The Most Notable Moments of PHDays VI: Day One
5/23/2016
More than 3,000 people attended the Positive Hack Days information security forum during its first day. Moreover, 15 hackspaces across Russia, Bangladesh, Belarus, India, Kazakhstan, Peru, Tunisia, and Sweden threw their open doors to those who wanted to participate in the forum online. The forum was broadcasted on the internet.
About 50 reports were presented during the first day, hands-on labs and round-table talks were held, tens of hacking contests were launched.
The information security level has a tendency to decrease
Positive Technologies experts presented Positive Research 2016 on the forum. This analysis report reveals the decrease in information security in almost every sphere. The security of IT infrastructure of large companies still leaves much to be desired: in 46% of cases, an intruder with low qualification could get access to internal network resources. The most common vulnerabilities: the use of dictionary passwords (53%), vulnerabilities in web applications (47%) and service protocols (100%), inefficient antivirus protection (91%), out-of-date software (82%).
Mobile subscribers’ data is at risk, PT experts say. They investigated SS7 security last year and the results showed that in 89% of cases it was possible to tap SMS messages, in 58% to locate a subscriber, 50% to intercept calls.
Banks are still vulnerable. All of the tested systems contained vulnerabilities, 90% of them being critical. In 50% of systems lacked two-factor authentication mechanisms or they were implemented incorrectly. Mobile bank apps for iOs are more secure that ones for Android: 33% of critical vulnerabilities vs 75% accordingly.
Positive Technologies specialists detected more than 100 vulnerabilities in industrial control systems in 2015. Nearly half of these errors can cause service failure. Among the most vulnerable systems: SCADA, HMI, PLC, remote terminals, network devices, and engineering software.

Topical information security issues in terms of government protection, business, and teсhnologies, were discussed in the section “Face to Face: the Arbiters of Security”. Representatives of government and business, developers of information security tools, CIO and CISO of large companies participated in the talk, among them:
- Natalya Kasperskaya, CEO at InfoWatch,
- Vitaly Lyutikov, Russian FSTEC,
- Oleg Bosenko, CISO at Rosneft,
- Evgeny Krainov, CISO at Rosinmonitoring,
- Kirill Alifanov, Director for business processes and IT at E.ON Russia,
- Boris Simis, Deputy CEO at Positive Technologies,
- Dmitry Gusev, Deputy CEO InfoTeCS,
- Vladimir Bondarev, AT Consulting,
- Sergey Ryzhikov, CEO at 1C-Bitrix,
- Ilya Fedorushkin, CEO at Tizen Security Center.
Boris Simis set the tone for the discussion by raising a severe problem: security specialists suppress information security issues and do not bring them to the attention of their managers. Natalya Kasperskaya agreed with this statement. Boris Simis noted that it is impossible to build a reliable protection system until security specialists do not acknowledge that their system can be hacked.
The evolution of information technologies is much faster than the development of protection technics. It is possible to increase the world-wide security level only of government, business organizations, and IS experts join their efforts. Among those who responsible for information security, Vitaly Lyutikov named regulators, researchers, customers, integrators, and developers. For him, the general goal is to cut time the time between problem detection and localization.

During the section “Why We Hack: The Truth”, Boris Simis discussed with hacking community representatives the role of hackers in the evolution of information security. Famous Russian pentest experts participated in the talk: Dmitry Evteev, Timur Yunusov, Nikita Kislitsin, Omar Ganiev, and Sergey Belov.
Why is it actually possible to hack a large network in one or two days? People spend years and lots of money to build a protection system. However, a security analysis expert can penetrate into an intranet quite easy. Timur Yunusov, a senior expert of the department of banking system security at Positive Technologies, drew an analogy to a chess game: the only difference is that black moves first and security specialists are always one move behind.
There are competent people among both attackers and defenders, says CTO of HeadLight Security Dmitry Evteev. When he was working for Positive Technologies, Dmitry gathered a team of pentesters that became famous across Russia. “Imagine there is a company that is well-protected by passwords, tokens, firewalls, and antivirus”, Dmitry says. “Users appears in the network. And they complain about complicated password policy. An accountant wants to install an important program that won’t work with proxy. Gaps appear. Users start visiting malicious sites. IT specialists move from one computer to another, but do not succeed in solving those problems”.
Sergey Belov, an analyst at Digital Security, is sure that people just can’t choose the right team: “Instead of a couple of competent offensive specialists, they hire experts who know SDL but can only create pseudo-secure processes. This approach is wrong. I have never dealt with a company that was invulnerable to capturing at least one domain account by responder, nmap or Hydra”.
Nikita Kislitsin from Group-IB noted that it the security itself is not attached to a product you buy. Security means processes, culture, and people. “For a long time, I have been analyzed botnets that sent various data from infected computers: intercepted post requests, passwords, videos, keys that can be obtained from filesystems or USB sticks”, Nikita tells. “Recently, I have come across an infected computer of a system administrator in a commercial bank. The cause is obvious: he visited a social media site and followed links that were sent to him. A bank can buy an antivirus or FireEye for a million dollars, but it is still vulnerable. According to my research, at least one-third of companies (including large banks) is infected with botnets. Building a DMZ and protection of a perimeter take a back seat, because it is easier to infect an important computer by sending a virus”.

An interesting discussion about the press on information security took place during the forum. Deputy CEO at Positive Technologies Alexey Kachalin discussed with journalists and bloggers whether it is necessary to cover information security incidents for newspapers and how to make a protection tool out of mass media materials. Among participants: Alexey Lukatsky (a business consultant on information security at Cisco Systems), Sergey Vilyanov (Bankir.ru), Ilya Shabanov (Anti-Malware.ru). Sergey Vilyanov in his notable speech stated: “Security needs silence”. He believes that security issues should not be disclosed to public. Alexey Lukatsky raised the question: for what and foe whom a blogger should write. He offered to write about information security for housewives. He supposes that not only small and medium-sized companies are interested in IS issues.

Information security services organization was discussed at the section “Another Round of the Standoff: IS Services as a Response to New Threats and Challenges”. What threats require prompt involvement of experts? How do IS services work and what are the advantages of the combination of cutting-edge technological solutions and deep expertise? Representatives from Positive Technologies, Kaspersky Lab, and Solar Security tried to puzzled out these problems. Experts named targeted attacks as a major challenge. There is no universal tool against this type of attacks. Pros and cons of new services as compared to full-packaged products were discussed as well as service models that can be procured via outsourcing.
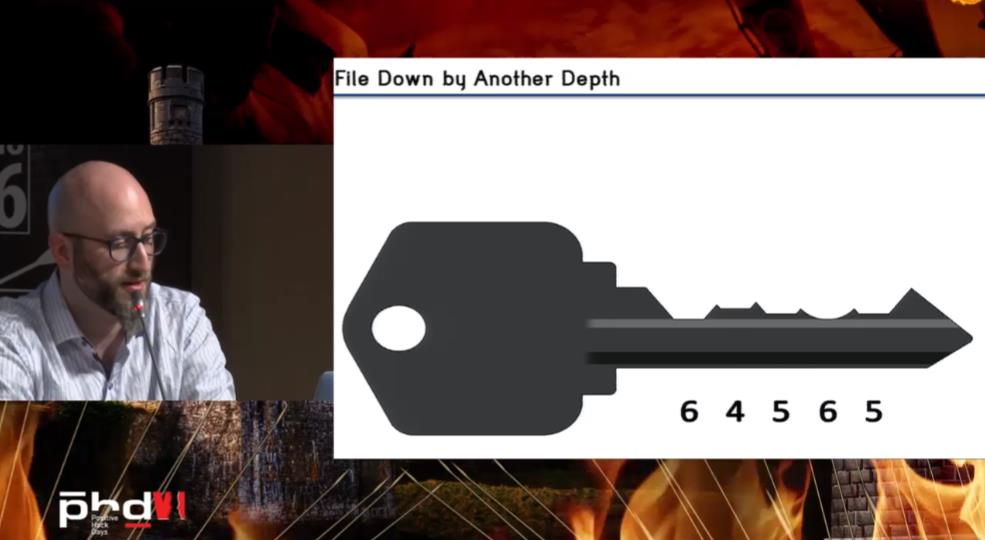
Babak Javadi, the president of the TOOOL division in the U.S., showed that any security is based on physical security. He told how to protect buildings against unauthorized access if a cylinder lock is installed on your door. TOOOL has 21 branch offices. They held conferences and hands-on labs where they demonstrate how to break locks. “If I can physically access your firewalls and servers, software protection methods won’t help. If you bought your locks in a supermarket, the whole data center security system is useless”, says Babak.
You can watch the record of the section “Janitor to CISO in 360 Seconds: Exploiting Mechanical Privilege Escalation” on the forum’s site and learn how to prevent lock breaking and to create keys with different priviliges.
Terrence Gareau, a recognized expert in DDoS attack mitigation, prevention, and recovery, spoke at PHDays for the first time. He told participants how to develop a honeypot network that will extract valuable information from the Internet and produce a data feed that can be used to protect online assets with Kibana, Elasticsearch, Logstash, and AMQP.
Terrence Gareau is Chief Scientist at Nexusguard. For the last two years, he has been developing a monitoring system for reflective DDoS statistics that are external to any specific network. During the talk, he demonstrated participant the system’s source code.
Fifteen fast-track talks were held during PHDays VI. The moderators spoke on various topics, including mobile antiviruses and tips on how to bruteforce passwords in one minute. Young School participants were among the speakers: they shared results of their researches on the protection of business systems, applied cryptography, etc.
Five-minutes sessions were organized this year for the first time. Any attendee could share his or her ideas, tell about his or her work and projects, about a new vulnerability, or about a plan to perform a research.
During hands-on labs, PHDays participants analyzed malicious programs, exploited vulnerabilities of EAC systems, hacked web applications, searched for vulnerabilities in SCADA systems, created their own exploits.
Hacking contests were held alongside with the reports and sections. This year, the key contest was PHDays VI СityF. It was based on the standoff between information security experts and hackers. It was a real fight: hackers attacked the city, while expert security centers tried to confront them. The model city consisted of a bank, mobile carrier, a large company’s office, electric power company, etc.
Upon the closing of the first day of the forum, a teenager managed to bypass industrial protocols’ security systems. This caused a shortage at a high-voltage substation (500 kV).
The results of the cyberpunk story contest are already known:
I place — Andrey Frolov,
II place — Dmitry Bogutsky,
III place — Igor Veresnev,
IV place — Vladimir Venglovsky, Alexey Drobyshevsky, Natalya Dukhina, Anna Derbeneva.
***
Sponsors: Kaspersky Lab, Axoft, CROC, Cisco, Informzaschita, Check Point, InfoTeCS, IBS, Qlik, ANGARA, MONT, NAG and ICL.
Media partners: Hacker Magazine, SecurityLab, Rubezh, PRO Business, Anti-Malware.ru, the Analytical Banking Magazine, the National Banking Journal, Digital Substation, Open Security, Computerworld Russia, BIS Journal, PC MAGAZINE Russian Edition, Storage News, ICT Online, Computerra, JSON.TV, AppTractor, BIT (Business and Information Technologies), System Administrator, Bankir.Ru, Popi;ar Mechanics, Bankovskoye Obozrenie, Information Security, Global CIO, iEcp.ru, BIS TV, IKS-Media, PC WEEK/RE, Apps4ALL, Business Journal, PLUS Journal.