The Way of the Industrial Ninja: PLC hacking at PHDays 9
7/22/2019

This year's PHDays 9 included Industrial Ninja—a contest of skill at hacking a gas pumping facility. At the PHDays venue, we created three stands that, at different levels of difficulty (No Security, Low Security, High Security), emulated the same industrial process: pressurized air was pumped to inflate, and then deflate, a balloon.
No matter the security level, the hardware in each of the stands was identical: an S7-300 Siemens Simatic PLC; emergency deflation button and pressure sensor (connected to the PLC's digital inputs); and intake and outlet valves (connected to the PLC's digital outputs). You can see these components in the following picture:

The PLC was programmed to deflate or inflate the balloon by closing or opening valves based on pressure readings. But all the stands included a manual override mode, which allowed controlling valve status without any restrictions.
For competitors, the trick was to find a way to enable this mode. Doing so on the High Security stand, needless to say, was not for the faint-hearted.
During the two-day contest, the contestants found solutions to five of the six tasks. The first-place winner (who had spent a week preparing) garnered 233 points. The top scorers were a1exdandy in first place, Rubikoid in second place, and Ze in third place.
Because nobody was able to conquer all three stands at PHDays, we decided to take the contest online. In early June we published the most difficult task for all to try. We gave competitors a month to complete the task, find the flag, and give an interesting description of the steps they took.
The bulk of the text that follows is courtesy of Alexey Kovrizhnykh (a1exdandy) from the company Digital Security. He took first place in the contest at PHDays and also wrote the best solution of those we received. In places we have added our own comments as well.
Initial analysis
The task came with an archive, which contained several files:
- block_upload_traffic.pcapng
- DB100.bin
- hints.txt
The file hints.txt provides the following information to get started:
- Word has it that it's possible to upload blocks from PlcSim to Step7.
- The PLC in question is a Siemens Simatic S7-300.
PlcSim is a PLC emulator for running and debugging programs written for the Siemens S7.
The file DB100.bin contains the DB100 PLC data block:
00000000: 0100 0102 6e02 0401 0206 0100 0101 0102 ....n........... 00000010: 1002 0501 0202 2002 0501 0206 0100 0102 ...... ......... 00000020: 0102 7702 0401 0206 0100 0103 0102 0a02 ..w............. 00000030: 0501 0202 1602 0501 0206 0100 0104 0102 ................ 00000040: 7502 0401 0206 0100 0105 0102 0a02 0501 u............... 00000050: 0202 1602 0501 0206 0100 0106 0102 3402 ..............4. 00000060: 0401 0206 0100 0107 0102 2602 0501 0202 ..........&..... 00000070: 4c02 0501 0206 0100 0108 0102 3302 0401 L...........3... 00000080: 0206 0100 0109 0102 0a02 0501 0202 1602 ................ 00000090: 0501 0206 0100 010a 0102 3702 0401 0206 ..........7..... 000000a0: 0100 010b 0102 2202 0501 0202 4602 0501 ......".....F... 000000b0: 0206 0100 010c 0102 3302 0401 0206 0100 ........3....... 000000c0: 010d 0102 0a02 0501 0202 1602 0501 0206 ................ 000000d0: 0100 010e 0102 6d02 0401 0206 0100 010f ......m......... 000000e0: 0102 1102 0501 0202 2302 0501 0206 0100 ........#....... 000000f0: 0110 0102 3502 0401 0206 0100 0111 0102 ....5........... 00000100: 1202 0501 0202 2502 0501 0206 0100 0112 ......%......... 00000110: 0102 3302 0401 0206 0100 0113 0102 2602 ..3...........&. 00000120: 0501 0202 4c02 0501 0206 0100 ....L.......
As its name suggests, the file block_upload_traffic.pcapng contains a traffic dump from uploading of blocks to the PLC.
Note that getting this traffic dump on-site at PHDays would have been a bit more difficult. There you needed to delve into a script from the project file for TeslaSCADA2. The script had the information needed to find the dump (encrypted with RC4) and the decryption key for it. To get the block dumps at PHDays, you needed to use a client for the S7 protocol. For this, I used the demo client from the Snap7 package.
Extracting signal processing blocks from traffic dump
The contents of the dump make clear that we have several signal processing blocks, specifically OB1, FC1, FC2, and FC3:
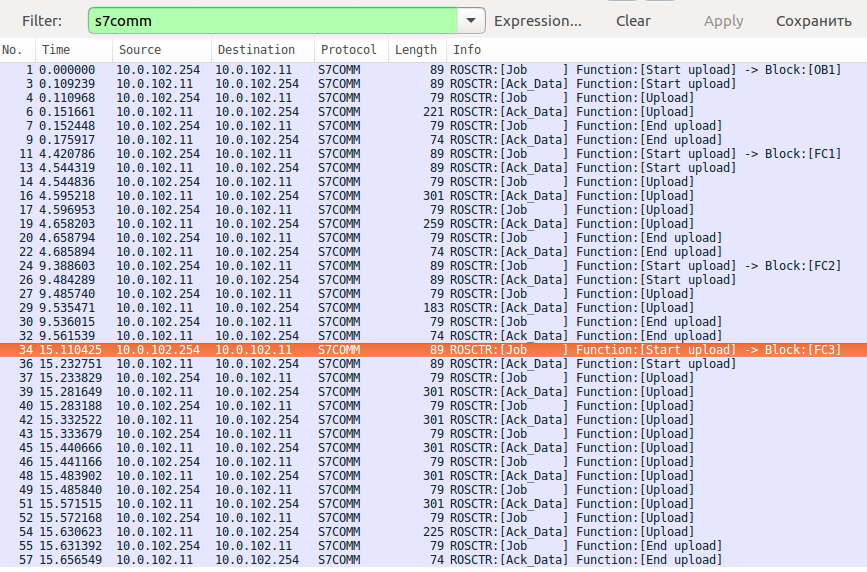
How can we extract these blocks? One way is to convert the traffic from pcapng to pcap and then run the following script:
#!/usr/bin/env python2
import struct from scapy.all import *
packets = rdpcap('block_upload_traffic.pcap') s7_hdr_struct = '>BBHHHHBB' s7_hdr_sz = struct.calcsize(s7_hdr_struct) tpkt_cotp_sz = 7 names = iter(['OB1.bin', 'FC1.bin', 'FC2.bin', 'FC3.bin']) buf = ''
for packet in packets: if packet.getlayer(IP).src == '10.0.102.11': tpkt_cotp_s7 = str(packet.getlayer(TCP).payload) if len(tpkt_cotp_s7) < tpkt_cotp_sz + s7_hdr_sz: continue s7 = tpkt_cotp_s7[tpkt_cotp_sz:] s7_hdr = s7[:s7_hdr_sz] param_sz = struct.unpack(s7_hdr_struct, s7_hdr)[4] s7_param = s7[12:12+param_sz] s7_data = s7[12+param_sz:] if s7_param in ('\x1e\x00', '\x1e\x01'): # upload buf += s7_data[4:] elif s7_param == '\x1f': with open(next(names), 'wb') as f: f.write(buf) buf = ''
This yields a number of blocks, which always start with the bytes 70 70 (pp). Now we need to figure out how to analyze them. The task hint makes one think about using PlcSim for this purpose.
Obtaining human-readable instructions from the blocks
To start, we can try to program S7-PlcSim: first we upload several blocks to it with repeating instructions (= Q 0.0) with the help of the Simatic Manager software. Then we save the emulator-generated PLC to the file example.plc. Looking at the file contents, we easily spot the start of these uploaded blocks based on the 70 70 signature we noticed already. Prior to the blocks, it seems that the block size is written as a 4-byte little-endian value.
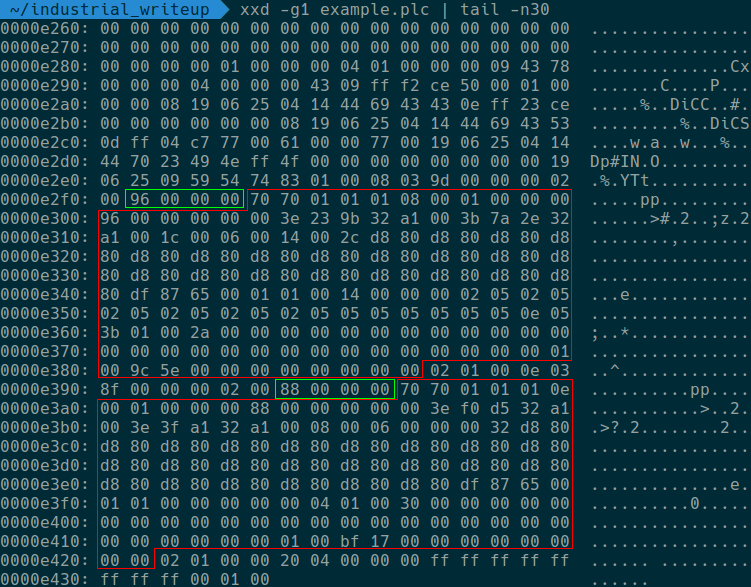
After figuring out the structure of the plc files, here was the plan for reading PLC S7 programs:
- Use Simatic Manager to create a block structure in S7-PlcSim that would be equivalent to the block structure we saw in the dump. Blocks should match in terms of both size (by making sure they contain the right amount of instructions) and identifiers (OB1, FC1, FC2, FC3).
- Save the PLC to a file.
- Swap out the content of the blocks from that file, inserting the blocks from the traffic dump. Find block start based on the signature.
- Upload the modified file to S7-PlcSim and look at the block contents in Simatic Manager.
To swap out the blocks, we can use the following code:
with open('original.plc', 'rb') as f:
plc = f.read()
blocks = []
for fname in ['OB1.bin', 'FC1.bin', 'FC2.bin', 'FC3.bin']:
with open(fname, 'rb') as f:
blocks.append(f.read())
i = plc.find(b'pp')
for block in blocks:
plc = plc[:i] + block + plc[i+len(block):]
i = plc.find(b'pp', i + 1)
with open('target.plc', 'wb') as f:
f.write(plc)
Alexey took a path that was probably more difficult, but nonetheless correct. We had originally anticipated that contestants would choose NetToPlcSim in order to use PlcSim over the network, upload blocks to PlcSim via Snap7, and then download these blocks as a project from PlcSim with the help of the developer tools.
Open the file in S7-PlcSim, so now we can read the overwritten blocks in Simatic Manager. Main functions for device management are located in block FC1. Of special note is the variable #TEMP0: when it is set to true, PLC control switches to manual override mode based on the bit memory values M2.2 and M2.3. The value of #TEMP0 is set by function FC3.
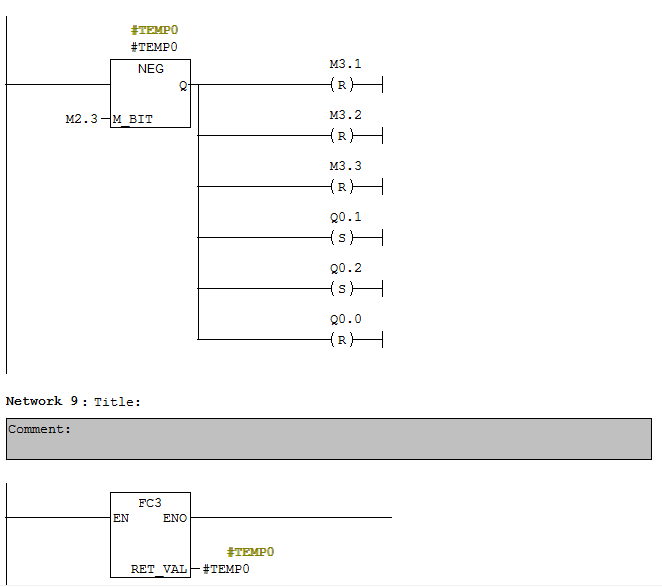
To solve the task, we need to analyze function FC3 and determine what we need to do for the function to return a value of 1.
Signaling processing blocks on the PLC of the Low Security contest stand worked similarly, but were easier to trick. To set the value of #TEMP0, all you had to do was write the string my ninja way to block DB1. Value checking in the block worked in a simple way that did not require a deep understanding of the block programming language. Naturally, the bar was much higher for the High Security stand: getting manual control required getting one's hands dirty with the STL language (one of the ways for S7 PLC programming).
Reverse-engineering block FC3
Here are the contents of block FC3 in STL form:
L B#16#0
T #TEMP13
T #TEMP15
L P#DBX 0.0
T #TEMP4
CLR
= #TEMP14
M015: L #TEMP4
LAR1
OPN DB 100
L DBLG
TAR1
<=D
JC M016
L DW#16#0
T #TEMP0
L #TEMP6
L W#16#0
<>I
JC M00d
L P#DBX 0.0
LAR1
M00d: L B [AR1,P#0.0]
T #TEMP5
L W#16#1
==I
JC M007
L #TEMP5
L W#16#2
==I
JC M008
L #TEMP5
L W#16#3
==I
JC M00f
L #TEMP5
L W#16#4
==I
JC M00e
L #TEMP5
L W#16#5
==I
JC M011
L #TEMP5
L W#16#6
==I
JC M012
JU M010
M007: +AR1 P#1.0
L P#DBX 0.0
LAR2
L B [AR1,P#0.0]
L C#8
*I
+AR2
+AR1 P#1.0
L B [AR1,P#0.0]
JL M003
JU M001
JU M002
JU M004
M003: JU M005
M001: OPN DB 101
L B [AR2,P#0.0]
T #TEMP0
JU M006
M002: OPN DB 101
L B [AR2,P#0.0]
T #TEMP1
JU M006
M004: OPN DB 101
L B [AR2,P#0.0]
T #TEMP2
JU M006
M00f: +AR1 P#1.0
L B [AR1,P#0.0]
L C#8
*I
T #TEMP11
+AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP7
L P#M 100.0
LAR2
L #TEMP7
L C#8
*I
+AR2
TAR2 #TEMP9
TAR1 #TEMP4
OPN DB 101
L P#DBX 0.0
LAR1
L #TEMP11
+AR1
LAR2 #TEMP9
L B [AR2,P#0.0]
T B [AR1,P#0.0]
L #TEMP4
LAR1
JU M006
M008: +AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP3
+AR1 P#1.0
L B [AR1,P#0.0]
JL M009
JU M00b
JU M00a
JU M00c
M009: JU M005
M00b: L #TEMP3
T #TEMP0
JU M006
M00a: L #TEMP3
T #TEMP1
JU M006
M00c: L #TEMP3
T #TEMP2
JU M006
M00e: +AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP7
L P#M 100.0
LAR2
L #TEMP7
L C#8
*I
+AR2
TAR2 #TEMP9
+AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP8
L P#M 100.0
LAR2
L #TEMP8
L C#8
*I
+AR2
TAR2 #TEMP10
TAR1 #TEMP4
LAR1 #TEMP9
LAR2 #TEMP10
L B [AR1,P#0.0]
L B [AR2,P#0.0]
AW
INVI
T #TEMP12
L B [AR1,P#0.0]
L B [AR2,P#0.0]
OW
L #TEMP12
AW
T B [AR1,P#0.0]
L DW#16#0
T #TEMP0
L MB 101
T #TEMP1
L MB 102
T #TEMP2
L #TEMP4
LAR1
JU M006
M011: +AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP7
L P#M 100.0
LAR2
L #TEMP7
L C#8
*I
+AR2
TAR2 #TEMP9
+AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP8
L P#M 100.0
LAR2
L #TEMP8
L C#8
*I
+AR2
TAR2 #TEMP10
TAR1 #TEMP4
LAR1 #TEMP9
LAR2 #TEMP10
L B [AR1,P#0.0]
L B [AR2,P#0.0]
-I
T B [AR1,P#0.0]
L DW#16#0
T #TEMP0
L MB 101
T #TEMP1
L MB 102
T #TEMP2
L #TEMP4
LAR1
JU M006
M012: L #TEMP15
INC 1
T #TEMP15
+AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP7
L P#M 100.0
LAR2
L #TEMP7
L C#8
*I
+AR2
TAR2 #TEMP9
+AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP8
L P#M 100.0
LAR2
L #TEMP8
L C#8
*I
+AR2
TAR2 #TEMP10
TAR1 #TEMP4
LAR1 #TEMP9
LAR2 #TEMP10
L B [AR1,P#0.0]
L B [AR2,P#0.0]
==I
JCN M013
JU M014
M013: L P#DBX 0.0
LAR1
T #TEMP4
L B#16#0
T #TEMP6
JU M006
M014: L #TEMP4
LAR1
L #TEMP13
L L#1
+I
T #TEMP13
JU M006
M006: L #TEMP0
T MB 100
L #TEMP1
T MB 101
L #TEMP2
T MB 102
+AR1 P#1.0
L #TEMP6
+ 1
T #TEMP6
JU M005
M010: L P#DBX 0.0
LAR1
L 0
T #TEMP6
TAR1 #TEMP4
M005: TAR1 #TEMP4
CLR
= #TEMP16
L #TEMP13
L L#20
==I
S #TEMP16
L #TEMP15
==I
A #TEMP16
JC M017
L #TEMP13
L L#20
<I
S #TEMP16
L #TEMP15
==I
A #TEMP16
JC M018
JU M019
M017: SET
= #TEMP14
JU M016
M018: CLR
= #TEMP14
JU M016
M019: CLR
O #TEMP14
= #RET_VAL
JU M015
M016: CLR
O #TEMP14
= #RET_VAL
The code is long and, to a person unfamiliar with STL, perhaps intimidating. Instead of analyzing each and every instruction, we recommend checking out the manufacturer's reference for the STL language: [Statement List (STL) for S7-300 and S7-400 Programming](https://cache.industry.siemens.com/dl/files/814/109751814/att%5F933093/v1/STEP%5F7%5F-%5FStatement%5FList%5Ffor%5FS7-300%5Fand%5FS7-400.pdf). What follows is the same code after some reworking: tags and variables have been renamed, with comments added to describe the flow and certain STL constructs. The block in question implements a virtual machine that runs bytecode in block DB100 (whose contents we know). The virtual machine instructions are 1 byte of opcode and argument bytes, one byte per argument. All the instructions have two arguments each. In the comments, their values are referred to as X and Y, respectively.
# Initialize variables
L B#16#0
T #CHECK_N # Number of checks completed successfully
T #COUNTER_N # Total number of checks
L P#DBX 0.0
T #POINTER # Pointer to current instruction
CLR
= #PRE_RET_VAL
# Main loop for bytecode interpreter
LOOP: L #POINTER
LAR1
OPN DB 100
L DBLG
TAR1
<=D # Check to see if pointer outside program bounds
JC FINISH
L DW#16#0
T #REG0
L #TEMP6
L W#16#0
<>I
JC M00d
L P#DBX 0.0
LAR1
# Switch -- cases for handling various opcodes
M00d: L B [AR1,P#0.0]
T #OPCODE
L W#16#1
==I
JC OPCODE_1
L #OPCODE
L W#16#2
==I
JC OPCODE_2
L #OPCODE
L W#16#3
==I
JC OPCODE_3
L #OPCODE
L W#16#4
==I
JC OPCODE_4
L #OPCODE
L W#16#5
==I
JC OPCODE_5
L #OPCODE
L W#16#6
==I
JC OPCODE_6
JU OPCODE_OTHER
# Handler for opcode01: load value from DB101[X] to register Y
# OP01(X, Y): REG[Y] = DB101[X]
OPCODE_1: +AR1 P#1.0
L P#DBX 0.0
LAR2
L B [AR1,P#0.0] # Load argument X (index DB101)
L C#8
*I
+AR2
+AR1 P#1.0
L B [AR1,P#0.0] # Load argument Y (register index)
JL M003 # Equivalent to switch case based on value Y
JU M001 # for selecting register to write to.
JU M002 # Similar constructs are used in operations
JU M004 # below for similar purposes
M003: JU LOOPEND
M001: OPN DB 101
L B [AR2,P#0.0]
T #REG0 # Write value DB101[X] to REG[0]
JU PRE_LOOPEND
M002: OPN DB 101
L B [AR2,P#0.0]
T #REG1 # Write value DB101[X] to REG[1]
JU PRE_LOOPEND
M004: OPN DB 101
L B [AR2,P#0.0]
T #REG2 # Write value DB101[X] to REG[2]
JU PRE_LOOPEND
# Handler for opcode02: load value X to register Y
# OP02(X, Y): REG[Y] = X
OPCODE_2: +AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP3
+AR1 P#1.0
L B [AR1,P#0.0]
JL M009
JU M00b
JU M00a
JU M00c
M009: JU LOOPEND
M00b: L #TEMP3
T #REG0
JU PRE_LOOPEND
M00a: L #TEMP3
T #REG1
JU PRE_LOOPEND
M00c: L #TEMP3
T #REG2
JU PRE_LOOPEND
# Opcode03 is not used in the program, so we'll skip it
...
# Handler for opcode04: compare registers X and Y
# OP04(X, Y): REG[0] = 0; REG[X] = (REG[X] == REG[Y])
OPCODE_4: +AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP7 # first argument - X
L P#M 100.0
LAR2
L #TEMP7
L C#8
*I
+AR2
TAR2 #TEMP9 # REG[X]
+AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP8
L P#M 100.0
LAR2
L #TEMP8
L C#8
*I
+AR2
TAR2 #TEMP10 # REG[Y]
TAR1 #POINTER
LAR1 #TEMP9 # REG[X]
LAR2 #TEMP10 # REG[Y]
L B [AR1,P#0.0]
L B [AR2,P#0.0]
AW
INVI
T #TEMP12 # ~(REG[Y] & REG[X])
L B [AR1,P#0.0]
L B [AR2,P#0.0]
OW
L #TEMP12
AW # (~(REG[Y] & REG[X])) & (REG[Y] | REG[X]) – equivalent to equality check
T B [AR1,P#0.0]
L DW#16#0
T #REG0
L MB 101
T #REG1
L MB 102
T #REG2
L #POINTER
LAR1
JU PRE_LOOPEND
# Handler for opcode05: subtract register Y from X
# OP05(X, Y): REG[0] = 0; REG[X] = REG[X] - REG[Y]
OPCODE_5: +AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP7
L P#M 100.0
LAR2
L #TEMP7
L C#8
*I
+AR2
TAR2 #TEMP9 # REG[X]
+AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP8
L P#M 100.0
LAR2
L #TEMP8
L C#8
*I
+AR2
TAR2 #TEMP10 # REG[Y]
TAR1 #POINTER
LAR1 #TEMP9
LAR2 #TEMP10
L B [AR1,P#0.0]
L B [AR2,P#0.0]
-I # ACCU1 = ACCU2 - ACCU1, REG[X] - REG[Y]
T B [AR1,P#0.0]
L DW#16#0
T #REG0
L MB 101
T #REG1
L MB 102
T #REG2
L #POINTER
LAR1
JU PRE_LOOPEND
# Handler for opcode06: increment #CHECK_N if registers X and Y are equal
# OP06(X, Y): #CHECK_N += (1 if REG[X] == REG[Y] else 0)
OPCODE_6: L #COUNTER_N
INC 1
T #COUNTER_N
+AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP7 # REG[X]
L P#M 100.0
LAR2
L #TEMP7
L C#8
*I
+AR2
TAR2 #TEMP9 # REG[X]
+AR1 P#1.0
L B [AR1,P#0.0]
T #TEMP8
L P#M 100.0
LAR2
L #TEMP8
L C#8
*I
+AR2
TAR2 #TEMP10 # REG[Y]
TAR1 #POINTER
LAR1 #TEMP9 # REG[Y]
LAR2 #TEMP10 # REG[X]
L B [AR1,P#0.0]
L B [AR2,P#0.0]
==I
JCN M013
JU M014
M013: L P#DBX 0.0
LAR1
T #POINTER
L B#16#0
T #TEMP6
JU PRE_LOOPEND
M014: L #POINTER
LAR1
# Increment value of #CHECK_N
L #CHECK_N
L L#1
+I
T #CHECK_N
JU PRE_LOOPEND
PRE_LOOPEND: L #REG0
T MB 100
L #REG1
T MB 101
L #REG2
T MB 102
+AR1 P#1.0
L #TEMP6
+ 1
T #TEMP6
JU LOOPEND
OPCODE_OTHER: L P#DBX 0.0
LAR1
L 0
T #TEMP6
TAR1 #POINTER
LOOPEND: TAR1 #POINTER
CLR
= #TEMP16
L #CHECK_N
L L#20
==I
S #TEMP16
L #COUNTER_N
==I
A #TEMP16
# All checks passed if #CHECK_N == #COUNTER_N == 20
JC GOOD
L #CHECK_N
L L#20
<I
S #TEMP16
L #COUNTER_N
==I
A #TEMP16
JC FAIL
JU M019
GOOD: SET
= #PRE_RET_VAL
JU FINISH
FAIL: CLR
= #PRE_RET_VAL
JU FINISH
M019: CLR
O #PRE_RET_VAL
= #RET_VAL
JU LOOP
FINISH: CLR
O #PRE_RET_VAL
= #RET_VAL
Armed with this information about the virtual machine instructions, we can write a small disassembler to parse the bytecode in block DB100:
import string alph = string.ascii_letters + string.digits
with open('DB100.bin', 'rb') as f: m = f.read()
pc = 0
while pc < len(m): op = m[pc] if op == 1: print('R{} = DB101[{}]'.format(m[pc + 2], m[pc + 1])) pc += 3 elif op == 2: c = chr(m[pc + 1]) c = c if c in alph else '?' print('R{} = {:02x} ({})'.format(m[pc + 2], m[pc + 1], c)) pc += 3 elif op == 4: print('R0 = 0; R{} = (R{} == R{})'.format( m[pc + 1], m[pc + 1], m[pc + 2])) pc += 3 elif op == 5: print('R0 = 0; R{} = R{} - R{}'.format( m[pc + 1], m[pc + 1], m[pc + 2])) pc += 3 elif op == 6: print('CHECK (R{} == R{})\n'.format( m[pc + 1], m[pc + 2])) pc += 3 else: print('unk opcode {}'.format(op)) break
And now we get the following virtual machine code:
R1 = DB101[0]
R2 = 6e (n)
R0 = 0; R1 = (R1 == R2)
CHECK (R1 == R0)
R1 = DB101[1]
R2 = 10 (?)
R0 = 0; R1 = R1 - R2
R2 = 20 (?)
R0 = 0; R1 = R1 - R2
CHECK (R1 == R0)
R1 = DB101[2]
R2 = 77 (w)
R0 = 0; R1 = (R1 == R2)
CHECK (R1 == R0)
R1 = DB101[3]
R2 = 0a (?)
R0 = 0; R1 = R1 - R2
R2 = 16 (?)
R0 = 0; R1 = R1 - R2
CHECK (R1 == R0)
R1 = DB101[4]
R2 = 75 (u)
R0 = 0; R1 = (R1 == R2)
CHECK (R1 == R0)
R1 = DB101[5]
R2 = 0a (?)
R0 = 0; R1 = R1 - R2
R2 = 16 (?)
R0 = 0; R1 = R1 - R2
CHECK (R1 == R0)
R1 = DB101[6]
R2 = 34 (4)
R0 = 0; R1 = (R1 == R2)
CHECK (R1 == R0)
R1 = DB101[7]
R2 = 26 (?)
R0 = 0; R1 = R1 - R2
R2 = 4c (L)
R0 = 0; R1 = R1 - R2
CHECK (R1 == R0)
R1 = DB101[8]
R2 = 33 (3)
R0 = 0; R1 = (R1 == R2)
CHECK (R1 == R0)
R1 = DB101[9]
R2 = 0a (?)
R0 = 0; R1 = R1 - R2
R2 = 16 (?)
R0 = 0; R1 = R1 - R2
CHECK (R1 == R0)
R1 = DB101[10]
R2 = 37 (7)
R0 = 0; R1 = (R1 == R2)
CHECK (R1 == R0)
R1 = DB101[11]
R2 = 22 (?)
R0 = 0; R1 = R1 - R2
R2 = 46 (F)
R0 = 0; R1 = R1 - R2
CHECK (R1 == R0)
R1 = DB101[12]
R2 = 33 (3)
R0 = 0; R1 = (R1 == R2)
CHECK (R1 == R0)
R1 = DB101[13]
R2 = 0a (?)
R0 = 0; R1 = R1 - R2
R2 = 16 (?)
R0 = 0; R1 = R1 - R2
CHECK (R1 == R0)
R1 = DB101[14]
R2 = 6d (m)
R0 = 0; R1 = (R1 == R2)
CHECK (R1 == R0)
R1 = DB101[15]
R2 = 11 (?)
R0 = 0; R1 = R1 - R2
R2 = 23 (?)
R0 = 0; R1 = R1 - R2
CHECK (R1 == R0)
R1 = DB101[16]
R2 = 35 (5)
R0 = 0; R1 = (R1 == R2)
CHECK (R1 == R0)
R1 = DB101[17]
R2 = 12 (?)
R0 = 0; R1 = R1 - R2
R2 = 25 (?)
R0 = 0; R1 = R1 - R2
CHECK (R1 == R0)
R1 = DB101[18]
R2 = 33 (3)
R0 = 0; R1 = (R1 == R2)
CHECK (R1 == R0)
R1 = DB101[19]
R2 = 26 (?)
R0 = 0; R1 = R1 - R2
R2 = 4c (L)
R0 = 0; R1 = R1 - R2
CHECK (R1 == R0)
As you can see, this program simply checks each character from DB101 for equality with a certain value. The string to pass all the checks was as follows: n0w u 4r3 7h3 m4573r. Placing this string in block DB101 would activate manual PLC control, allowing the contestant to inflate or deflate the balloon at will.
So there you have it! Alexey displayed an exemplary level of knowledge worthy of an Industrial Ninja. Fun prizes are on the way to their winner. Thank you to everyone who participated!