PHDays 8: hunting for IP camera zero-days at CAMBreaker
6/8/2018
More than 5,000 visitors came to Positive Hack Days this year, the majority of them security professionals. Their creativity and fine-tuned technical intuition were on full display in the hacking contests. CAMВreaker was no exception. In this article, we describe the preparations, techniques, and victors in this marathon of IP camera hacking.
At CAMBreaker, any visitor could try out the role of surveillance camera hacker by attempting to obtain unauthorized access to IoT devices and searching for vulnerabilities in firmware source code. Fun prizes awaited the most successful bug hunters!
Preparations for the contest began two months in advance. It was not easy by any means! This process consisted of several stages:
- Choosing which cameras to include.
- Checking the firmware versions, software, and operability of the cameras.
- Obtaining the firmware for each camera. Several methods were used:
- Intercepting firmware during camera updates via an Android app.
- Downloading firmware from the vendor's official site.
- Connecting to the device via Telnet.
- Connecting to the device via UART. This physical protocol (which stands for "universal asynchronous receiver transmitter") is rather old and the most widespread one in use today. The most well-known protocol in the UART family is RS-232 (commonly known as a COM port).
- Clipping a programmer to the flash chips inside the camera without de-soldering.
- And if all else fails, de-soldering the chips and reading them with a flash programmer.
- Configuring static IP addresses and credentials on the cameras.
- Designing and setting up a local network for the stand at PHDays.
- Setting up the stand in the demo environment.
Here are a few photos illustrating the work involved:

Extracting data from a chip with the help of a CH341A programmer

A camera motherboard

Flash programmer and friends :)
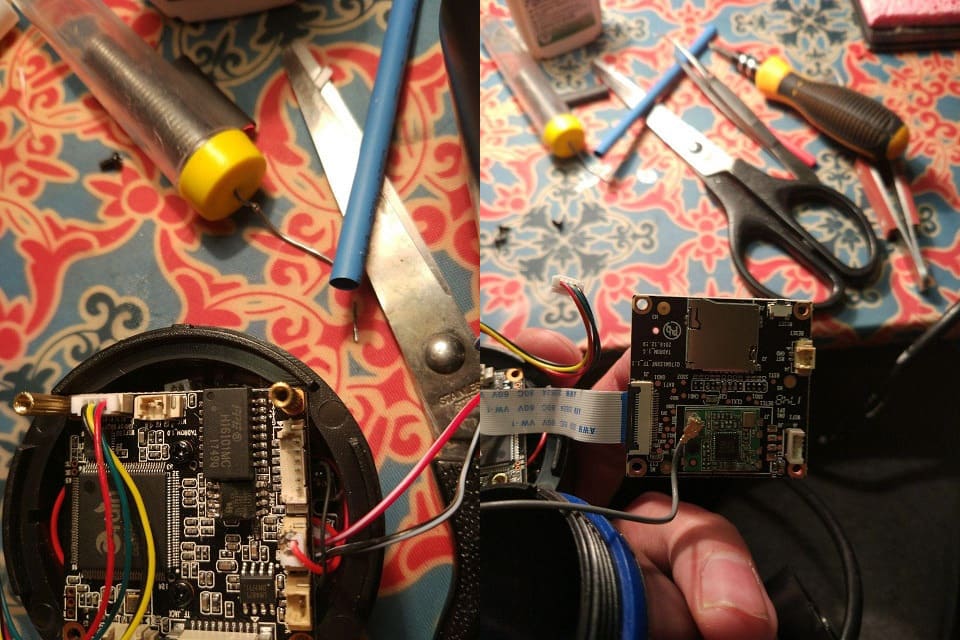
Some chips had to be de-soldered due to power circuitry
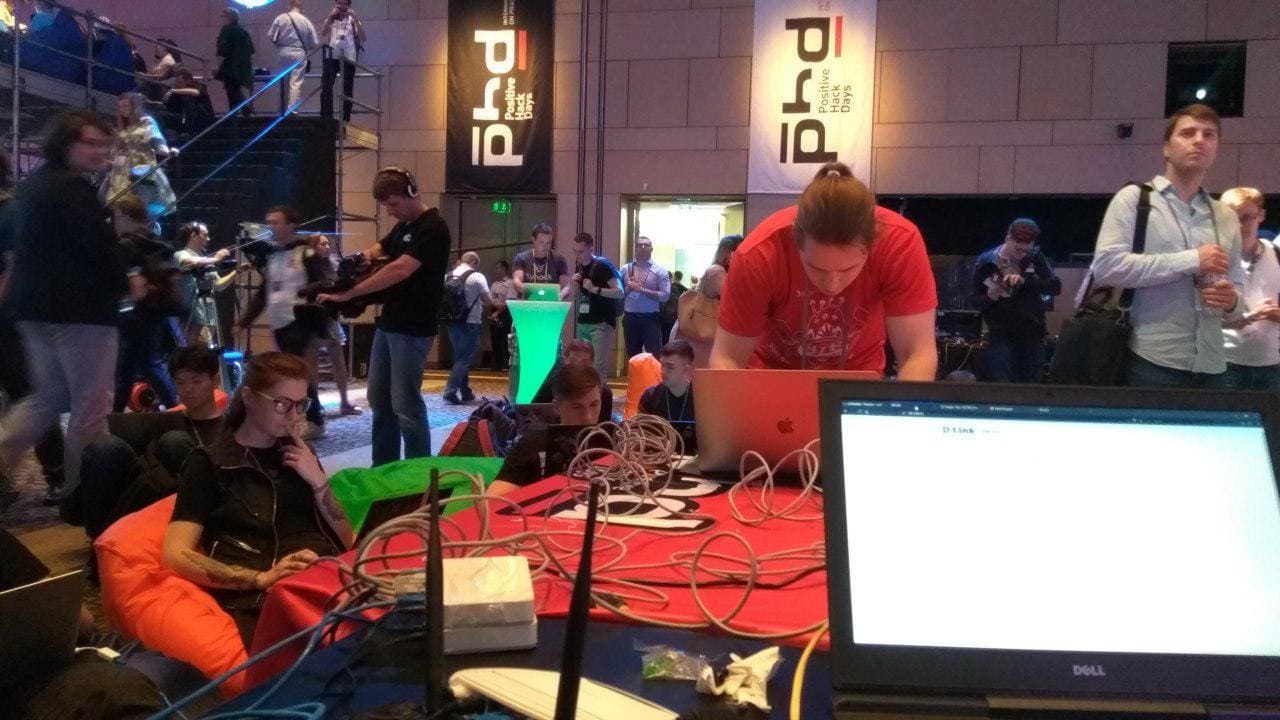
As for the stand, it consisted of 11 cameras and a handful of switches mounted for accessibility. Participants had access to a Wi-Fi network as well as a switch with patch cords for wired connections.

The stand

Big Brother watching you watch Big Brother
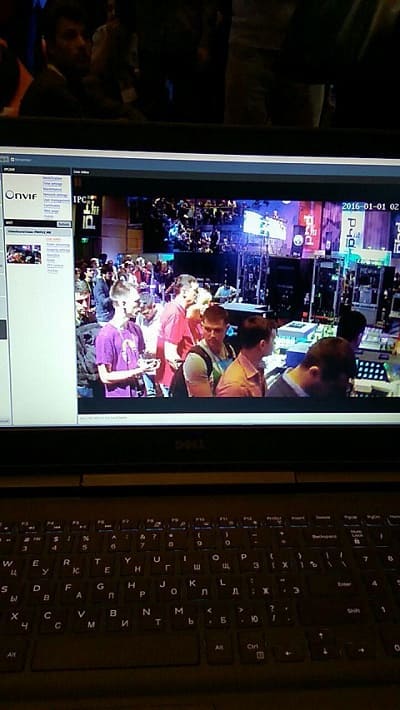
The router at the center of the network was running an FTP server, from which participants could download camera firmware. Information including camera addresses, credentials, and serial numbers was freely available to all.
Hackers @ work
Once on the network, participants could download firmware and get down to business
On the first day, the participants were given a tricky challenge: to find a vulnerability in a camera, plus write an advisory about exploitation of it or create a working proof-of-concept exploit. Unfortunately, many of the participants were spooked off by such requirements. But who said that winning a JTAGulator would be easy?
For the remaining time, hackers sat on their beanbag cushions and looked for firmware flaws. The firmware files were available from the local FTP server. The contest network lit up with hundreds of gigabytes of traffic as all sorts of tools were applied to the task: IDA Pro, Binwalk, Radare2, Strings, Wireshark, Tcpdump, Sqlmap, and Burp Suite, to name a few.
At the hacking-ist time of all—13:37—reinforcements arrived in the form of kegs of cold beer.

Refreshing beer on tap
Progress did not slow down after this top-up. In fact, the beer drew in several new participants and inspired them to join the effort. Still, no reports had been received by the end of the first day.


CAMBreaker participants
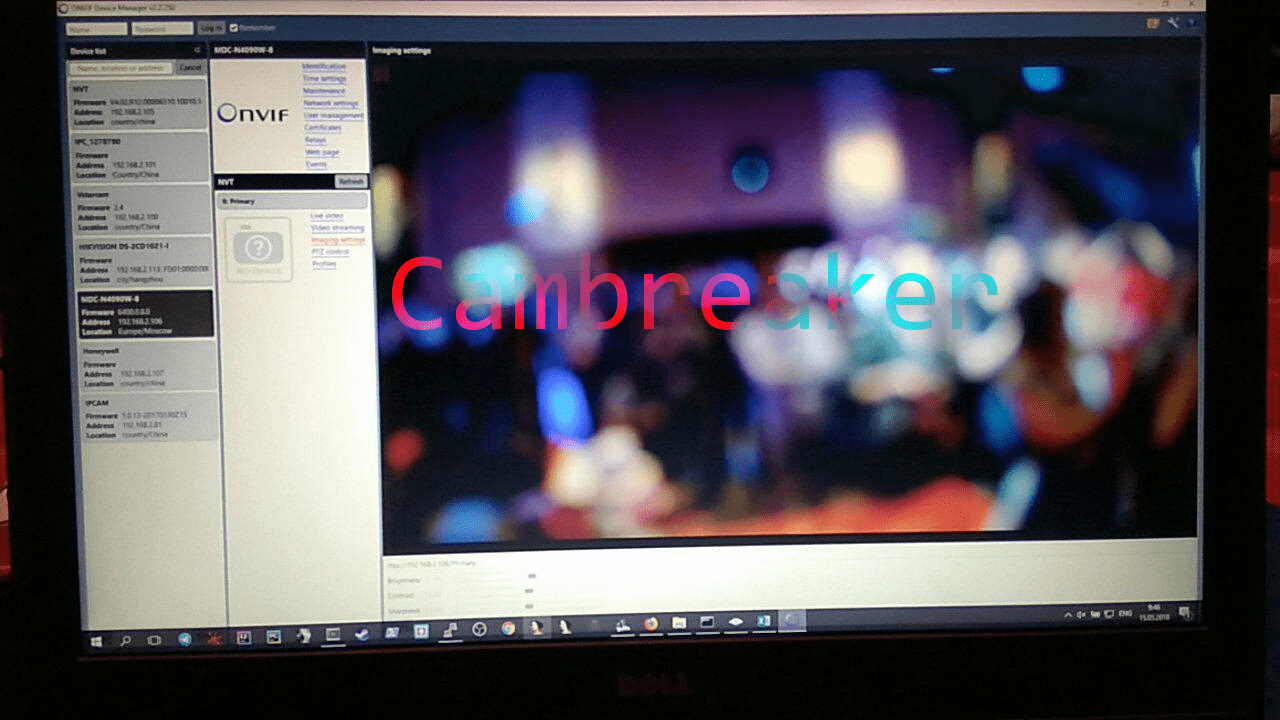
Two vulnerability reports came in early on the second day. The first, regarding the vstarcam-c16s camera, was found by Novosibirsk security specialist Pavel Cherepanov. The second vulnerability was discovered by Ivan Anisenya, another specialist. The web form for authentication on the MDC-N4090W-8 camera allowed blind SQL injection. As a result, an attacker could inject SQL commands with the id parameter and "blindly" extract (with a series of true-or-false questions) all of the device's usernames and passwords, including for the root user.
The camera vendors were informed of all discovered vulnerabilities. For the moment, the exploits all remain zero-days.
Pavel and Ivan received their well-deserved prizes.

Award ceremony for Pavel Cherepanov

Award ceremony for Ivan Anisenya (prize being received by Georgy Zaitsev in his place)