PHDays V: How to Create Your Own Shodan, Find ROP Shellcodes, and Automate Reverse Engineering
4/29/2015

The fifth Positive Hack Days international forum on practical security will take place in Moscow World Trade Center on May 26-27. With the second wave of Call for Papers finished, we present a new portion of reports.
Automation: Reverser’s Helper
Reverse engineering often implies thorough analysis of an application system code, and the star tool here is a disassembler. Researchers encounter various difficulties — from deciding on an order of function processing and differences in system versions to inability to fully debug and emulate the code in built-in systems.
In his report Anton Dorfman, who presented a workshop on mastering shellcode at PHDays III, will share his experience in creating a reverse engineering plugin based on IDAPython, which is capable of conducting primary automated code analysis and transferring results from a currently researched system to its other versions.
How to Create Your Own Shodan
The acclaimed international security specialist Igor Agievich will cover the topic of creating a search system identical to “the world’s most dangerous search engine” — Shodan.
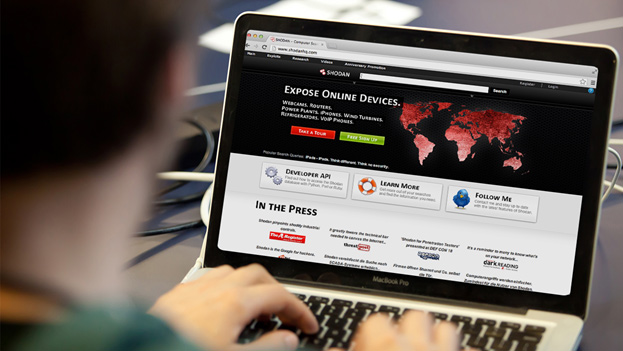
The speaker will compare the developed system to its counterparts and give examples of curious devices detected by the new search engine.
Catching ROP Shellcodes in Network Traffic
Remote vulnerability exploitation is one of the most powerful tools attackers have in their arsenal — this is how worms are spread and sensitive information is leaked. In order to bypass security, attackers developed a shellcode-constructing technique using return-oriented programming. The new type of shellcode was called ROP shellcode.
The former participant of the CTF team Bushwhackers Svetlana Gayvoronskaya will present a utility that conducts static and dynamic network traffic analysis for ROP shellcodes. Last year Svetlana together with Ivan Petrov presented a report on shellcode hunt for ARM.
One Month Left Until PHDays
The fifth Positive Hack Days international forum on practical information security is coming up. The arrangements for PHDays V are in full swing. The organizers are putting together the competitive program and presentation schedule. You may find the previous announcements on our website (1st and 2d).
In the near future, we will publish on the site the full list of speakers including abstracts. Follow our newsfeed and you will not miss all the juicy stuff.

Even now you may vote for the most interesting presentations — click on “Want to visit” near the report of your choice on the forum program page. The voting will help us to make the correct arrangements for meeting rooms based on their sitting capacity.
You still have the opportunity to join PHDays V but do not linger — only few tickets are left.
See you in May!