PHDays CTF Over? PHDays CTF Goes On!
8/20/2012
In 2012 the PHDays CTF contest’s infrastructure was based on the principle of the King of the Hill game — the point were given for keeping control over the successfully attacked systems. This made the CTF contest even more intriguing — some important nuances of the hackers’ and information security specialists’ work were taken into account in the tasks, and many participants of Positive Hack Days really appreciated it. That is why an idea came to our minds… Why not to repeat the ‘royal battle’ separately for the Internet community, let us say, in the second half of August?
Dates
Everybody is welcome to try on the crown during the King of the Hill contest from the 20th of August to the 2nd of September
The cause for organizing the online battle is two hacking forums — in India and in Kaliningrad. From August 16 to 19 the experts of the Positive Technologies company at the SecurIT 2012hacking forum in Indiawill remotely carry out a workshop about the $natch contest. Also, from August 24 to 27 BaltCTF in Kaliningrad will welcome its guests. Participating in King of the Hill will give members of the of Internet community an opportunity to challenge professional hacker teams from France, Germany, Tunisia, Netherlands, and Russia.
Where to register?
To try to repeat the feats of the CTF battle participants and fight for prizes provided by Positive Technologies, please register at the official web site http://www.phdays.com/ctf/king/.
The detail of the King of the Hill contest is available at the http://www.phdays.com/ctf/rules website.
What is King of the Hill?

A real shooter for pentesters, which is as close to reality as possible. King of the Hill includes three information systems, which are exact duplicates of typical external perimeter of an average enterprise network. The perimeter of such an enterprise includes vulnerable web application and various services (administration interfaces, databases, etc.), and Microsoft Active Directory behind them (on the second level).
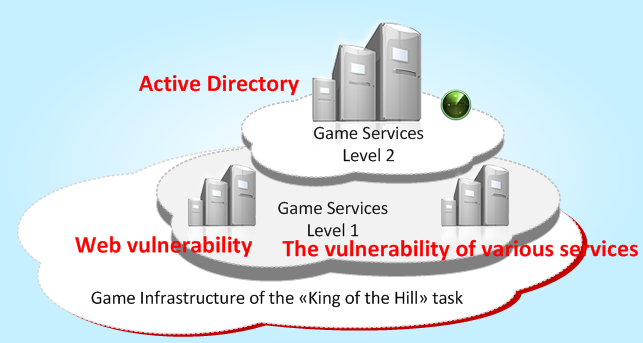
The aim of the participants of King of the Hill is to detect vulnerabilities of the systems, exploit them and, the most important of all, keep control over the systems as long as it is possible. The trick is in regeneration of the sets of vulnerabilities in the systems. The participants face a dilemma — whether to try to attack the neighboring systems or to proceed with vulnerability detection on the systems which are under control already. As in real life, the largest number of points is given for keeping control over Active Directory, since attacking AD requires keeping control over first level systems.
The King of the Hill contest was developed by the Positive Technologies experts and was presented for the first time at PHDays CTF 2012 as part of the hacking contest.