PHDays VI Life Stories: How Moxie Marlinspike Defeated FBI and John Bambenek Sniffed Out Number One Hacker
5/4/2016
In early April, all the largest mass media worldwide talked about Moxie Marlinspike — a billion of WhatsApp users are now end-to-end encrypted by his Signal Protocol. In a month only, on May 17 and 18, you will have a chance to learn from Moxie at PHDays VI. Along with Moxie Marlinspike, Rahul Sasi, Paul Vixie, John Bambenek, and Andrey Masalovich will share their professional experience.
Obama and Cameron against Marlinspike

Born in 1980, Moxie was officially named Matthew Rosenfeld. In the late 90’s, he moved to San Francisco. The sea and hacking are two life passions that predefined his pseudonym: Marlinspike means a tool used to separate strands of rope or wire, and Moxie is a synonym of boldness.
His personal website is called thoughtcrime.org, an Orwellian term, not by chance. When in 2009 he developed an online service WPA Cracker and MitM attack SSL stripping,, intelligence agencies turned their attention to him. From now on, he was specifically thoroughly inspected at airports. His phone number was then found in the contacts list of Jacob Appelbaum, a WikiLeaks’ activist, so the pressure on Moxie only doubled. Once, he и had been kept at an airport for several hours with all his devices confiscated.
Intelligence services seemed to fool around turning Marlinspike angry. Together with Stuart Anderson, he founded Whisper Systems in 2010. Their products, a protected message exchange system TextSecure and call encryption program RedPhone, were top-ranked by security specialists. They were free of charge and ran without errors. However, Twitter bought the company in 2011, and the development of these products died out. Marlinspike merged with Twitter as the head of information security only to leave the company in a year and a half and bring his pet project back to life. He established a non-profit organization Open Whisper Systems and moved on with the development of TextSecure and RedPhone. Fortunately, Twitter decided not to interfere and allowed these applications to be publicly available.
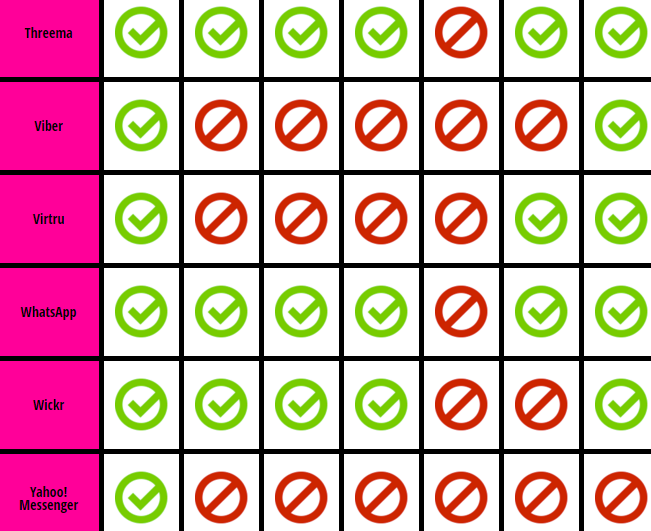
Today, both products are substituted with the messenger Signal suitable for iOS and Android. It is recommended by Edward Snowden and Electronic Frontier Foundation. In the EFF rating, it won seven points out of seven. Compare it with Skype that scored one point only or Telegram with four points earned.
In December 2015, Pavel Durov, responding to Snowden’s and Marlinspike’s retorts on how Telegram’s defaults are dangerous, claimed that an average user of Telegram prefers synchronization to encryption. Secret chats keep encryption keys on a device instead of on a remote server, so that is why they cannot synchronize via a cloud.
Until November 2014, WhatsApp had two points out of seven in the EEF rating. Now, when they started cooperating with Open Whisper Systems, they have six. However, some politicians did not perceive this news positively. Barack Obama mentioned it as a problem, and David Cameron promised to prohibit WhatsApp. Since April 5, 2016, every WhatsApp user is encrypted end-to-end. Now the owner of the messenger cannot give away any data to intelligence services even if requested: no video, voice traffic, chats, or photos.
When young people ask Moxie about how to get started in their software or security career, he advises them not to hurry. “A friend of mine,” Moxie wrote at Slashdot in 2011, “recently quipped "most people working in software discovered technology before they discovered themselves." If you're a young person, I think the very best thing you could do is get together with a group of friends and commit to a one year experiment in which the substantial part of your life will be focused on discovery and not be dedicated to wage work — however that looks for you. Get an instrument, learn three chords, and go on tour; find a derelict boat and cross an ocean; hitchhike to Alaska; build a fleet of dirigibles; construct a UAV that will engage with the emerging local police UAVs.”
Rahul Sasi: Artificial Intelligence to Stop Drone Hijackers

UAVs are interesting to another participant of PHDays VI — Rahul Sasi. Remember Interstellar when the lead character and his daughter hijack a UAV — this is what Rahul can do. In 2015, he developed the backdoor Maldrone to overtake control of Parrot AR.Drone 2.0 and DJI Phantom. Working together with the exploit Skyjack, Maldrone can hijack drones, intercept video signals, and propagate his “flying army” infecting neighboring drones. By the end of 2016, the number of UAVs in the USA only will have reached 2.5 million. This is a good argument to look closer at Rahul’s research.

At PHDays VI, Rahul Sasi will talk about his other project — a security automation system based on artificial intelligence. Many traditional security scanners used for web applications cannot оdetect logic errors. The speaker will showhow to use machine learning technologies to design a tool that discovers such errors. Some more details are available in The Register.
John Bambenek: How to Find a Number One Hacker

Black hats shoot not only the rich and strong. At BlackHat USA 2014, John Bambenek described a tragedy that happed to a Romanian man. He killed himself and his 4-year old son because of a ransomware he received after visiting adult websites. This “police impersonation” malware instructed him to pay a massive fine or else go to jail for 11 years.
In his interviewfor The News Gazette, Bambenek mentioned that his greatest achievement up to date was participation in Operation Tovar. In June 2014, a group of 150 specialists from 13 countries managed to detect a possible organizer of the most dangerous hacker teams in history — Evgeniy Bogachev. Born in Russia, also known as lucky12345 and slavik, he stole almost $ 100 million from the U.S. citizens and companies. He is also indicted to be behind GameOver Zeus and Cryptolocker. “Bogachev and his criminal network implemented the kind of cyber crimes that you might not believe if you saw them in a science fiction movie,” said Leslie Caldwell, an attorney involved in the case. In 2016, the FBI included Bogachev in the list of the most wanted cyber criminals and offered a $ 3 million reward for his capture.
John Bambenek first tried to write a computer program when he was six and conducted his first hacker research before he went to college. The U. S. Air Force paid for his education, but he could not proceed with the military career because of a serious knee injury he suffered during a hiking trip. So he started as a project manager in Ernst & Young (he might even have shared the same canteen with Jan Koum, the founder of WhatsApp, who worked for Ernst & Young at that time).
Along with hunting cyber criminals, John Bambenek helps school children in Tanzania via a charity fund he established; he likes steaks and has four kids.
John compared сhis visit to Moscow in 2015 (he spoke at PHDays at that time) with an explosion. We hope this year visit to PHDays will be no less emotional. John will concentrate on how to detect cyber criminals via peculiar features of the infrastructure those criminals create. His advice on how to protect yourself from ransomware is available at the website of SANS Technology Institute.
Paul Vixie: DNS as a Defense Vector

Paul Vixie, the founder of Internet Systems Consortium, will also visit Moscow this spring. For pioneer achievements, he was named to the Internet Hall of Fame in 2014.
He has been contributing to Internet protocols and UNIX systems as a protocol designer and software architect since 1980; wrote Cron (for BSD and Linux) and is considered the primary author and technical architect of BIND 4.9 and BIND 8. He has authored or co-authored a dozen of RFCs, mostly on DNS and related topics; earned his PhD from Keio University for work related to DNS and DNSSEC.
During his talk, Paul Vixie will show how to secure DNS and use it to protect other targets of local and global Internet. He will focus on DNS spoofing, domain name system security extensions (DNSSEC), DDoS attacks, rate limiting, DNS firewalls, and passive DNS monitoring.
Andrey Masalovich: Looking for Aircraft Carrier on Google

Presentations of a lieutenant colonel of the Russian Federal Agency of Government Communications and Information, Andrey Masalovich, are far from typical reports on information security. They are colorful shows where the audience watches a vulnerability being exploited at the Pentagon website or a secret Chinese aircraft carrier deliver its cargo. “I’m not an Olympic champion or master of sports. I’m a first-rate sportsman,” he told to Forbes. His stories are so fascinating that the audience always asks to prolong his talk (this also happened at PHDays V).
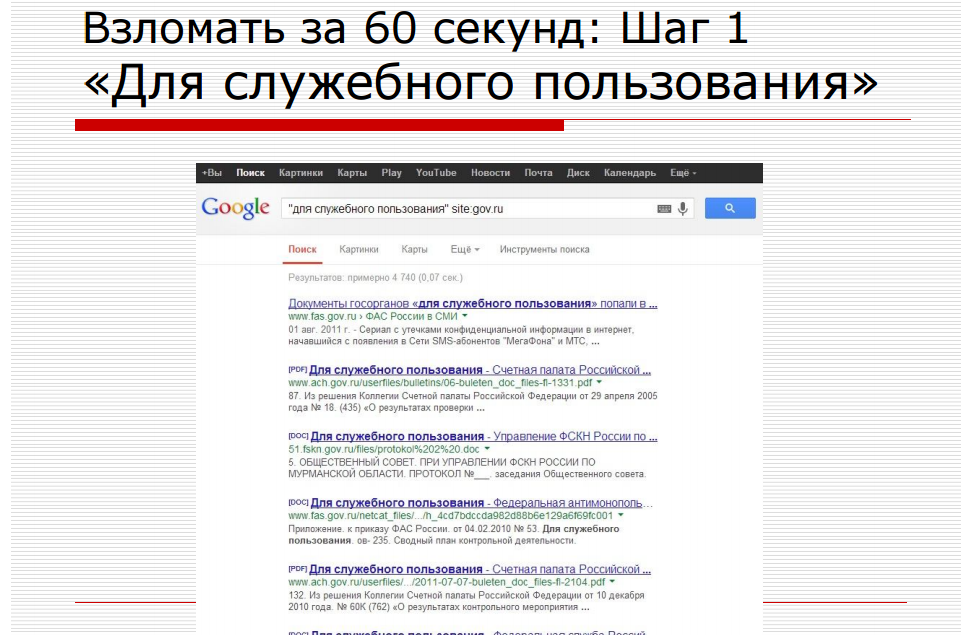
In 2014, his «Life After Snowden» was among the most frequently cited talks on the social networks. Particular attention was paid to the section “Documents” on Vkontakte where scans of personal documents can be found.
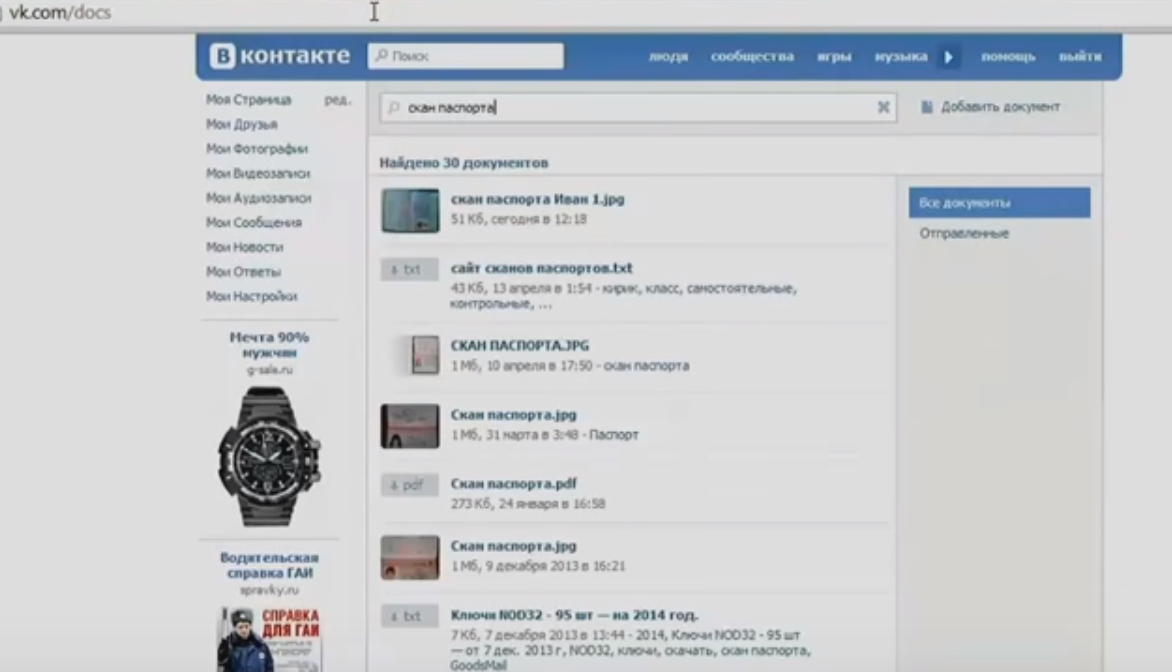
Studying of Pentagon tender documents right during his talk at PHDays wasn’t passed over by American intelligence agencies. A distinguished scientist, awarded a scholarship by the Russian Academy of Sciences, was included into the FBI base of dangerous cyber criminals as a lead hacker.
For the last two years, he has been focusing on detection and prevention of malicious information influence. His talk «The Revenant» is in top five most expected presentations at PHDays VI. The speaker will talk on how information attacks are developed, how to detect them at an early stage, and how to resist them. He will analyze the perception of information and the diffusion of information in social networks by using bots and trolls. His talk will also include a quick social test of common participants of mass discussions — common users, politicians, media people, teenagers, recruiters and their victims.
On May 17 and 18, Moxie Marlinspike, Rahul Sasi, Paul Vixie, John Bambenek, Andrey Masalovich, and many other renowned infosec experts will share their knowledge with PHDays VI participants. You can study the programof the event and find the best way to visit the forum at our website phdays.com