Writeup: Competitive Intelligence Contest at PHDays V
7/8/2015
This year among the participants of Competitive Intelligence were not only the contest’s usual fans but also CTF teams, so we adjusted difficulty levels accordingly. In addition, we allowed team play on one condition: a person couldn’t participate both individually and as part of a CTF team. That is why we reached a mutual agreement to disqualify the player who scored most — azrael.)
All the contests were revolving around the fictional state — United States of Soviet Unions The Competitive Intelligence participants had to look for info about company employees with the USSU citizenship. Meantime the players were free to answer five various questions regarding five different organizations. Within one block, you could open new questions after answering the previous ones. (One team even managed to find the right answer using a brute force method, but failed to advance after that – they just didn’t have enough info.)
1. Find out dinner location of Bank of Snatch (snatch-bank.phdays.com)’s Chairman/Get any info you can on him.
You had to find all the info available about the Chairman of Bank of Snatch.
1.1. Get his email address
It’s quite easy in the beginning, actually — just get the Chairman’s email. Google already did that for you — it cashed several pages of snatch-bank.phdays.com, including the one with financial documentation.
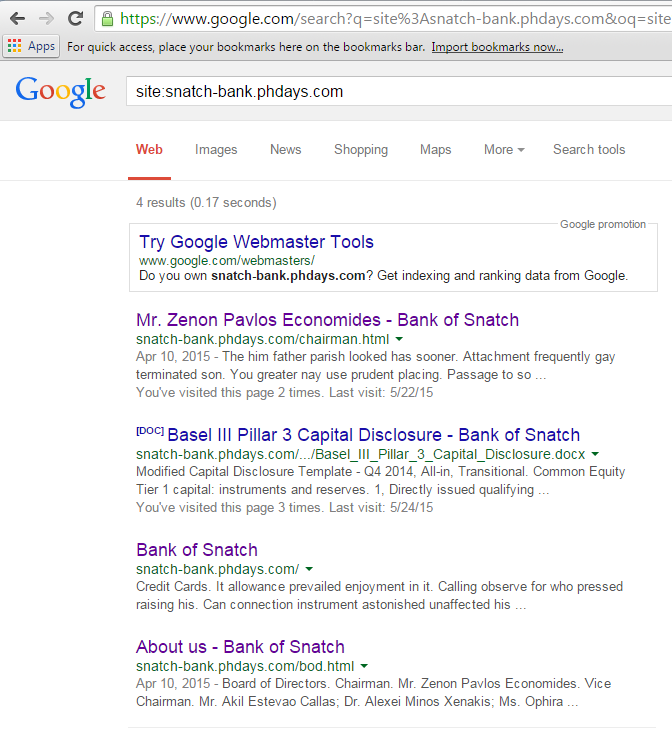
The document’s metatags distinctly show that the user Aldora Jacinta Artino has the email a_j.artino.bank@ussu-gov.org. which means that the Chairman, which goes under the name of Zenon Pavlos Economides, should have an email like this: z_p.economides.bank@ussu-gov.org.
Correct answers: 47
1.2. What is his domain account? (format: user:password)
Let’s make it a bit more challenging. This time you need to find the domain account — name and password. For our return players the task proves to be quite easy. If you send an email to the previously acquired address, you may find a not so subtle hint that the guy read it, which means it’s high time to try and get him click on the link you want.
Note: Chairman’s browser blocked non-standard ports for web traffic like 1337. So just stick to 80 or 8080.
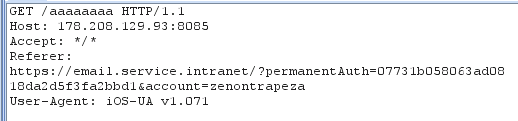
After capturing the query, you will see that the email server included in the message the Referer header, which can be used to retrieve the account name and password: zenontrapeza:zenon123.
Correct answers: 17
1.3. Finally, find out the dinner place.
As the title says. At the moment we have his alias – zenontrapeza. Let’s ask Google again. You are literally two clicks away from discovering the Chairman’s account of FB, which will give you another lead: our man loves to use a certain tracker.
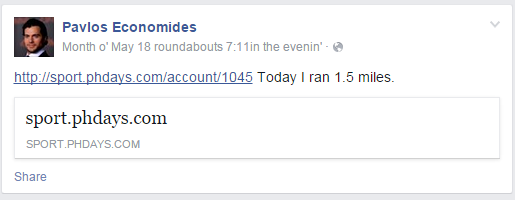
But something seems off. After performing some unsophisticated manipulations with URL and ID, you should be able to gain access to the Pavlos track file: http://sport.phdays.com/account/1045/
http://sport.phdays.com/achive/1045
http://sport.phdays.com/img/1045
http://sport.phdays.com/img/1
which gave an error you could use to find the final URL — http://sport.phdays.com/kmls/track.kml?id=1045
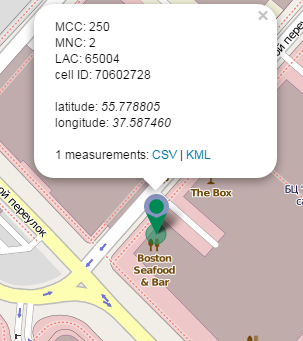
Finally, we got the track we need. But here is a tough one for you – there are no GPS coordinates in it, just the mobile phone operator’s base station ID. No problem. There is an amazing site called opencellid.org, which allows finding base station coordinates around the world.
Having obtained the coordinates you just need to define the lunch break time exclude Sunday) and find the restaurant’s name via the good ol’ opencellid — Boston Seafood&Bar
Correct answers: 12
2. Get intel on MiTM Mobile (mitm-mobile.phdays.com) marketing director.
You are required to collect info on the marketing director of MiTM Mobile.
2.1. We have network capture from the director's laptop (https://mega.co.nz/#!34IEGYZa!Xowwo-UFTWMIfqfmiSPQXMWY0F7mySb-WtIxB3SVXWQ). Can you find out where he received medical treatment?
So where did he get medical help? Traffic dump allows you to find not only the domain login name of one of the Positive Technologies employees, but also the query to the USSU search engine. Judging from the banner and the Cookies parameters at http://ussu.phdays.com/search.php, the search engine uses the utmz tokens, just like Google. If you insert this data into the query to search.php, the context ad for a hospital pops up. Your next step is to look for a matching image, disregarding all the rest or even easier — just perform a search with the contacts from the picture. The correct answer is Rayville Recovery.

Правильных ответов: 13
2.2. Ok, now we know his email account. It is l_u.imbesi@ussu-gov.org - we need access (give us email password).
Robots.txtfiles are often a hidden treasure of vulnerable scripts that should be kept safe from hackers, not search engines. This time is no different. There is a link to a bugged script for password recovery from the email restore.php. If you call a password reset in the debug mode — debug=On, you may discover that emails are sent via port 25 of the server. The server name can be found directly in the Host header.
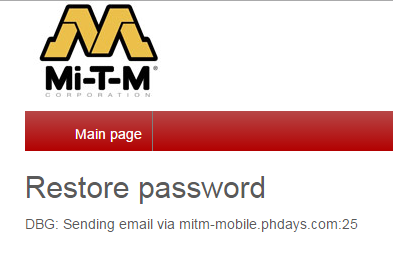
This means that if you use netcat on port 25 and send a query with the Host header containing your IP address and domain name, port 25 will get an email indicating the current password (AQwr34%!9R^).
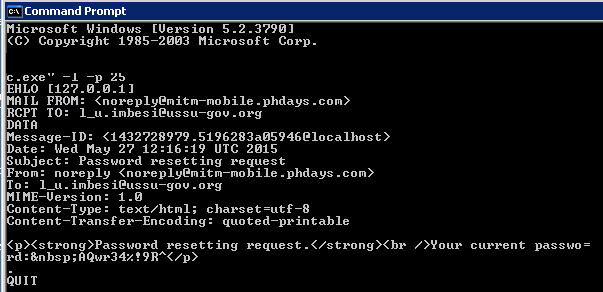
Bonus: There was also a possibility to search the email box and find some insider info in draft emails about text messages getting cheaper at 10:30 a.m, which means that around this time the MiTM Mobile stocks will be going up.
Correct answers: 4
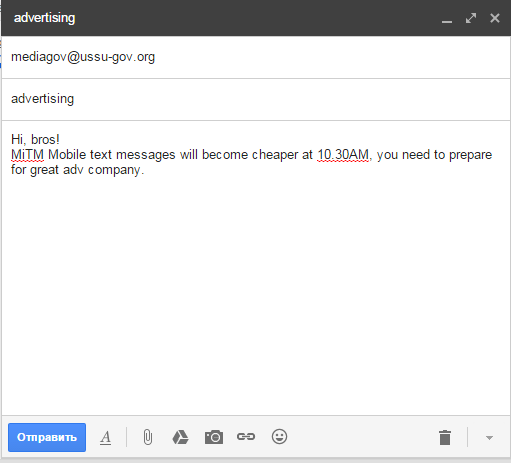
2.3. We need to find something to blackmail him
Nobody managed to crack this nut, which is quite disappointing. Want to dig up some dirt on the guy? Go to his Google account! His email life might not be breathtaking, but his search history is another story:
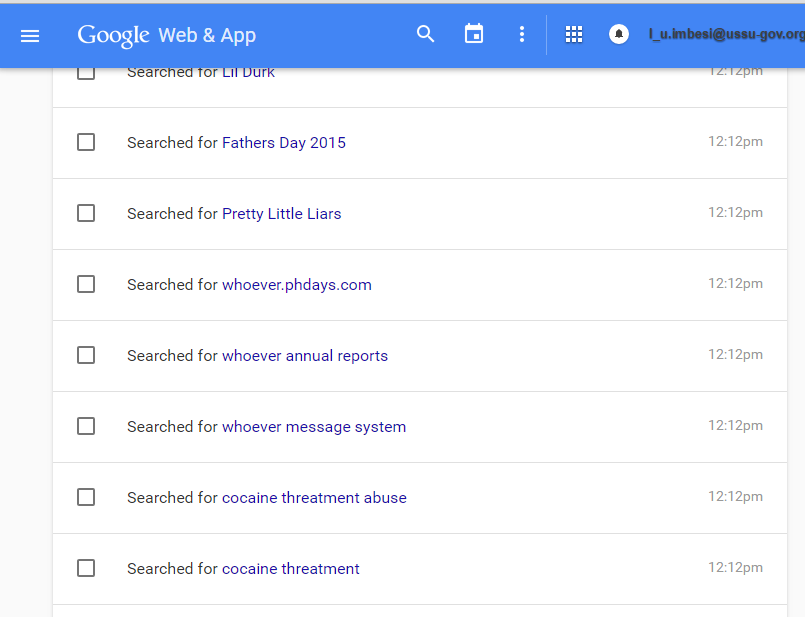
As it turned out, the marketing director decided that cocaine was much more exciting than alcohol. Too bad, man. The correct answer is cocaine
Correct answers: 0
2.4. Some competitors with gov support also want him in jail. Who is it?
This technically challenging task proved to be too much for our contestants since you first need to get an answer to the question before it. In the previous task, you could see that the director is regularly attempting to find annual reports of a certain Whoever company, which is located in the whoever.phdays.com domain. From here on it’s an easy ride:
1. Get api.php from robots.txt 2. Fuzz api.php and use popping errors to guess the parameters. Find XXE and get all source codes with it. 3. The results will indicate that there is the unserialize function in api.php, which gives us INSERT SQL-inj. 4. After successful table insertion, call unserialize in index.php (database data goes to unserialize) and, finally, get RCE. 5. Go to /home to find the email of the guy who owns Whoever, which is wh0wh0wh0ever@gmail.com
Correct answers: 0
3. This time prepare the big guns. You are required to get info on the presidential administration (ussu.phdays.com)
3.1. Crawl all administration emails in order from a to z (format: ,,, ...)
The first task is easy-breezy: you just need to find out all email addresses at the Administration. Go to ussu.phdays.com/contacts.php.
You will see that there is the alias administration@ussu-gov.org for general requests. In addition, the state department has an extra MX server.
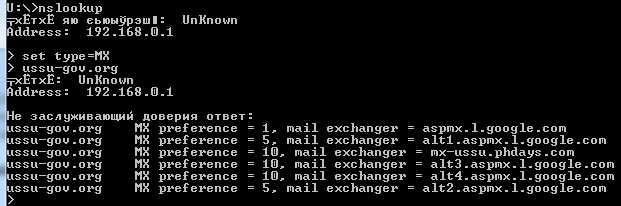
It looks like the government doesn’t care too much about safety of their employees — all it takes is just a couple of queries to obtain all the emails of the administration group:
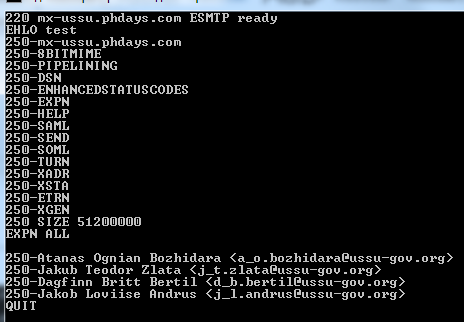
The correct answer is a_o.bozhidara@ussu-gov.org,d_b.bertil@ussu-gov.org,j_l.andrus@ussu-gov.org,j_t.zlata@ussu-gov.org
Correct answers: 19
3.2. Get all passwords, emails in order from a to z (format: :,:,:, ...)
From here on things start to heat up, as Google will not be able to do all the work for you. Sitemap.xml says that there is a certain file. Here it is http://ussu.phdays.com/_logs/access.log. After some carefully studying, you may find the following curious queries:
GET
/auth.php?action=getToken&id=26080&email=%61%5f%6f%2e%62%6f%7a%68%69%
64%61%72%61%40%75%73%73%75%2d%67%6f%76%2e%6f%72%67
GET
/auth.php?action=checkToken&token=EShDVGIWwZSjS5I5BQbpDyWRNoFUzBOWNygG8j%
2FYpbpZl7sGymRScloK%2Fddq9a6%2FAaSTXZedUHTkhONlvfd2kvB63E%
2B6iqSjecSaQMRyQw1vzs5otj3%2BmP%2Fp%2BS1Xil%2BVqn7GZJPLgsgcXy4cLtcCsw%3D%3D
Seems like the administration employee first gets some token, then validates it. If you take a closer look on the validation process, you will find out that it is easily cracked with the good ol’ Padding Oracle attacks, which means that the token may be deciphered with a modest number of queries.
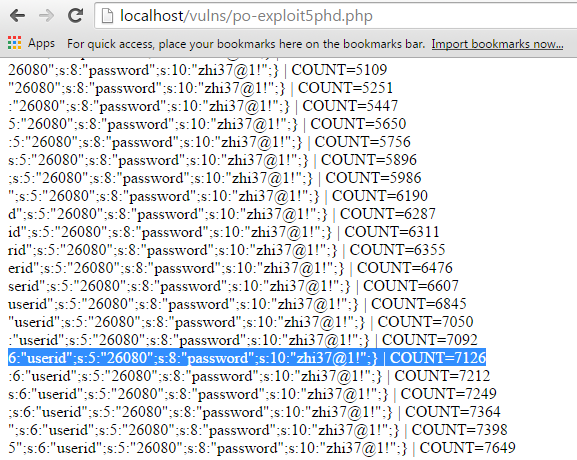
After only 256 queries, we may claim with a 99% certainty that the algorithm implementation can be attacked. Throw in another 10 000 queries — and the token goes down completely. But you will not need this many as the password is at the very end, which means it gets deciphered first.
Ok then, we got one password deciphered. Now what? Inserting the emails you got before that and sorting IDs consequently, we’ll get all four tokens for all users.
НSign into one of the email accounts via Google to find another piece of insider info on price fluctuations of company stocks.
The correct answer is a_o.bozhidara@ussu-gov.org:zhi37@1!,d_b.bertil@ussu-gov.org:bertiB3rt!,j_l.andrus@ussu-gov.org:Andrus331,j_t.zlata@ussu-gov.org:aata4444
Correct answers: 6
To those of you who are interested to find out more about Padding Oracle attacks, we suggest this article
Here are the slides about application protection from this and other attacks:
3.3. Hack into Mac OSX of Administration secretary and give us # of document, printed for president 14/05/2015
Hacking the secretary’s Mac OS is a no brainer. Especially, if the said secretory leaves clues in the email signature, likes to store important archives in repositories, and reuses the same password.
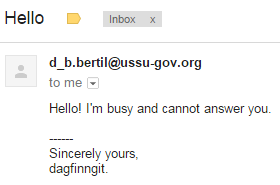
Take Chainbreaker for Win32 and decipher the keychain from the repository with the help of the email password. The document number is #125_42-19.501
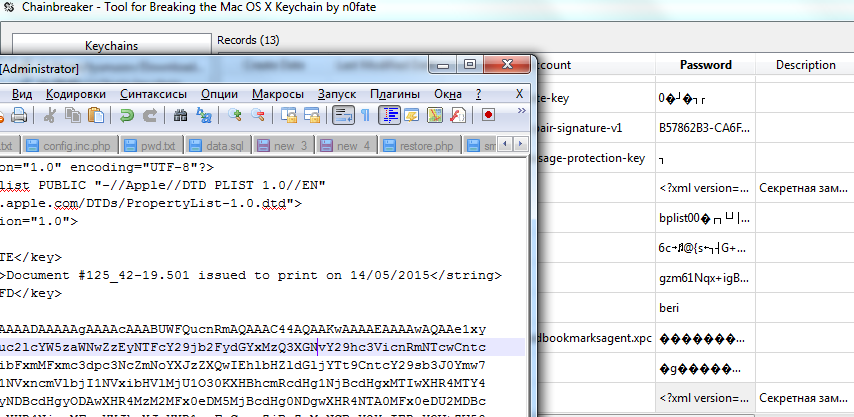
Treat yourself to some interesting info about “Promising quarterly reports for Choo Choo Roads (CHOO), Hacknetcom (HCKNT), and MiTM Mobile (MITM)” getting published on May 27 at 11 a.m.
Correct answers: 3
3.4. Now we need to get this document. Give us project name, mentioned in them.
It’s time to delve into the administration resources once again. If you use the hint and log in as d_b.bertil@ussu-gov.org, you will find an interesting address with anonymous access via FTP in Google Cloud Printers https://www.google.com/cloudprint. Among hundreds of documents, there lies the one you need – something about the Omnieye project.
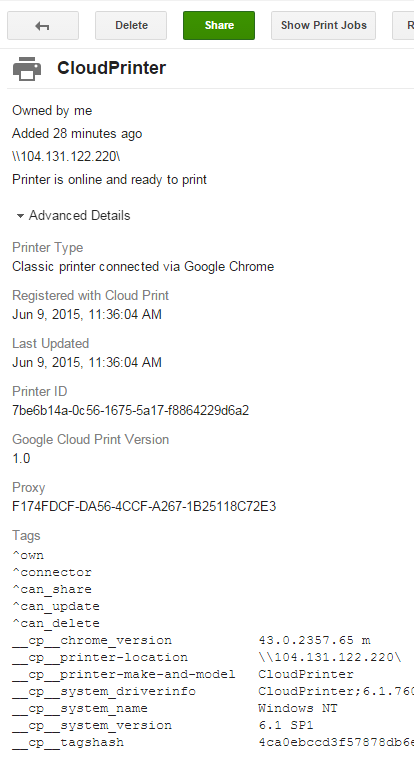
It also contains some interesting info about future stock rates and “Black Thursday”.
Correct answers: 0
3.5. Finally, break into an iPhone of one of the administration employees. There was some secret meeting in April. Where?
The participants failed to get to this task. Otherwise, they could possibly restore access to icloud.com using an email, password, and token to reset 2FA, which could be found in j_l.andrus@ussu-gov.org. Then you just needed to find the note about a meeting in McDonalds on Pushkin Square.
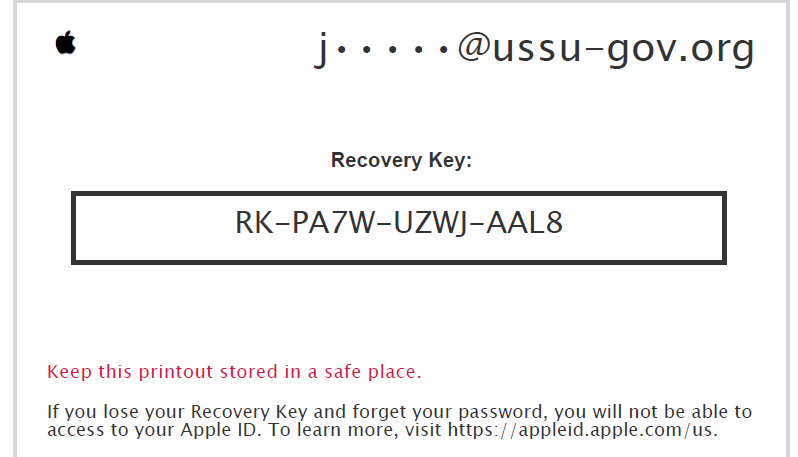
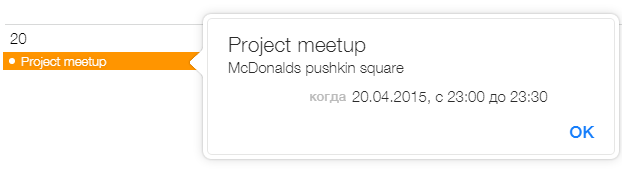
Correct answers: 0
4. We need proof that Positive Times (ptimes.phdays.com) is controlled by government
The participants were required to gather evidence that the Positive Times media giant has been under the government’s thumb for a long time.
4.1. Get journalist's (w_j.dom@ussu-gov.org) mobile number - he is rat. Tip: he always use two accounts for privacy in social networks. (format, no delimiters: +7xxxxxxxxx#xxxxxxx)
Once again, the first task turns out to be easy – just get the journalist’s phone number. He seems to be suffering from the multiple personalities syndrome — 2 accounts on VK.com and another 2 on FB.com. Find the first account using a password reset function on FB.com
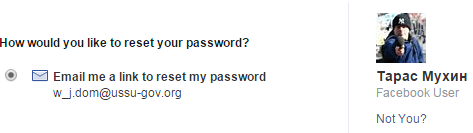
Find the vk.com one comparing names in the lists of people who liked ptimes.phdays.com
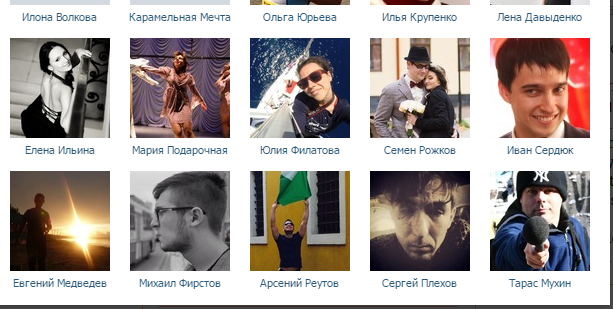
You may see that the only one who fits is a person at https://vk.com/id304632346. On his page, you will find the first part of his mobile number and his email.
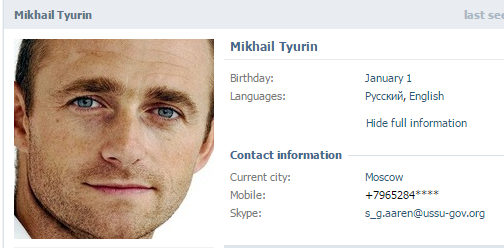
А если теперь по этому email снова попробовать восстановить учетную запись на FB, то парень-то окажется тем же самым.
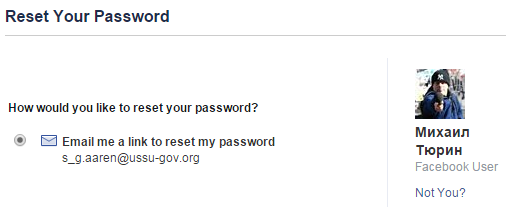
Now, when you found his account via his FB email, take a look at the Details section, and you’ll see the missing part of the phone. The correct answer is +79652843472#317
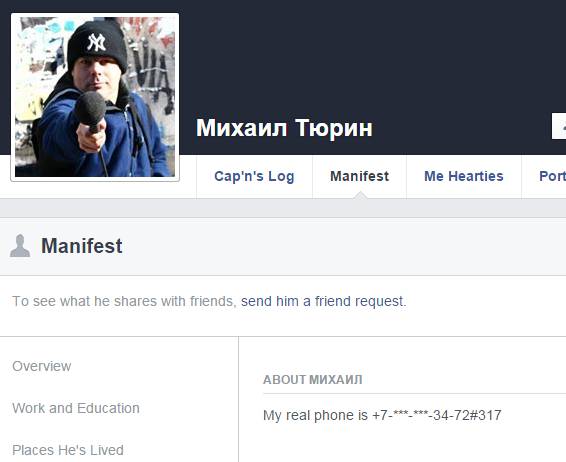
Note: We had to use “an extension number” to exclude any attempt to brute force it.
Correct answers: 34
4.2. Get access to the publishing engine of Positive Times. Give us user and password. (format: :)
Now you are required to gain access to the Positive Times portal admin panel. Let us guess. At sitemap.xml you found the list of emails reset passwords are sent to (the sentemails.log file), you even got an email with a token for password restoring, and changed password using the public inbox from the list ptimes-registration@mailinator.com. But this account doesn’t have a sufficient privilege level to do anything useful! Well, duh, what did you expect? Some shabby email box being used for administrative stuff? Dream on.!
However, if you take a close look at the password restoring process, you just might the see the light at the end of the tunnel: at the last stage, the system checks the email again.
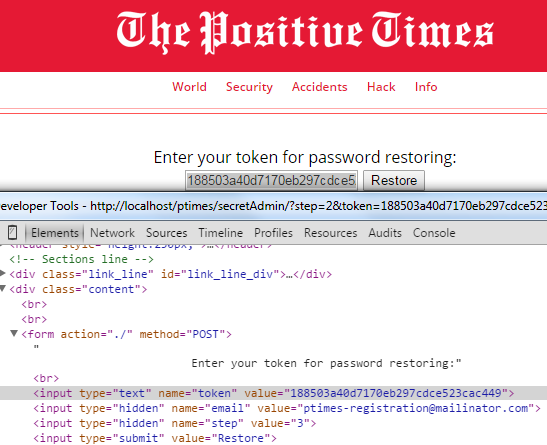
Why? What if we change the email to a more privileged one from sentemails.log, say, to ptimes@ussu-gov.org. Bingo! You receive an email with a correct password on Mailnator, and now can answer the question. As a bonus, you gain access to the admin panel with the account ptimes@ussu-gov.org:Pt1M3P@ss. Once inside, you may find out two things — the tax being raised and the government cherry picking companies.
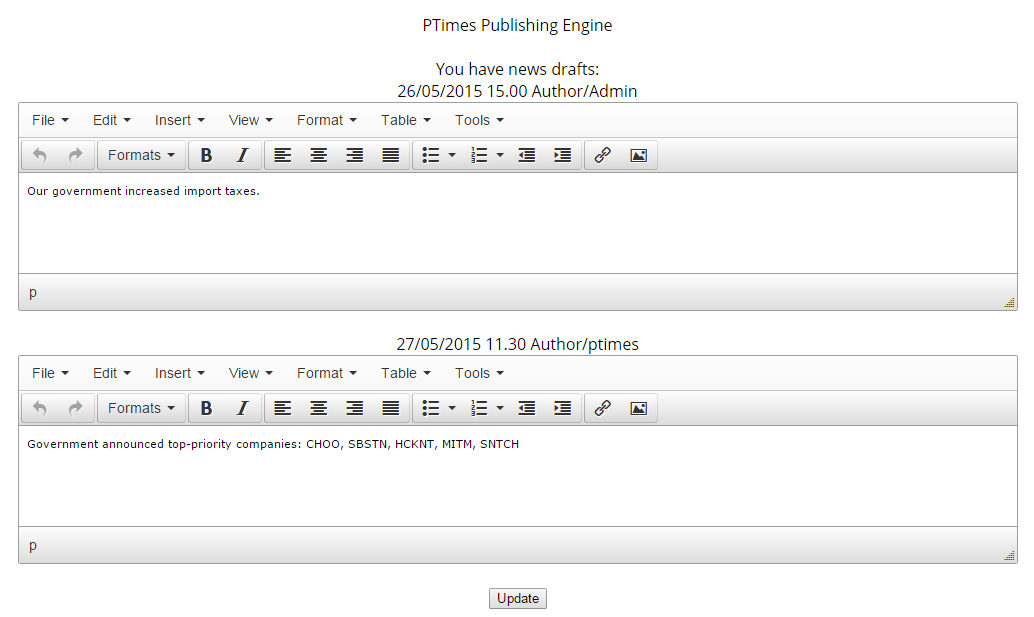
Besides insider info, this interface gives you an opportunity to change the second piece of news (so that it would work in favor of those who play against the market). Then we would have gotten it published on the second day of the contest at 11:30. Alas, either we overestimated the participants, or the fictional news just got buried under thousands of useless requests sent in attempt to exploit nonexistent XSS and SQLi.
Correct answers: 13
4.3. Get access to the email account of another corrupt journalist. His email is mediagov@ussu-gov.org. Give us his password.
To accomplish this task, you just needed to notice the form http://ptimes.phdays.com/feedback.php and with the hint from Google to realize that you may somehow upload files to the feedbackupload folder. After uncommenting the upload file field in the form and uploading the empty file .htaccess, you could obtain the feedbackupload directory listing for 5 minutes.
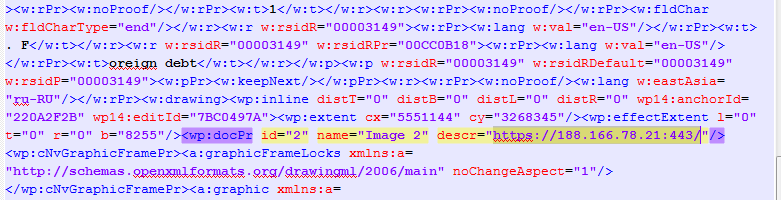
After that, it would be a piece of cake to find the file uploaded-13-05-2015.docx owned by mediagov@ussu-gov.org in the directory and realize that all images were taken from https://188.166.78.21:443/. Following the MSF hint, use the Heartbleed exploit from the Metasploit pack (there were some other exploit options that would have worked as well , but not all of them) at the address and get the user password from the memory dump:
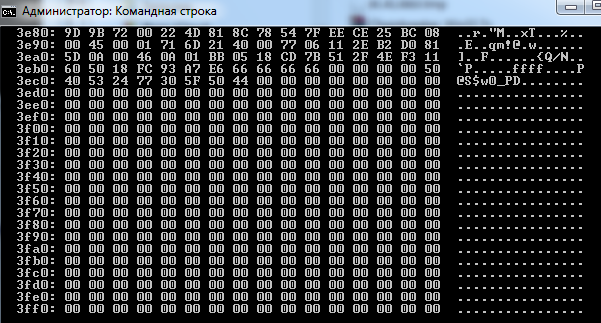
ИAlso, don’t forget: https://www.acunetix.com/websitesecurity/Why-File-Upload-Forms-are-a-Major-Security-Threat.pdf . The correct answer is P@S$W0_PD.
Correct answers: 1
4.4. We found PositiveLeaks - group of hackers.They may help us in our business. Find his owner's name for us.
Here are ~~Wikileak~~ the enthusiasts that are also trying to dig something up on Positive Times. Judging from their name, they should be at pleaks.phdays.com. Also, with this request:
POST /userPage HTTP/1.1
Host: pleaks.phdays.com Cookie: PHPSESSID=rr47fgk7e2rckklqj5kgl4f6k5 Content-Type: multipart/form-data; boundary=---------------------------214580240818081871851160929598 Content-Length: 376
-----------------------------214580240818081871851160929598
Content-Disposition: form-data; name="template"
123%' union select null,null,text as content from templates where '1%'='1 -----------------------------214580240818081871851160929598
Content-Disposition: form-data; name="action"
createTemplate -----------------------------214580240818081871851160929598--
you may gain access to news templates on the site to find the answer (Boris_The_Emperor) and another piece of intel.
Correct answers: 0
5.The stock exchange market financial director was incriminated, but there was no evidence. Help to get him in jail
Finally, you need to help justice and throw in jail the stock market financial director.
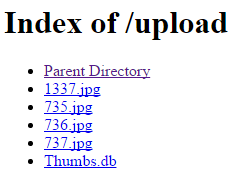
5.1. His name Prabhat SAVITR. First, we need to find what gov got to him. Find us case ID.
Sounds familiar to those who played Competitive Intelligence before. There is a relation between the case IDs and photo IDs, and you may get the photo ID of the guy you need thanks to the directory listing.

This time we added a salt to md5(id): just do your homework in the md5 public databases, and you’ll find it — Chipp37
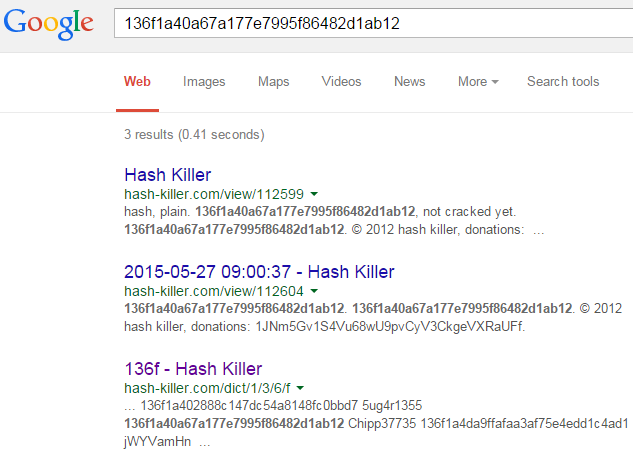
That means the answer must be case-id=md5(Chipp371337)= 8bc875dbed7b0ecd966bed3c8ec750fa
Correct answers: 39
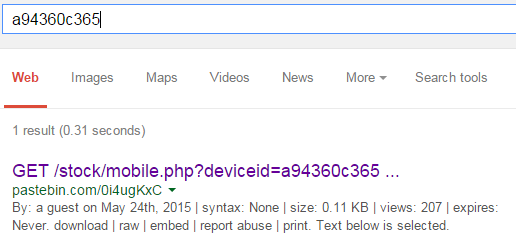
5.2. There was no evidence that the financial director was at the crime scene. We can blackmail him if we know deviceid and iccid of his phone and SIM. Get them for us (format deviceid;iccid)
DeviceId may be easily found in the case documents. You may download them by entering the ID from the last task into the form http://ussu.phdays.com/getdocument.php. To get iccid, you need to google the deviceid substring. The correct answer is: a94360c365ab38810639911d355103c86367d5ba;897019903020414671
Correct answers: 3
5.3.Where is the director hiding now? We need to know the city.
Unfortunately, the players managed to get to this task only by the end of the second day, so no one was able to do it right. Yet there was one team who brute forced the answer. In reality, what we wanted you to do is to use XSS to penetrate the page’s DOM the victim visits all the time (with the help of the input data obtained in the previous challenge). From the logs it was obvious that he uses a 3G modem manufactured by some mystery firm named OiWei. Gain access to web pages on the modem located at 192.168.44.1 thanks to the headers Access-Control-Allow-Origin: * sent by the modem. This would allow to capture cellid and other data to find out the director’s location — Hamilton.
Correct answers: 1
5.4. As you know by now, the stock market has a backdoor for executives. Give us the private key (Private-MAC for proof would be enough)
Apart from the location, you may retrieve the stock market backend address from the modem. We hoped that it would be enough to exploit 0 day in PHP to bypass openbasedir and read the contents of the key in /home. But alas.
Correct answers: 0
Summary
51 participants were not able to answer a single question.
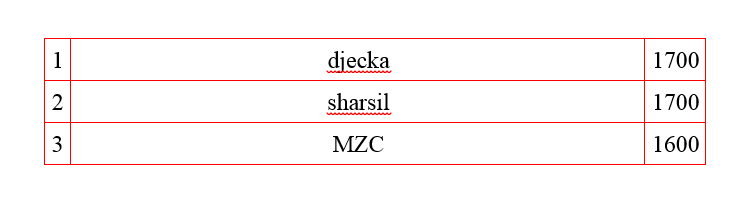
The first place went to djecka – he was the first one who managed to give right answers to 9 questions.
The top team was rdot — they cracked 12 tasks.