Show Me the Money! The $natch Competition at PHDays 2012
6/27/2012

How to Protect Money, a section of PHDays 2012 dedicated to banking issues, ended like a good old thriller: the participants, who were discussing security issues urgent for the industry a minute before, found themselves witnessing a real bank robbery. Armed with laptops, the “criminals” were attacking a “bank” represented by a remote banking system, which had been developed by Positive Technologies specialists for the competition.
The participants of the $natch competition were to demonstrate their skills of exploitation of vulnerabilities common for remote banking services – rather logic than web ones (i.e. not like Cross-Site Scripting or SQL Injection).
Specially for the competition, we developed our own remote banking system from scratch and stuffed it with common vulnerabilities revealed by Positive Technologies experts in the course of security assessment of such systems. The solution called PHDays I-Bank was a standard Internet bank with a web interface, PIN code to access the account and a processing.
The day before the competition the participants received an image of an operating system with the installed remote banking (and its source code, of course) and a test base. Thus, they have a day to detect the vulnerabilities and write an exploit for them. During the competition, each participant got their personal login and password to the remote banking system and a real bank card bound with a specific account. The competition lasted for 30 minutes. The participants were to hack the base (this time – operational), transfer money to another account and then, use the bank card to cash out the money in an ATM waiting in for the winners in the lobby.

Though it was not officially announced, the money could have been stolen not only from the “bank” but from other participants as well J The balances were displayed on a large screen, so during the 30 minutes the guests could follow the game and know who had managed to ~~steal~~ get more money.
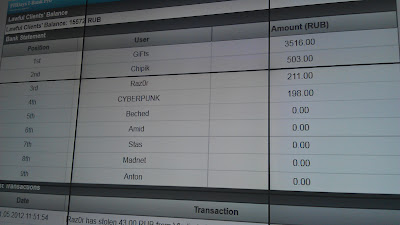
Finally, the competition was won by Gifts, who could take out 3,500 rubles, followed by Chipik (900 rubles). The third place was taken by Raz0r. The game was fair: ATM gave out all the amounts they earned.

CTF vs. Online HackQuest
Then it was time for the CTF teams to join the competition. Their task was to ensure the system’s security. The contestants were also given the image of the operating system with the remote banking, its source codes and the test base. They had 4 hours to detect and eliminate the vulnerabilities on the condition that the system functionality remains unchanged. In other words, the secure but not working system was not an option.
The role of hackers was played by the Internet users participating in the Online HackQuest competition. When they were granted a VPN access to the network, they had 30 minutes to attack the system and take out the money from the CTF teams’ account. Detailed description of the rules is published in our habrahаbr entry. In the end, the CTF teams snatched the victory: they managed to save almost all their money.
Both the participants and the on-lookers enjoyed the competition immensely and unanimously called it the star turn of the forum’s program. We already have some ideas of how to make the competition even more exciting and entertaining and will try to embody them in PHDays 2013. So, see you next year!
P. S. We’d like to point it out once again: the remote banking system used for the competition was developed by Positive Technologies specially for the PHDays 2012 competitions. It IS NOT USED in any real bank; though, it is as similar to the real systems as possible and contains vulnerabilities typical for such systems.