PHDays V Highlights: Signs of GSM Interception, High Time to Hack Wi-Fi, Future of Encryption
6/3/2015

Technological singularity is expected in 15 years at best, but Positive Hack Days transition is happening right now. The fifth forum had a record attendance – over 3,500 visitors, which is comparable to the leading international hacker conferences, and the number of talks, sessions, and various activities surpassed one hundred. The incredible and exciting contests involved hacking spaceships, power plants, ATMs, and railway companies. More Smoked Leet Chicken became the winning champion of this year’s CTF, showing their best at stock exchange speculation. Congratulations! A detailed write-up about that is coming soon. Right now let’s focus on a number of recommendations and tips that impressed us most of all during the 2-day hacker marathon that took place in World Trade Center on May 26-27.

Color of the Day vs Social Engineering
Chris Hadnagy, the founder of social-engineer.org, talked about his experience in business protection against social hackers during his speech called “Social Engineering for Fun and Profit”. One of his stories was about a pregnant girl, a social engineer by profession, who carrying a heavy box managed to get inside an office protected by various identification systems and penetrated its most critical part — a server room. Pregnant women look so vulnerable, don't they?
He also pointed out that while techniques change, people remain the same and there is no need to fight the very essence of human nature and become heartless robots. Instead, he showed how to turn it against social hackers. One of the ways is to implement the Color of the Day routine so the color would be known to employees only. When an adversary attempts to conduct a vishing attack pretending an IT or HR specialist, you just need to ask him or her the color of the day as a certain password to ward off impostors. You use ID cards to enter your office and it is all right to implement similar IDs for all access points.

Find Out Someone Is Listening on Your Phone
During his talk called “GSM Signal Interception Protection”, Sergey Kharkov described signs of wiretapping and all sorts of hardware and software diagnostic tools. For example, in order to make a connection, an attacker needs to make your device connect to his or her virtual cell, otherwise a phone might find a better alternative. So one of the sure signs that your device got connected to an adversary’s virtual cell is a strong signal and an unnaturally high C2 value responsible for prioritizing one cell over another.
PHDays V participants gave a lot of attention to mobile security. Dmitry Kurbatov, Positive Technologies expert, held a hands-on lab, after which anyone was able to participate in the MiTM Mobile contest and try to hack a mobile operator created for the contest. Participants could do a lot of things like intercepting SMS, USSD, and phone conversations, working with IMSI catcher, hacking encryption keys using kraken, and duplicating cell phones. Write-up of the contest highlights is coming soon.

Why Hackers Attack the Olympics
Among the participants of a round table dedicated to incident investigation in large infrastructures were Vladimir Kropotov, Fyodor Yarochkin, Kevin Williams, John Bambenek, and other infrastructure protection experts. For instance, Kevin as a British NCCU employee helped to protect the Olympic Games in London, while Vladimir represented Positive Technologies, which helped to protect VGTRK, a state television and radio broadcasting company in Russia, during the Olympics ’14. Fyodor Yarochkin noted that along with usual threats like hacktivists and hooligans came the most dangerous type of adversary — various forms of criminal business related to totalizators, as any change might help them to hit the jackpot. Kevin Williams discussed in detail the common practice in the UK to coordinate efforts with CERT, which act as a mediator between state departments and companies.

How to Help Intrusion Prevention Systems
Hackers have learned how to confuse self-learning mechanisms in the network intrusion detection systems. Clarence Chio, an artificial intelligence specialist, reviewed several models applied throughout IPS based on PSA, clusterization, etc. Which is better — rule-based techniques or machine self-learning mechanisms? Clarence Chio believes that ML techniques look good in theory, but when it comes to real life action they fail to impress.

The Most Secure Mobile Platform Around
The information security experts Denis Gorchakov and Nikolay Goncharov shared, among other things, information about the most secure mobile OS in their report called “Fighting Payment Fraud Within Mobile Networks”. The first place went to Windows Phone, for which any critical epidemics haven't been registered yet. As for iOS, there is a number of applications that attack devices with or without JailBreak. Android being the most popular mobile OS turned out the worst. According to Android Security Report 2015, the rate of malicious software found is 3 to 4 times above the average in Russia.

Edward Snowden in Your Keyboard
Not only may wireless keyboards discharge when you least expect it, they also have a potential to disclose your confidential data. Andrey Biryukov, a system architect for MAYKOR, told us about the concept of keysweeper — a simple Adruino-based device in a shape of a charger that hijacks signals from keys pressed on a wireless keyboard and sends the data to an attacker. Usual computer scanning will help you to detect viruses and vulnerabilities on your PC, yet it fails to protect against keysweeper.
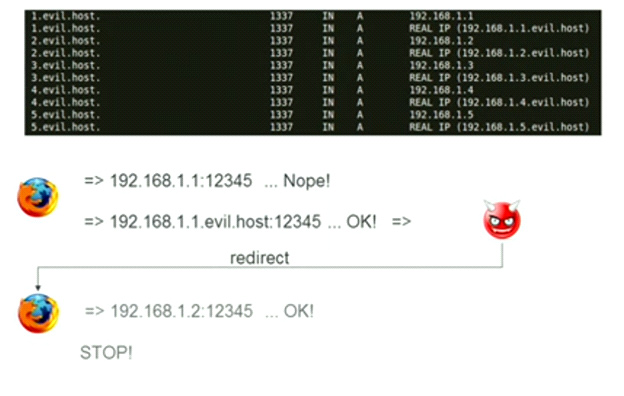
Victim’s Browser as a Scanning Tool
Dmitry Boomov, a respected deanonimization specialist, told the audience how to scan internal infrastructures via a victim’s browser without using JavaScript during his report called “Not by Nmap Alone”. All you need is to make a victim click on the right link.

Best Time to Catch Wi-Fi
In his report “Overview of Little-Known Wi-Fi Nuances”, the researcher Oleg Kupreev brought our attention to time and weather conditions most comfortable for hackers to strike. A high-frequency signal is weaker on rainy days, so a potential attacker will most definitely choose another day to attack thousands of users near the subway. It makes more sense to go on a DDoS hunt on WTS via mdk3 deep in the night. Not only it’s inconvenient to attempt it in the evening (the only channels that do not cross are 1, 6, 11), but also quite reckless – traffic overload every five minutes may raise suspicions if a victim watches TV online. Mornings, when office PCs are turned on, are high time to crack WAP Enterprise.

How to Make Vendors Patch Vulnerabilities
In March, FSTEC of Russia made its official vulnerability database, comprised of more than 150 threats and 10,000 vulnerabilities, public. Vitaly Lyutikov, the head of FSTEC of Russia, mentioned during the round table called "Expert Community's Role in Generation of Information Security Threat Databases" that the national database was a result of a law prohibiting Russian documents from referring to third-party CVE definitions. FSTEC of Russia is now responsible for checking zero-day vulnerabilities and vendor correspondence.
Onion Vulnerabilities
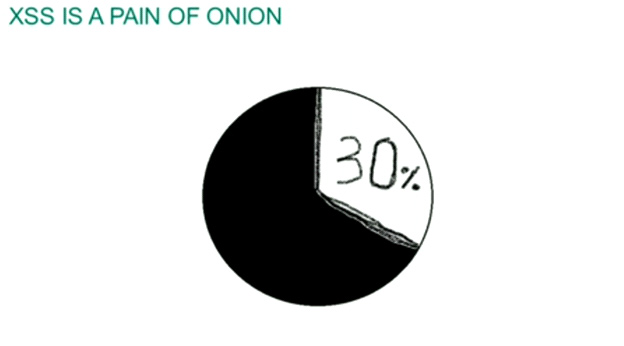
Protecting onion resources on DarkNet is not that easy. The Kaspersky Lab's experts, Denis Makrushin and Maria Garnaeva, told us what kind of information external users may get on a Tor user. Denis developed a passive system for Exit node traffic collection which had a key quality — it transferred traffic throughout the ports and contained a sniffer that was able to catch out all HTTP connections with the Referer header. If a person inside Tor clicks a link to an external web resource, this packet gets captured. The discovered sites usually contained ads about passwords and legacy databases. The authors of "The End of Anonymity on Anonymous Networks" also found out that every third onion resource has security flaws and allows for arbitrary JavaScript code execution.
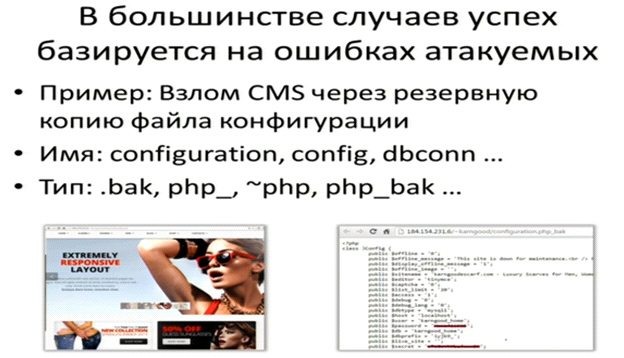
Hunting Lost Configuration Files
Hardly would anyone draw your attention for as long as Andrey Masalovich, the faithful participant of Positive Hack Days — in an hour the audience just couldn't stop listening to the competitive intelligence expert, so we had to extend the time of his talk "Zero Shades of Grey". Having shared one of his relatively honest ways to access website logins, passwords, and bases (figuring out the name of the backup copy of a CMS configuration file forgotten by a system administrator), he focused on a very important topic — doubting authenticity of multimedia, graphic and text data.

Below is a demonstration in France.

Check If Photos are Photoshopped
The contest held by Almaz Capital for startup cybersecurity projects touched upon data authenticity as well. In no rush for establishing a company, participants needed to provide a prototype of their solution.

The first prize (1,500,000 rubles) went to SMTDP Tech, a company that invented an anti-photoshop to detect photo and video changes. If you need to check a static billboard or car accident photos, this software may help.
Future of Encryption

Whitfield Diffie, the advisor for Almaz Capital, the father of digital signatures and asymmetric encryption made his forecast from PHDays plasma displays on May 26. He believes that if we were spending as much money on actual defense as we are spending on interactive attack systems we might get much better results, build digital fortresses and level up information security. Today quantum key distribution shows great promise for solving transportation problems, but nobody knows exactly how it'll look like. We can only assume that radio or vibro communication will be implemented. Another debated technology taken skeptically by Whitfield Diffie is homomorphic encryption — a user's computer might not be powerful enough to decrypt a message.
Linguists to Come Out of the Shadow
The session "Information Security: Careers of the Future", its moderator and Positive Technologies expert Evgeny Minkovsky along with business and government officers tried to foresee our future as well. What information security jobs and technologies will be most popular in five or fifteen years? Voting results at the end of the meeting surprised the participants — sooner or later information security will show high demand for linguists. Meanwhile, this point of view corresponds to the Atlas on New Professions by Agency for Strategic Initiatives that placed digital linguistics among the most promising professions. These specialists will develop semantic translation and text processing systems and new communication interfaces between PCs and human beings.

You may find videos of all the PHDays reports at the forum’s site http://www.phdays.com/broadcast/.