Positive Hack Days CTF 2012, or Hackmageddon
6/18/2012

In the 19th century, carefree people who used to treat migraine with craniotomy, cough, with heroine, and other illnesses, with mercury, came to believe in the almighty Genetics. However, the long-awaited triumph of biotechnologies turned into a global catastrophe. The plot of the Russian major hacker contest, PHDays 2012 CTF, set an ambitious task for the participants, who had come from all over the world: to save the Earth Civilization, fairly beat-up and dying of starvation amidst mutants and giant weed-trees.
The battle between hackers based on the Capture The Flag model has become the star turn of the PHDays 2012 program: for two days and a night non-stop 12 teams from 10 countries were breaking rival networks and protecting theirs.
PHDays CTF conditions, unlike those of other contests of this kind, were as real as possible: the vulnerabilities used for the competition are common for modern information systems. Besides, the participants were allowed to take blind actions when solving the tasks. In other words, they could attack systems that they had no access to. The most curious feature of PHDays CTF 2012 was the King-of-the-Hill scheme used at the heart of the contest. According to the logic of this scheme, a team scored not only for having captured a system, but for having held it down as well.
For the conditions to be as real as possible, the King-of-the-Hill scheme copied a typical arrangement of enterprise networks: the external perimeter was made of web applications, DBMS servers, and various catalogs (LDAP) and, if penetrated, gave access to the internal perimeter – Microsoft Active Directory. Everything was the way it is in real life.
The Show
To add a special flavor to the competitions, we prepared a game infrastructure and were modifying it throughout the CTF according to a single plot line. So, the participants were not only to complete tasks faster than their competitors, but to save the world! (For the legends of Day 1 and Day 2, visit the forum’s web-site).
Besides, this time the show was spiced with an element of a reality show: random visitors were given cards with bonus keys that they could present to their favorite team at the end of the second day.
Challenges
The competitions were not only about “pure” hacking. In the lobby of Digital October, the organizers mounted an enormous container with “litter”. The CTF contest required the teams to dive into the container (dumpster) and find bonus keys (flags). Each team had 30 minutes to do the Dumpster Diving.

The second day of Positive Hack Days prepared new surprises for the CTF participants. First, they had to take over an aircraft AR.Drone operated with a mobile phone via an insecure wireless connection. The contestants had 30 minutes to win the competition.
The weather on the 31st day of May was not quite warm and sunny, so the Drones were launched indoors, right next to the dumpster.

Not only did the winner score extra points to their team, but took the drone home as a prize. The quadrocopters went to Sergey Azovskov from HackerDom (Russia) and Matt Dickoff from PPP (the USA).
Yet, there was even more to come. The Way To Protect Money section offered the $natch competition composed of three parts. The first one required participants to take out money from a remote banking system specially developed for this occasion. The second part was meant for the CTF teams, who had four hours to enhance the security of the banking system. Finally, contestants of the online HackQuest joined the game to attack the system and steal the money from bank accounts of the CTF teams.

The CTF contestants managed to win the battle and save almost all their money.
Results
The best team of Positive Hack Days CTF 2012 proved to be LeetMore (Russia). Last year they were second, but this time they gave no chances to their rivals and took the main prize – 150,000 rubles. The second place was taken by a Swiss team, 0daysober (100,000 rubles), followed by Int3pids from Spain (50,000 rubles). Last year’s favorite PPP (the USA) became the fourth. The final results are provided in the table below:
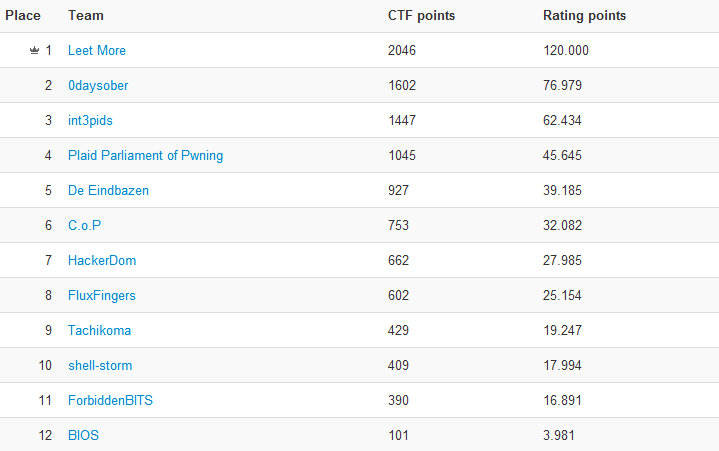
Tachikoma from Japan deserves a special mentioning. The team was comprised of students of four Japanese universities who participated in such a contest for the first time. The whole country was cheering for the guys, and they did a good job for novices.
0-day
The CTF wars helped to reveal a few quite interesting vulnerabilities. For example, the LeetMore contestants detected a 0-day in the FreeBSD 8.3 release (a local vulnerability that allows bypassing security restrictions). By exploiting this vulnerability, anyone could have broken the security mechanism and deleted the flags of other participants. However, everyone played fair J
Another vulnerability was found by Eindbazen (the Netherlands). They discovered a vector of XSS attack on the King of the Hill. Since this web attack had not been foreseen by the CTF authors, this vulnerability can be considered as a 0-day.
Defcon, Alas!
Unfortunately, Defcon refused to put off its CTF qualifications. It’s quite understandable that, having fought in PHDays for two days non-stop, 12 best teams were physically incapable of taking part in the qualifications: some of them were on their way back home; others were literally exhausted.
Anyway, everything was great! We’ll do our best to make PHDays CTF 2013 even more exciting!
P. S. For those who are interested, the full version of the CTF legend (text+video) and links to feedbacks on the forum can be found in a personal blog of one of the organizers.