PHDays 8: cash-hungry hackers refuse to Leave ATM Alone
5/30/2018
Positive Hack Days 8 continued a number of fun traditions from past years, among them the Leave ATM Alone contest. All comers were invited to hack two ATMs provided by our Banking Security partner Alfa Bank (to make things easier for hackers, we specially configured and hid vulnerabilities on the ATMs prior to the contest start). Participants had 15 minutes to bypass security and cash out. Around 40 participants tried their luck, with a total of 40,000 rubles at stake. Leonid Krolle, the Positive Technologies banking security researcher in charge of the contest, told us about the twists and turns that followed.

Leave ATM Alone contest participants
There were two ATMs for participants to attack. One of them was protected by application control software from our partners. This software prevents launch of untrusted applications, including those needed for withdrawing cash (that would be you, Cutlet Maker, BubbleMaker, and nemagiya!).
The second ATM was connected over a network to a processing center (an emulated one, that is). So the processing center would allow withdrawing any cash that is present in the ATM—but the catch is that the processing center would send a signal for dispensing cash from an empty cassette. So attackers would need to forge a reply from the processing center in order to withdraw cash from the non-empty cassette.
Network cables joining the ATM and processing center were visible. Participants could connect to them using a standard network cable (LAN).
And it might go without saying… but participants got to keep any cash they could take!

ATMs, too, can feel lonely and ignored
Application control
There are several ways in which application control software can determine whether a particular application has been whitelisted. Methods include verifying the path to the executable, checking its hash, and looking at its digital signature and extension. By blocking applications by default (unless they are explicitly whitelisted), this software offers additional protection for client computers and isolated systems, such as ATMs, intended to have limited functionality.
A blacklist of extensions is fairly cut-and-dry to make, plus easy to configure. But figuring out a whitelist (allowing files with only certain extensions) is much harder: whitelists are usually too broad, since they tend to include all pre-installed applications, even non-essential ones.
A number of methods have been published in recent years for bypassing application control with the help of built-in Microsoft Windows features (such as rundll32 and regsvr32). Simply blocking them would prevent Windows from operating normally. Such issues make application control a delicate and complex task. At Leave ATM Alone, participants' job was to tear down the results of such work. In the real world though, attackers would not have so much time at their disposal to bypass application control.
Day 1 of the contest
A steady stream of visitors—over 40 in all—kept the ATMs busy on the first day, as they attempted to bypass application control and forge ATM processing messages.

The first participants
A total of 15 minutes was given for bypassing protection on the ATM with application control installed. Participants' task was to run their own code before time ran out. Alas, all exploit attempts on Day 1 were unsuccessful. However, one observant participant discovered a strange device installed on the ATM. This, of course, was a skimmer: a small portable data reader similar to those that real-life criminals attach to ATMs. Skimmers steal card data (including PIN codes) by reading everything on a card's magnetic stripe.

Skimmer
After discovery of the skimmer, the challenge was to extract card data from it. Organizers had previously written a dump of a non-existent card to the skimmer, including the card number.
How did we make the skimmer? A skimmer consists of a magnetic reader head and audio recording device (some skimmers even have Wi-Fi or Bluetooth). Our skimmer was made from an Explay music player with microphone. Other USB microphones would work as well: http://www.chucklohr.com/usbaudiorecorder/. Thanks to its diminutiveness, the player nicely fits into the ATM panel and even leaves space for the battery. We then brought our mini-Frankenstein to life by testing a similar device on a different ATM model. To save space, we removed the USB port attachment, necessitating that we make our own USB adapter.
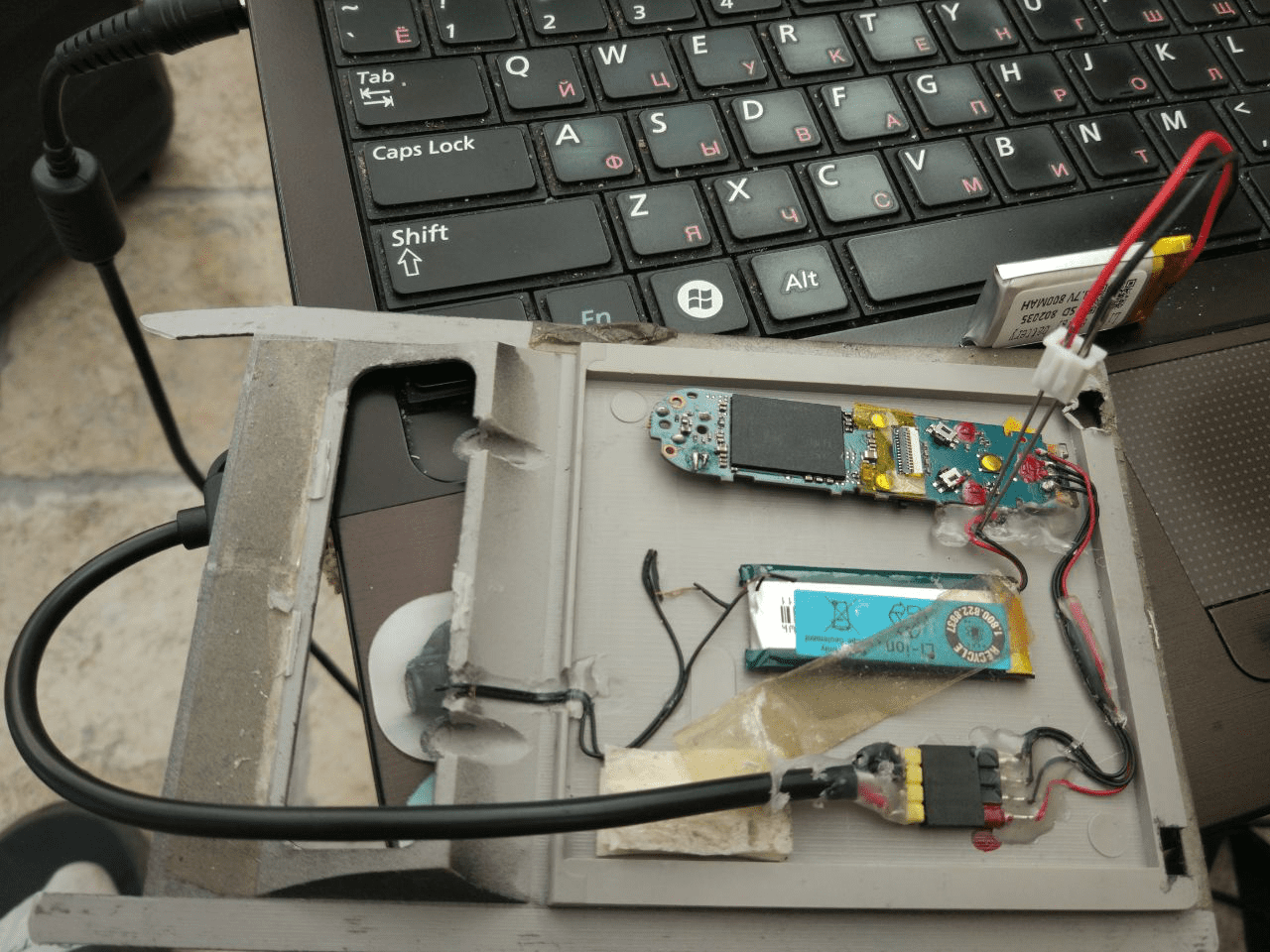
Beauty is in the eye of the beholder
To make sure that our player/skimmer turned on correctly, we had to consult the player manual online (since we had removed the player from its body, there was no way to tell the buttons apart). Then it was just a matter of recording the card information to the skimmer for participants' hacking pleasure.

Card with liberally sprinkled magnetic powder
Information on the magnetic stripe is recorded using frequency/double frequency (F2F) encoding (learn all about it here), consisting of alphanumeric characters in 7-bit encoding or numeric characters in 5-bit encoding. Read errors are detected with parity checking and a longitudinal redundancy check (LRC).
Data on any track should start with "start" and end with "end". These keywords have been chosen such that they allow determining the start of a data block, the direction of card reading, and even the encoding used (5-bit or 7-bit).
Control characters are intended for hardware commands, and cannot be used to transfer or store information. Card data fields have dividers in between them.
In the 7-bit encoding, reverse slashes (\) are reserved for country-specific characters and should not be used in international data exchange. The pound sign (#) is reserved for graphics.
Here is an example of how this might look on a standard ISO 2 track:
;XXXXXXXXXXXXXXXX=YYYYYYYYYYYYYYYYY?Z (37 characters),
in which X…X is the 16-digit card number and Z is the LRC (data lies between "start" and "end")
Testing the skimmer and writing the dump to it
Data can be copied from a player as an MP3 file. To make use of the data, you then need to find where the track is recorded, blow it up in an audio editor, and go through it bit by bit. But there are easier ways.
These include:
- SWipe, an application for reading magnetic stripe cards over an audio port.
- Magnetic Stripe Decoder, a program to decode a magnetic stripe card by receiving raw data from the magnetic stripe via the sound card.
Such methods allow, more or less accurately, decoding audio tracks into ASCII.
About an hour later, the card data written to the skimmer was provided by one of the participants. So a well-deserved prize found its owner, Maxim Vikhlyantsev!
Meanwhile, the remaining participants continued battling for the other prizes—the papery ones stored in the ATM cassettes. Some lost heart and gave up on their dreams of quick riches, while others kept on hacking. Overall, the first day was full of action, but by evening the organizers were still sitting pretty with their cash horde intact.

Day 2 of the contest

Dedication and persistence
Many of the first day's participants returned to take another crack. Their patient efforts to bypass protection were rewarded, as Stanislav Povolotsky broke through and ran unsigned code, winning the cash inside the first ATM.

Mission completed
But what about the second ATM? In essence, this ATM contained a laptop, which ran software to emulate a bank processing center.
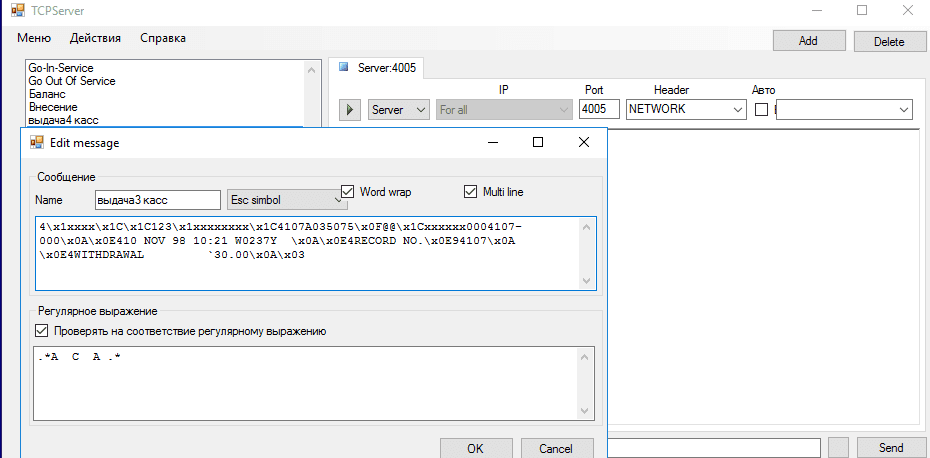
Processing center emulator
The emulator was configured to spit out cash for any inserted card, no PIN required. But the cassette indicated in the emulator's response was empty. To overcome this, it was necessary to complete several steps:
- Intercept the response packet from the processing center emulator.
- Modify the packet to contain the number of the other cassette.
- Insert a card into the ATM and, after a request is sent to the processing center, reply to the ATM with the modified packet.
- Use tcpdump, Wireshark, Scapy, or Ettercap to perform a replay or spoofing attack, in order to reply to the ATM with the modified data.
What are all these utilities?
tcpdump is a UNIX utility (with Windows clone) that allows intercepting and analyzing the network traffic that passes through the computer on which the utility is installed.
Wireshark is a fancier GUI version of tcpdump.
Scapy is an interactive shell and Python module for manipulating network packets.
Ettercap is a utility with extra functionality for analyzing the network traffic that passes through a computer interface. This is useful for man-in-the-middle attacks, which fool another computer into sending packets to the attacker, instead of to the intended recipient.
No changes here
This complex series of steps created challenges, but many of the participants rose to the occasion. The prize for forging the response on the second ATM went to the team сalled Information & Public Security Center Uzbekistan. Congratulations! A full list of winners can be found on the contest page.