, all participants were able to change the readings on all the electrical meters and control the various devices, including controllers and charging station.
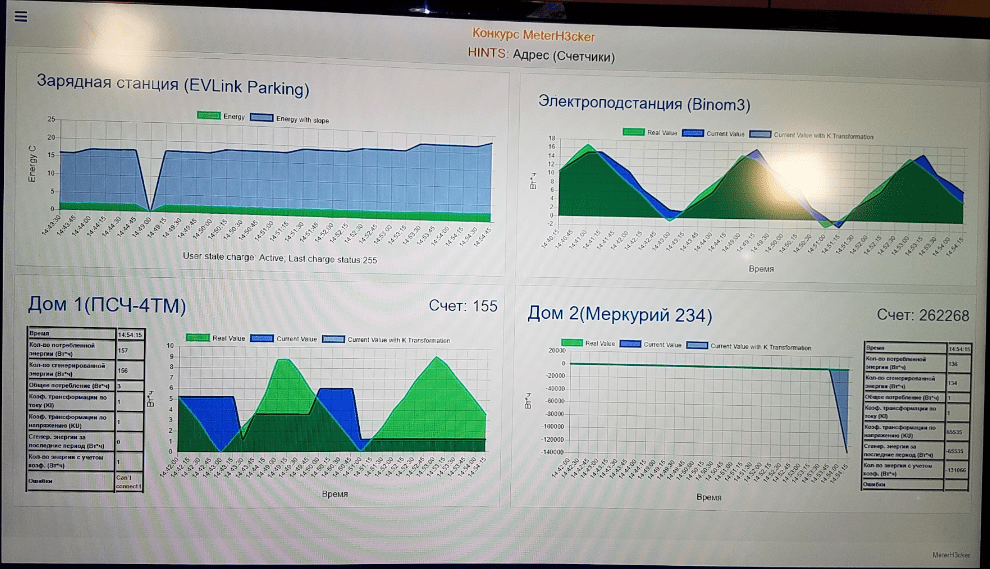
Results of attacks on the meters: the lower-right graph shows a change in the meter rate, while the lower-left graph shows a successful denial of service attack
Day 2: tournament and finale
Based on the participants' descriptions of their successes by the end of the first day, we selected seven participants who had been able to find and exploit vulnerabilities in the stand equipment.
Since our hacker-vs.-hacker rounds on the second day allowed fiddling not only with your own meter readings, but with those of your neighbor, any distraction or slip-up could be disastrous. When attacking his neighbor, Oleg accidentally boosted the neighbor's account because the attack took place during the neighbor's power generation phase, and he was unable to run down the amount in the other direction. Subsequent competitors took this lesson to heart by maximizing the coefficients on their own meter during the generation phase (daytime) and minimizing them during power consumption (nighttime).

Tournament table
The finale was rather dramatic. Satoru Takekoshi quickly seized the advantage with an attack that gave a big boost to his balance. His opponent, Alexey Kuznetsov, performed an attack of his own to much smaller effect. The gap in the readings for generated energy was 25 GWh versus 5 GWh. Scores remained unchanged for most of the remaining round.
Perhaps to avoid the painful experience already mentioned, when an attack backfired and ended up boosting the target's score because of poor timing, Alexey was more cautious and kept a close eye on day/night. In the second half of the round, he successfully attacked the substation meter, quickly coming up from behind. And then, in the closing seconds, Alexey again attacked his own meter and made the readings jump. This was enough to snatch victory. With an account balance standing at the equivalent of $92 billion (thanks to his successful substation meter attack), he walked away the winner.
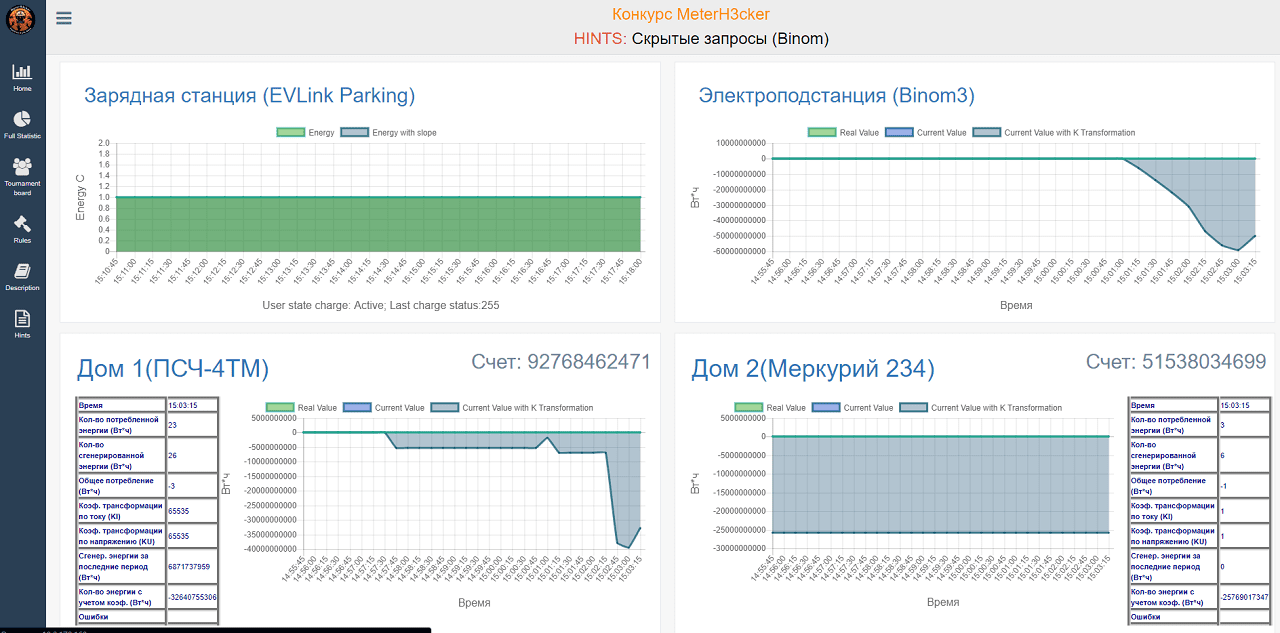
Account status in the closing seconds, after the final attack
Results
The winners were: Alexey Kuznetsov in first place, Satoru Takekoshi in second place, and Nikita Stupin in third place. A special prize for fourth place went to young hacker Yury Grishin.
Participants pulled off some ingenious attacks, especially during the final rounds. Most tried to attack meter readings, increase power (when it was being generated), and reduce power (when it was being consumed). In some rounds, the participants successfully attacked the charging station for electric vehicles and the solar charge controller.
However, nobody was able to pull off an attack on the aggregator and tamper with data on the aggregator itself. Such attacks could have given free reign over the information sent to the billing center, thus allowing boosts of absolutely any size to account balances. During the two days, we saw only one (unsuccessful) such attack attempt.
Nor were any attacks made on the HVAC controller. We had expected that an attacker would connect to the device and control the equipment using existing management signals. The main difficulty for attackers, however, was to correlate open ports with equipment names in order to, say, request information via the FOX protocol. Special software was not needed for such an attack. The hint from the organizers went unheeded—all attackers would have needed to do is spoof their browser's User-Agent header in order to connect successfully.
Other observations. The participants asked a great many questions about the stand's structure, functioning, and devices during the contest. The reason was that besides merely hacking devices, participants needed to figure out what each of the devices does and whether it's possible to exploit that particular device for profit.

Day 1 in full swing
The contest may be young, but we were delighted to see the interest of bystanders. Many of them wanted to know everything about the workings of the stand and participants' accomplishments. The beanbag chairs were all quickly taken!
We also want to commend the Japanese participants for their particular tenacity. The internal portal for the contest, as well as documentation for Russian devices, were only in Russian. This hardy bunch had the practical skills to demonstrate a whole range of successful attacks nonetheless. (That said, they did admit that the language barrier got in the way at times.)
Overall, the contest succeeded in showing that two days is enough time to get a good grasp on modern power metering systems and perform successful attacks on them.