The Standoff: Recap and highlights of live cyberbattle at HITB+CyberWeek 2019
2/5/2020
In mid-October, a battle flared for three days in sunny Abu Dhabi between teams of security experts. Attackers (red teams) and defenders (blue teams) fought for control of the digital infrastructure of a mock city specially created by Positive Technologies for HITB+CyberWeek 2019.
A longtime favorite among security professionals, The Standoff is a cyberbattle held annually by Positive Technologies at the Positive Hack Days international forum on practical security. The Abu Dhabi competition marked a big first for The Standoff, which had previously been held only in Moscow, most recently in May at PHDays 9. For details, check our previous article.
Smart city in Abu Dhabi
Positive Technologies created an enormous diorama of Kabakas, a fictional industrial city, spanning about 17 square meters (183 square feet) and containing thousands of figurines. Over 100 meters (328 feet) of miniature railway tracks and more than 500 meters (1,640 feet) of wiring went into creating the city infrastructure. The mock city model allowed demonstrating consequences of real cyberattacks against critical infrastructure.

Figure 1. A diorama-eye view of the city of Kabakas
The city included a refinery, oil loading terminal, and oil storage facility belonging to Federal Oil Company. Heating, air conditioning, and lighting were provided by HiPower. Susani Logistics was responsible for transportation, servicing the railroad, traffic lights, and the Ferris wheel at the amusement park. Each company's infrastructure included approximately 70 hosts. All the facilities were equipped with modern PLCs designed to control industrial processes. The city also had its own bank, the Central Bank of Kabaka.
Gearing up for a matchup
A total of 60 security experts took part. Attackers were represented by seven teams from the Middle East and Eastern Europe. Defenders had three teams, two of them from the UAE and one from Russia.
At PHDays 9, defenders could check systems for vulnerabilities in advance, take appropriate measures, and install protection tools. By contrast, in Abu Dhabi they were not given time to prepare for attacks. Nevertheless, defenders had a number of modern protection tools in their arsenal, including WAF, NGFW, and SIEM.
The Positive Technologies Expert Security Center monitored the game and recorded attacks against infrastructure with the help of Positive Technologies products such as MaxPatrol SIEM, PT Network Attack Discovery, PT Application Firewall, PT MultiScanner, and PT ISIM.
What the "bad guys" tried to do
The battle lasted from October 15 to 17. Attackers pursued many of the same goals as real-world cybercriminals. They could pick from 30 tasks on the game portal, each worth a certain number of points. The winning attacker team was the one with the most points earned.
Tasks were of three main types: withdrawing money from the accounts of Central Bank of Kabaka clients, stealing information from industrial companies, and disrupting companies' operations. Attackers could also sell employees' email addresses, phone numbers, salary information, and corporate documents to earn additional points.
The first day was marked by a pleasant surprise for attackers when they learned that it was possible to install the HITB-DDoSCOIN miner on compromised hosts and earn points by mining. In addition, throughout the game, teams could take part in a bug bounty by reporting vulnerabilities to the organizers for additional points.
Attacker actions and tactics
Here we will take a closer look at key moments in the game and techniques used by attackers. For terminology, we will rely on MITRE ATT&CK, a knowledge base of advanced persistent threat (APT) information. At the end of this article, we provide a heatmap demonstrating the techniques most frequently used by The Standoff teams.
Day 1: Breaching the perimeter
From the early morning of the first day, the attackers quickly got to work against Federal Oil Company, Susani Logistics, and HiPower. They scanned the companies' perimeters hoping to find known vulnerabilities (Exploit Public-Facing Application) and bruteforce passwords (Brute Force). We detected attempts to exploit the BlueKeep vulnerability (CVE-2019-0708), but none were successful.
By noon, one of the teams punched through the perimeter of Susani Logistics by uploading a web shell and subsequently could remotely execute OS commands. At about the same time, another team detected and exploited RCE vulnerability CVE-2018-15708 in Nagios on the perimeter of Federal Oil Company.
Right after obtaining a shell, the teams began reconnaissance. Our monitoring tools constantly picked up the commands typical of reconnaissance: whoami, quser, ls, ifconfig, and ipconfig, to name a few. In MITRE ATT&CK terminology, attackers used System Owner/User Discovery, File and Directory Discovery, and System Network Configuration Discovery. For persistence, one team created a local user account on a compromised host and added it to the sudo group (Create Account). With the help of wget, the attackers uploaded additional modules of their own, laying the groundwork for attacks within the network (Remote File Copy).
On one of the hosts belonging to Federal Oil Company, attackers discovered the Redis DBMS and attempted to remotely execute code on the server using the master–slave replication mechanism, but this attack failed. (Attackers eventually managed to hack the Redis server, but only on the third day.)
In the afternoon, two teams discovered a vulnerable YAML parameter on a HiPower server and got shell access. One of the teams immediately installed a miner on the compromised host (Resource Hijacking).
Day 2: Battle raging on
On the second day, teams worked in two directions: looking for new entry points to corporate networks and moving laterally from hosts already compromised on the first day. To perform reconnaissance on compromised hosts, some attackers installed nmap and scanned the network (Network Service Scanning). One team spent time analyzing an AppArmor configuration file.
Around 1 p.m., one of the teams managed to upload the password-protected WSO web shell to Federal Oil Company's host cloud.fedoil.hitb. Then came a series of privilege escalation attacks. At 3:03 p.m., MaxPatrol SIEM flagged an attempted Kerberoasting attack, after which the attackers made several attempts to dump credentials (Credential Dumping). Subsequently, cloud.fedoil.hitb was used as a stepping-stone to access the internal network of Federal Oil Company.
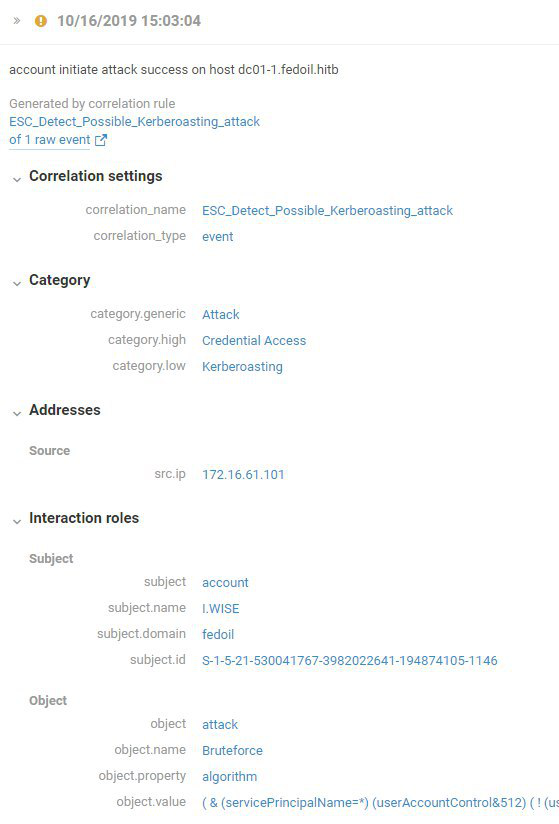
Figure 2. Attempted Kerberoasting attack
After obtaining a local administrator account, the attackers remotely connected to network hosts via RDP (Remote Desktop Protocol), performed reconnaissance, and attempted to perform a memory dump of the lsass process. In this kind of attack, hackers can obtain the passwords (or password hashes) of logged-in system users from the lsass memory dump. This can be useful for developing the attack, especially if one of these users is a privileged user.
To further escalate privileges, the attackers used Incognito tools. With incognito.exe, they could view available privileges, as well as delegation and impersonation tokens. Then they performed a memory dump of the lsass process and ran cmd.exe as administrator.
Wanting to ensure persistence, one team tried to create the domain account "backadmin" on compromised hosts (Create Account). We already observed this technique at The Standoff at PHDays 9. Back then, the hackers had acted in a similar way, and even used the same username (backadmin).
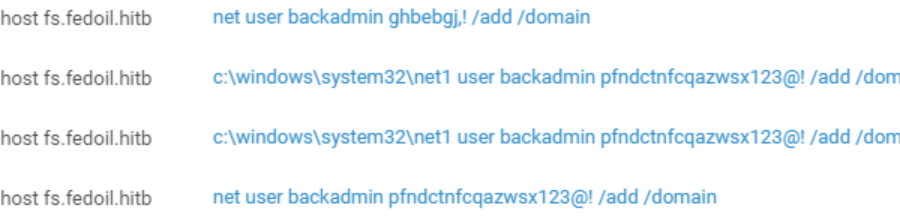
Figure 3. Attempts to create account backadmin using the net user command
On the second day, another team started to install miners on compromised hosts. During the day, the team installed miners on five hosts on the Federal Oil Company network.
team404 "celebrated" the halfway point of the game with a successful bank attack. The team exploited Insecure Direct Object Reference in the online bank. To do this, hackers found a URL that gave access to 50 accounts of the city's residents to an unauthorized user.
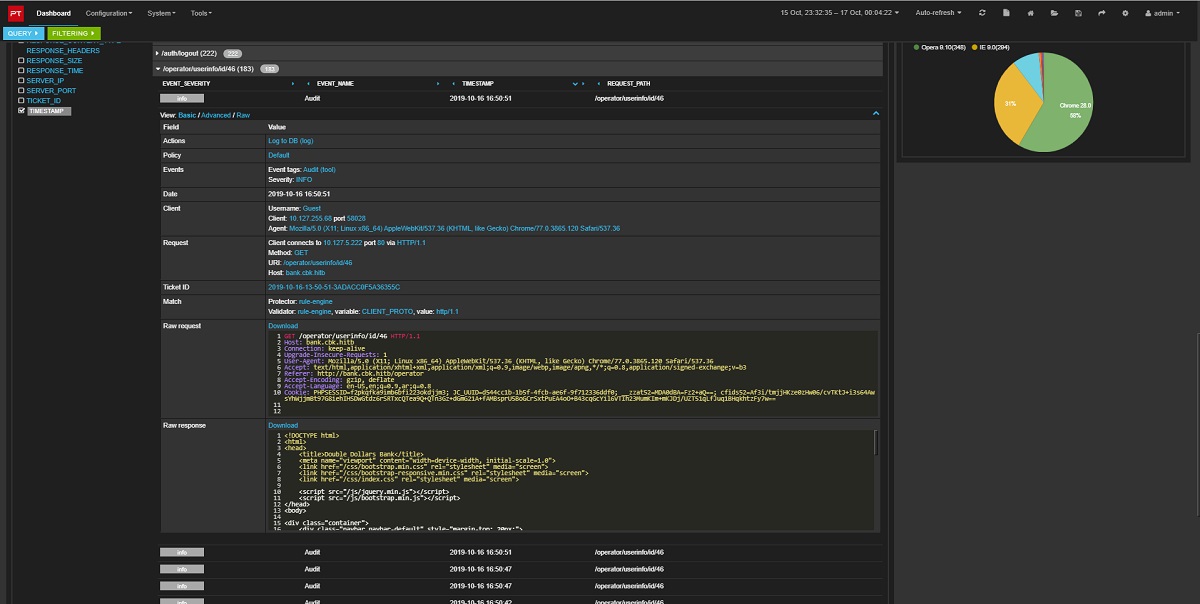
Figure 4. Bank attack recorded by PT Application Firewall
After studying the outgoing transfer limits and transaction time-out, the team wrote a script that transferred money from clients' accounts to the attackers' account using Cart2Cart. This attack brought a lot of points to the team, lifting it into second place overall.
Day 3: "Oops" at the oil storage facility
Around 10 a.m., one team managed to exploit Insecure Deserialization on the Redis server. The attackers injected an object into Pickle and established a reverse shell connection.
At about the same time, another team ran the gost traffic proxying utility on one of the hosts compromised the day before (in a combination of Connection Proxy and Multi-hop Proxy). The team used the utility to pursue attacks inside the Federal Oil Company network. The utility allows tunneling and pivoting to gain access to local resources. In addition, the attackers used Bloodhound and PowerView to get the lay of the land.
Attackers tried to escalate privileges with an NTLM Relay attack (LLMNR/NBT-NS Poisoning and Relay). Their first attempt, using ntlmrelayx.exe, was seemingly unsuccessful. But the hackers pressed on to install a Python interpreter and IMpacket module, then using the utility ntlmrelayx.py to escalate domain user privileges.
Another way to escalate privileges was to launch the command line with the help of PsExec.
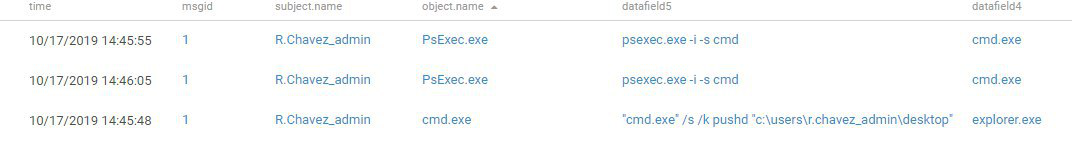
Figure 5. Running cmd.exe via PsExec to escalate privileges
To penetrate some hosts, attackers used Metasploit Framework—in particular, the EternalBlue exploit. After exploiting the vulnerability, the attackers disabled the SMBv1 protocol in order not to let other teams use the same vulnerability. The same technique was used during The Standoff at PHDays 9.
Another way to make life hard for competitors is to replace bruteforced passwords with more complex, harder-to-guess ones. Again, attackers used this technique at PHDays 9 as well.
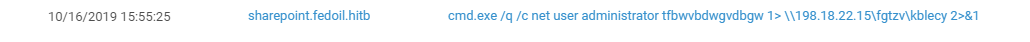
Figure 6. Changing local administrator password via WMI
Industrial companies often have hosts (in most cases, administrator workstations) that are allowed access to network segments containing ICS/SCADA equipment. This was the case at Federal Oil Company. Moving inside the corporate network, attackers found a web application containing numerous vulnerabilities that allowed for remote OS command execution on the host. Next, the attackers created a new user account and connected to the host via RDP. There was no doubt that they had landed in the industrial process segment, as they found the graphical interface of a running Simatic WinCC SCADA system. The attackers easily exited kiosk mode and changed the password of the SCADA account, thus gaining control over the company's industrial equipment processes, which allowed them to perform two tasks. First, the team changed the maximum filling level in the oil storage tank, which caused a tank overflow and oil spill.

Figure 7. Oil storage facility collapse
For the second task, the team almost immediately caused another accident by shutting off the pipeline valve to stop the flow of oil.
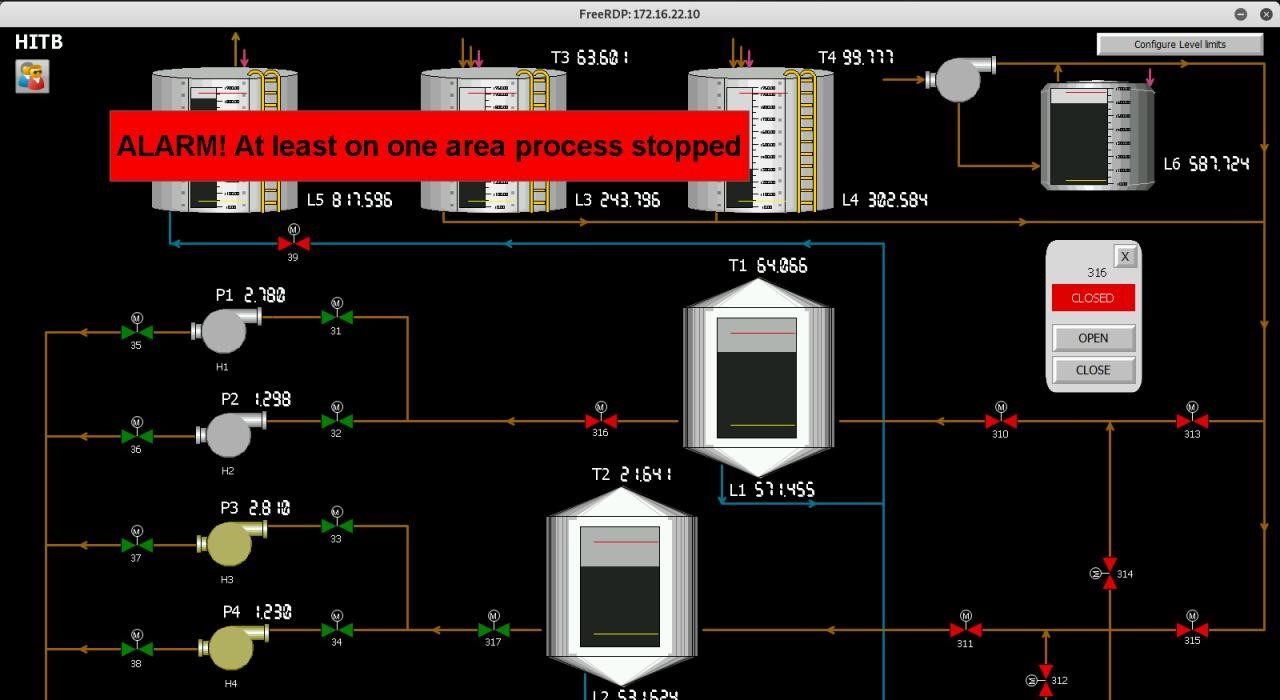
Figure 8. Valve 316 shut off
Team True0xA3 received the highest in-game points at The Standoff for these successful ICS attacks. Only two such attacks happened, both near the end of The Standoff, but that was enough for the team to take the lead and win the contest.
Results
Over the three days, we logged about 50 attacks. In total, attackers managed to hack 20 hosts. Almost half of active actions (44%) happened during the last day of the game.
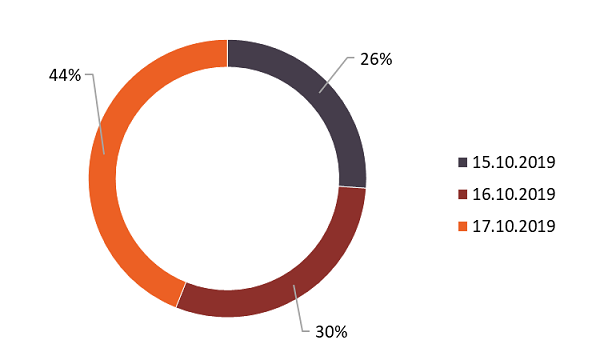
Figure 9. Team activity per day (percentage of recorded incidents)
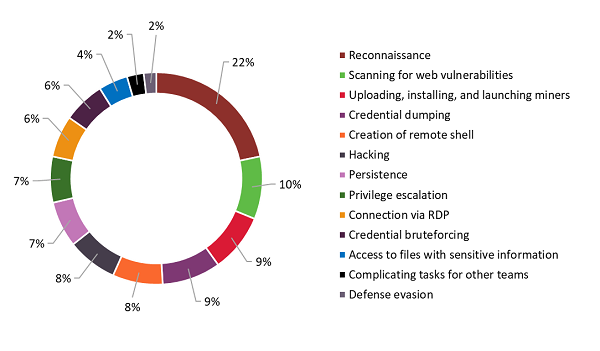
Figure 10. Attackers' actions (percentage of recorded incidents)
Highlights of the three-day battle:
- Attackers managed to steal corporate email addresses and salary information from all companies.
- Two companies (HiPower and Federal Oil Company) lost their corporate documents to attacks. Hackers also stole phone numbers of Federal Oil Company's employees.
- True0xA3, the winner, compromised Federal Oil Company's operations by first shutting off the valve to stop the oil flow and then causing an oil spill at the company's oil terminal.
- team404 was able to withdraw money from client bank accounts.
- Four out of seven teams took part in the bug bounty program, submitting a total of 25 vulnerability reports. These reports accounted for 12 percent of all points earned in the game.
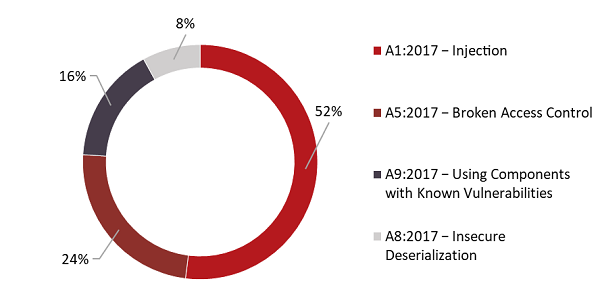
Figure 11. Vulnerabilities discovered as part of the bug bounty program (categorized per OWASP Top 10−2017)
- Of the seven teams, two installed miners, for a total of 9 compromised hosts.
Figure 12. Time of infection by miners
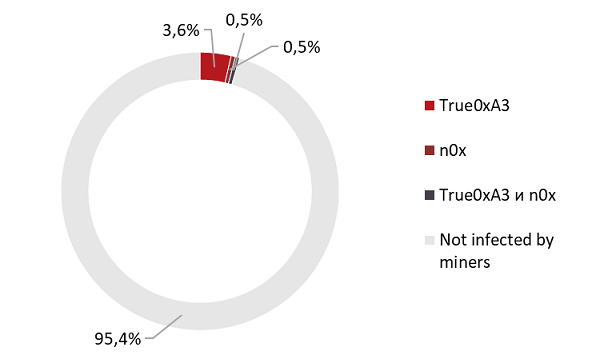
Figure 13. Percentage of hosts infected by miners
The Standoff vs. real-world attacks
Today, many industrial and energy companies recognize that disruption of their operations may be an objective of cybercriminal groups. However, our research shows that information security is often neglected. The problem is especially acute for small cities, such as Kabakas. Even if companies detect security incidents, they often do not take any active measures to respond. As a consequence, all the attacks we observed during the game could very well happen in real life.
In Abu Dhabi, defenders could not prepare for attacks in advance. This allowed us to bring the game conditions even closer to real life. However, from the very beginning of the battle, defenders focused on countering the attackers' moves and were constantly anticipating attacks. In real life, on the contrary, it is impossible to predict when a targeted attack is going to happen. It is much easier to counter an attack when you have an idea of how the criminals are going to act, and which tools, techniques, and tactics they are going to use when they strike.
Most successful attacks at The Standoff started with hackers exploiting vulnerabilities at the perimeter. Some teams learned corporate email addresses from public sources (OSINT) and sent phishing emails. However, most emails did not look trustworthy and only a few teams managed to trick the city's residents into opening malicious attachments. Nine out of ten currently active cybercriminal groups start their attacks against companies by sending phishing emails to employees. These messages come with careful preparation. Security experts cannot forget that when an APT group sends phishing messages, the changes of a victim opening the attachment are much higher than usual.
After attackers penetrate the internal network, their actions are in many ways similar. Once inside the network, both real-world cybercriminals and The Standoff participants try to perform reconnaissance, get a foothold, and escalate privileges. Just like real hackers, attackers at The Standoff mostly used legitimate utilities after penetrating the network. However, unlike real criminals, the contest participants took almost no measures to hide their presence on the network, focusing only 2 percent of their efforts on evading defenses.
Unfortunately (or fortunately), none of the red teams coped with The Standoff's most profitable task: to make two trains collide. We wonder whether attackers could have accomplished this and other tasks, had they not been limited by time and resources? What's for certain is that real criminals will stop at nothing. They are ready to pay good money for unique tools and can wait for months, or even longer, until the right moment for an attack comes.
